Adam
@Hexacorn
Red Brain, Blue Fingers
[email protected]
https://t.co/Bm0C9KQDDY
RIP Twitter
ID:456312508
http://www.hexacorn.com/blog/ 06-01-2012 03:26:37
6,3K Tweets
24,4K Followers
1,2K Following
Follow People







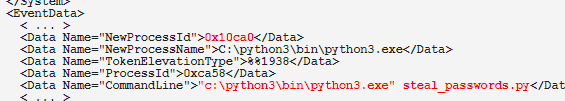
Dropping a new initial access technique via RDP that I dubbed 'Rogue RDP'. Use malicious .RDP files to bypass email/servers/security gateways and then run code to binary plant/exfil from your own RDP server, blinding EDR. Bonus: Target runs HyperV? RCE! blackhillsinfosec.com/rogue-rdp-revi…




smart as always from Cory Doctorow NONCONSENSUAL BLUE TICK on how closed platforms and social media companies screw over everyone, not just their users
pluralistic.net/2024/04/22/kar…