Brandon Azad
@_bazad
ID:984632450629300224
https://github.com/bazad 13-04-2018 03:20:44
37 Tweets
15,3K Followers
0 Following




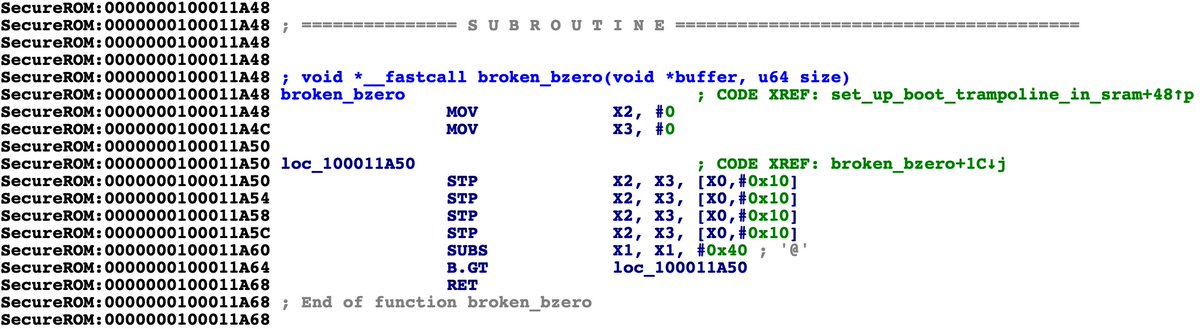
One Byte to Rule Them All: An iOS 13 exploit technique that turns a one-byte kernel heap overflow into an arbitrary physical address mapping primitive, all while avoiding the kernel task port and sidestepping mitigations like PAC, KASLR, and zone_require.
googleprojectzero.blogspot.com/2020/07/one-by…


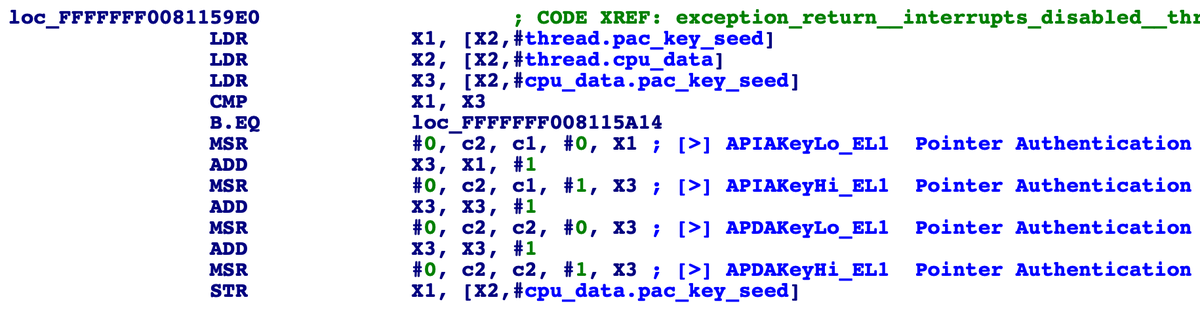
New blog post on how I was able to find the 0-day used in unc0ver just 4 hours after it was released: googleprojectzero.blogspot.com/2020/07/how-to…
Key takeaways:
1. Obfuscating an exploit doesn't hide the bugs.
2. Like SockPuppet, this bug could have been identified with simple regression tests.



Here are slides and recordings from 36C3 and OBTS.
36C3 slides: bazad.github.io/presentations/…
video: media.ccc.de/v/36c3-10806-k…
OBTS slides: bazad.github.io/presentations/…
day 2 stream: youtube.com/watch?v=ZDJsag…
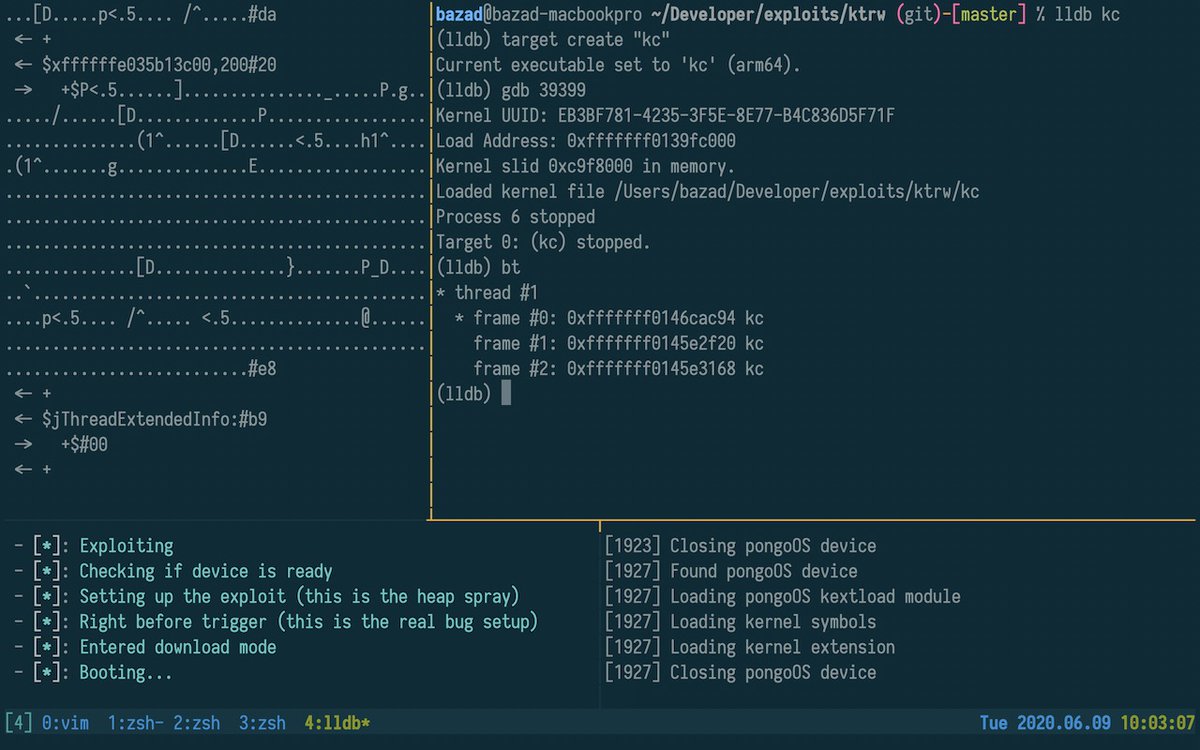
In the OBTS live demo I showed how I used KTRW to discover the oob_timestamp bug.