Adrian Grigorof
@AdiGri
CTO @ Managed Sentinel
ID:15334357
https://www.managedsentinel.com 06-07-2008 18:01:15
252 Tweets
435 Followers
122 Following

Segregation of access to logging data is a crucial topic that arises during Microsoft Sentinel architecture sessions. This blog post provides some of the common ways to implement it.
BlueVoyant #microsoftsentinel
managedsentinel.com/microsoft-sent…

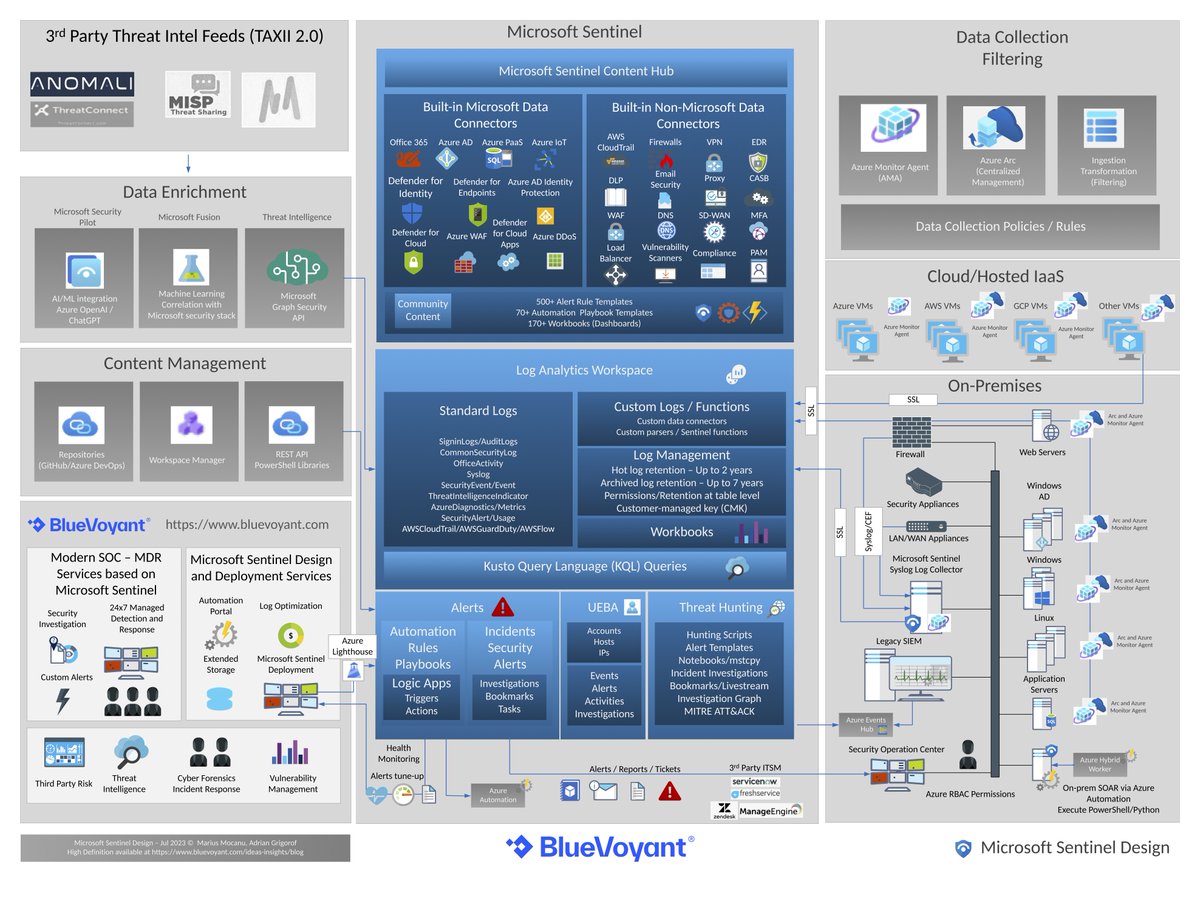
Microsoft Sentinel introduced a significant number of new features and improvements of existing ones since our last diagram update. This one page diagram attempts to cover the core components and the integration with log sources.
managedsentinel.com/microsoft-sent…
#microsoftsentinel #siem

2 new Microsoft Sentinel alert rule templates published:
- Workspace deletion activity from an infected device
- TI map IP entity to Network Session Events (ASIM Network Session schema)
#microsoftsentinel
BlueVoyant


2 new Microsoft Sentinel alert rule templates published:
#microsoftsentinel
BlueVoyant
Chia_Crypto_Mining IOC - June 2021
(Preview) TI map IP entity to DNS Events (ASIM DNS schema)

2 new Microsoft Sentinel alert rule templates published:
#microsoftsentinel
BlueVoyant
Front Door Premium WAF - SQLi Detection
Front Door Premium WAF - XSS Detection


2 new Microsoft Sentinel alert rule templates published:
#microsoftsentinel @bluevoyant
Guest accounts added in AAD Groups other than the ones specified
Guest accounts changed user type from guest to members in AzureAD

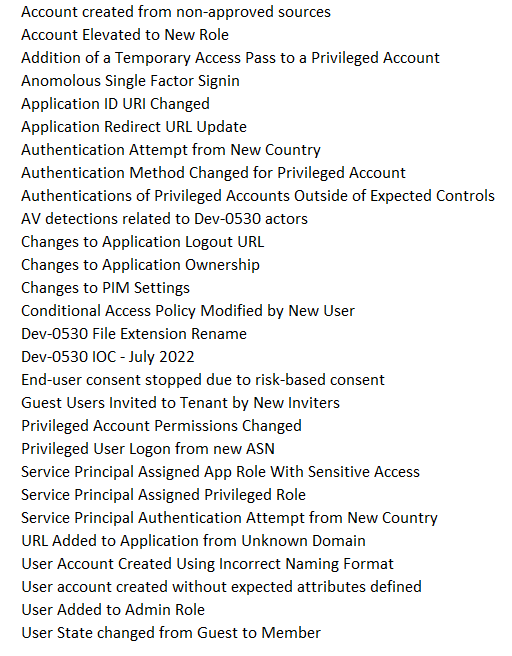
8 new Microsoft Sentinel alert rule templates published (471 in total):
#microsoftsentinel @bluevoyant



New Microsoft Sentinel alert rule template published:
AD FS Abnormal EKU object identifier attribute
Uses Security events from the AD FS Auditing provider to detect suspicious object identifiers as part event ID 501 (from the Enhanced Key Usage attributes).
#microsoftsentinel

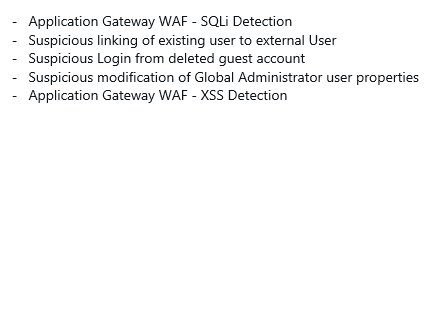
New Microsoft Sentinel alert rule templates published:
#MicrosoftSentinel BlueVoyant Managed Sentinel



New Microsoft Sentinel alert rule published:
Title: New External User Granted Admin
Description: This query will detect instances where a newly invited external user is granted an administrative role.
#microsoftsentinel

New Microsoft Sentinel alert rules published:
- PulseConnectSecure - CVE-2021-22893 Possible Pulse Connect Secure RCE Vulnerability Attack
- Hive Ransomware IOC - July 2022
- AV detections related to Hive Ransomware
#microsoftsentinel