247CTF
@247CTF
🏆 The 247CTF continuous security competition
📺 YouTube for CTF fundamentals https://t.co/0RP7w5pej2
🏁 https://t.co/FATXT1bqrW for CTF challenges
ID:1113355705711386624
https://247CTF.com/ 03-04-2019 08:21:00
1,5K Tweets
5,2K Followers
92 Following

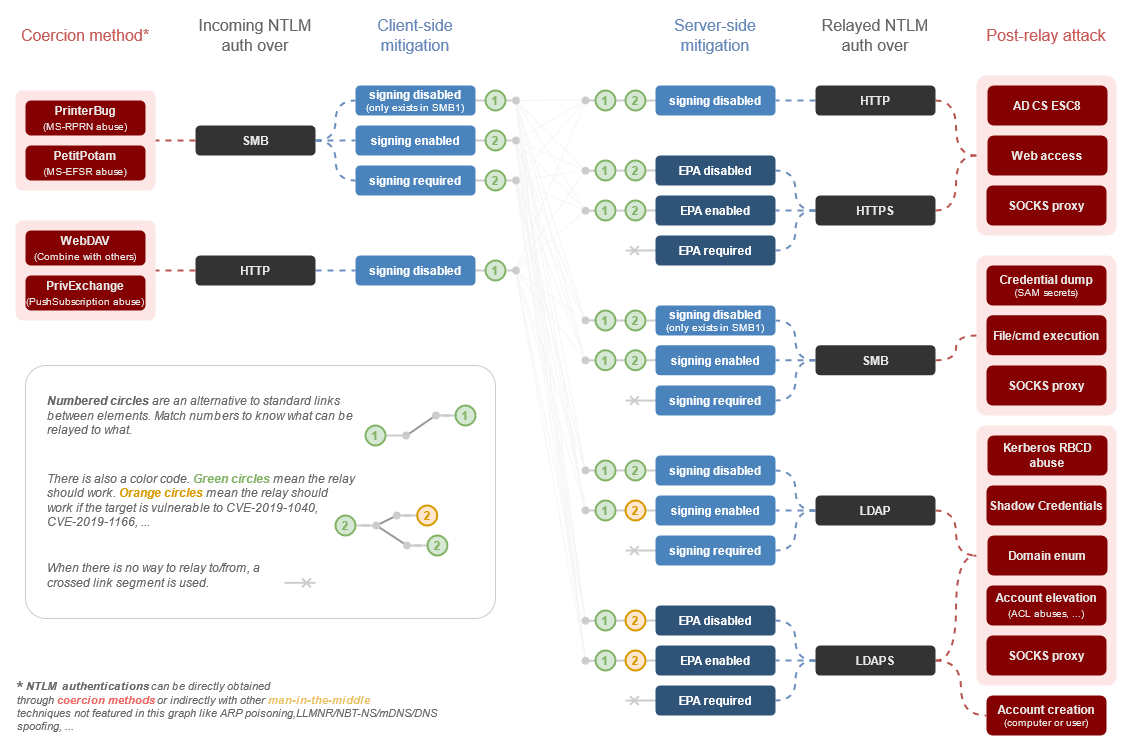
During a recent Active Directory intrusion test, Quentin Roland was led to devise a new versatile attack vector targeting Group Policy Objects, allowing their exploitation through NTLM relaying.
synacktiv.com/publications/g…



[BLOG]
Ok, I've written about my experience of battling with both managed and unmanaged memory allocations to try and improve b33f | 🇺🇦✊'s Melkor POC.
rastamouse.me/building-a-sli…


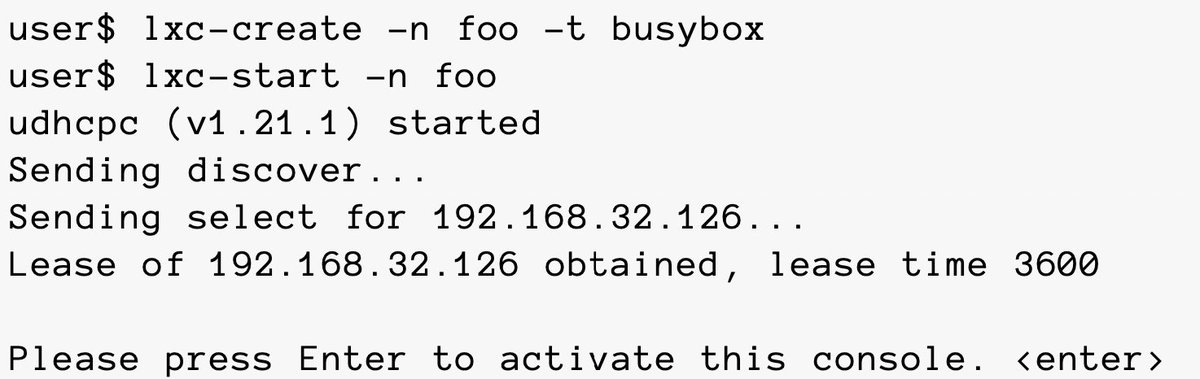
A few years old but a very well written white paper on Linux containers
Credits NCC Group plc
research.nccgroup.com/wp-content/upl…
#Linux #containers #infosec



Lee Chagolla-Christensen , Max Harley , and I are very proud to announce that the alpha release of Nemesis is now public! The code is at github.com/SpecterOps/Nem… and we have a post explaining details at posts.specterops.io/hacking-with-y… 1/3


When making the vulnerable #AWS environment CloudFoxable, Seth Art drew inspo from #security tools like #CloudGoat , flaws.cloud, and #Metasploitable . CloudFoxable provides flags and #attackpaths in a CTF format.
Check out the #challenges ! bfx.social/3X6diwX




Continuing their journey through offensive data, Will Schroeder, Lee Chagolla-Christensen, and Max Harley break down some common challenges in post-exploitation work flows. ghst.ly/45d5oF3