LiveOverflow 🔴
@LiveOverflow
wannabe hacker... he/him
🌱 grow your hacking skills @hextreeio
ID:3094698976
https://www.youtube.com/LiveOverflow 18-03-2015 14:33:53
8,3K Tweets
141,0K Followers
1,2K Following












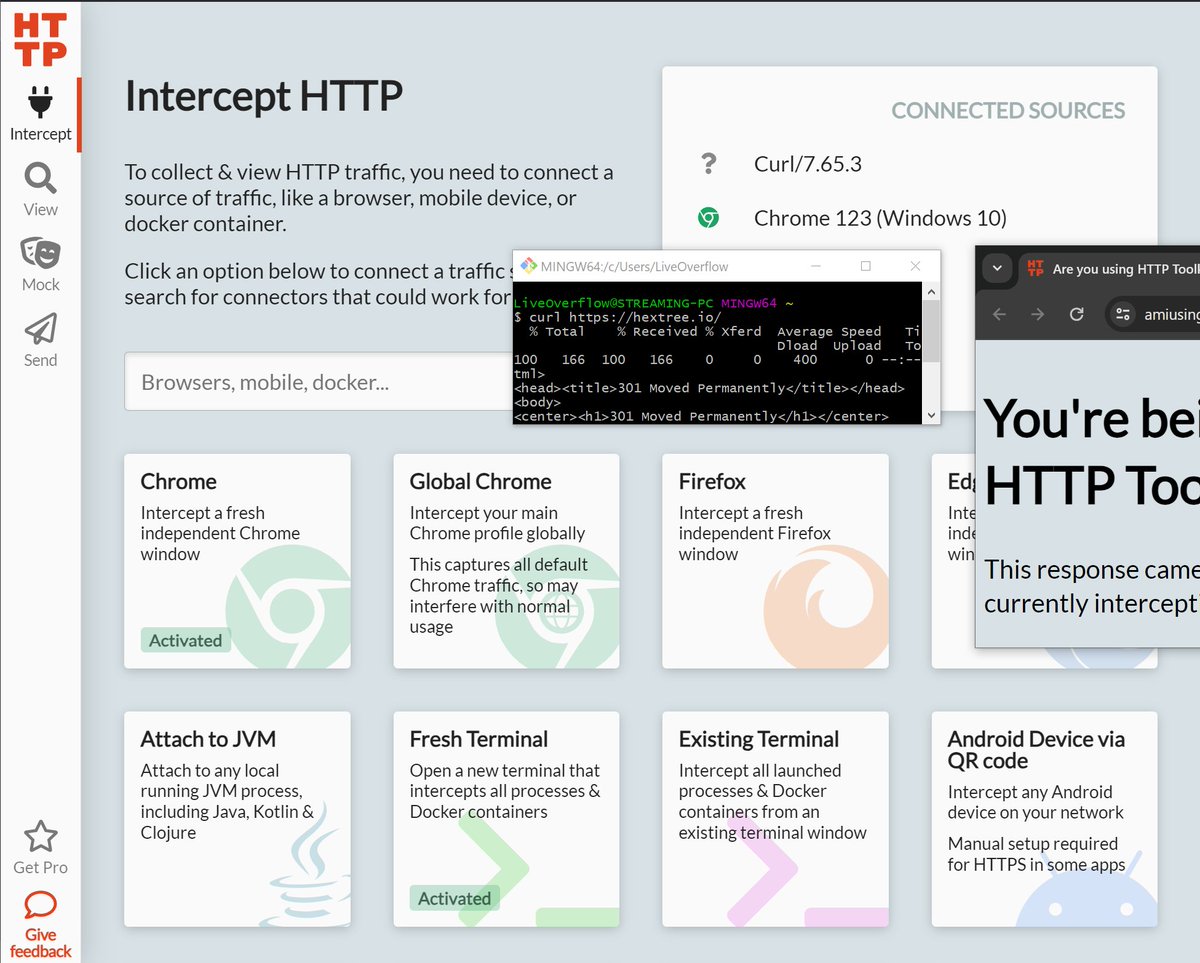
Shoutout to Tim Perry and HTTP Toolkit. Incredible convenient to quickly configure a proxy for various programs - including browsers, shells and Android.
Also great writeup about the technical details of the android interception changes in Android 14 🙇♀️
httptoolkit.com/blog/android-1…