DROL Security
@DrolSecurity
Not my Day Job
ID:700868921298124801
20-02-2016 02:25:47
18,0K Tweets
536 Followers
1,0K Following


Wrote a Keylogger in Rust that Bypasses Almost All AV Engines.
Code: github.com/Whitecat18/Rus…
#maldev #offensiverust #redteam #keylogger #rustlang #cybersecurity


New TCP Keylogger[Beta]: Now you can receive the logs directly from victim using receiver.
[+] TCP Keylogger: github.com/Whitecat18/Rus…
[+] TCP Receiver: github.com/Whitecat18/Rus…
#keylogger #maldev #pentesting #redteam #cybersecurity #hacking #pwned #infosec





The MITRE Corporation says state hackers breached its systems in January 2024 by chaining two Ivanti VPN zero-days - Sergiu Gatlan
bleepingcomputer.com/news/security/…

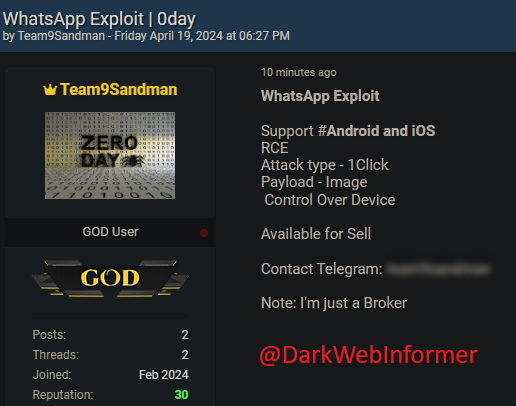
🚨URGENT🚨A Zero-day exploit for WhatsApp is up for sale.
#DarkWeb Informer #DarkWeb #Cybersecurity #Cyberattack #Cybercrime #Infosec #CTI #0Day #ZeroDay #WhatsApp #Exploit
Details:
- Supports #Android and iOS
- RCE
- Attack type - 1Click
- Payload - Image
- Control Over



Offensive Security OSCP, OSWP, OSEP, OSWA, OSWE, OSED, OSMR, OSEE, OSDA Exam and Lab Reporting / Note-Taking Tool
Source: github.com/Syslifters/Off…
#Hacking #infosec urity #infosec #Pentesting #redteam #pwn #CyberSecurity #CTF #CyberSecurity #cybersecuritytips

Vulnerability in Putty:
'attacker in possession of a few dozen signed messages and the public key has enough information to recover the private key'
* Revoke keys immediately including public in authorized_keys
* Generate a new key pair and replace
chiark.greenend.org.uk/~sgtatham/putt…




#BREAKING : US Gov't confirms Russia has cyber-hacked our own gov't *just a few days ago* (11 April).
#CISA reports the Russia-hacking operation, called Midnight Blizzard, successfully infiltrated our gov't by penetrating #MICROSOFT .
#Context : #Microsoft is the main provider of


![Mike Takahashi (@TakSec) on Twitter photo 2024-04-20 16:08:06 Google Dork - Login Pages 🔑 inurl:login | inurl:signin | intitle:login | intitle:signin | inurl:secure site:example[.]com Find hidden login pages and admin panels 👀 Google Dork - Login Pages 🔑 inurl:login | inurl:signin | intitle:login | intitle:signin | inurl:secure site:example[.]com Find hidden login pages and admin panels 👀](https://pbs.twimg.com/media/GLno7nwa0AAMGQM.png)