AMol NAik
@amolnaik4
CISO | Ex-Gojek | Startup Security | Vulnerability Researcher | Bodhi (https://t.co/IOJjeRGHNc) | Likes are bookmarks | Opinions are my own
ID:99859721
http://amolnaik4.blogspot.com 28-12-2009 04:25:50
5,8K Tweets
3,4K Followers
386 Following














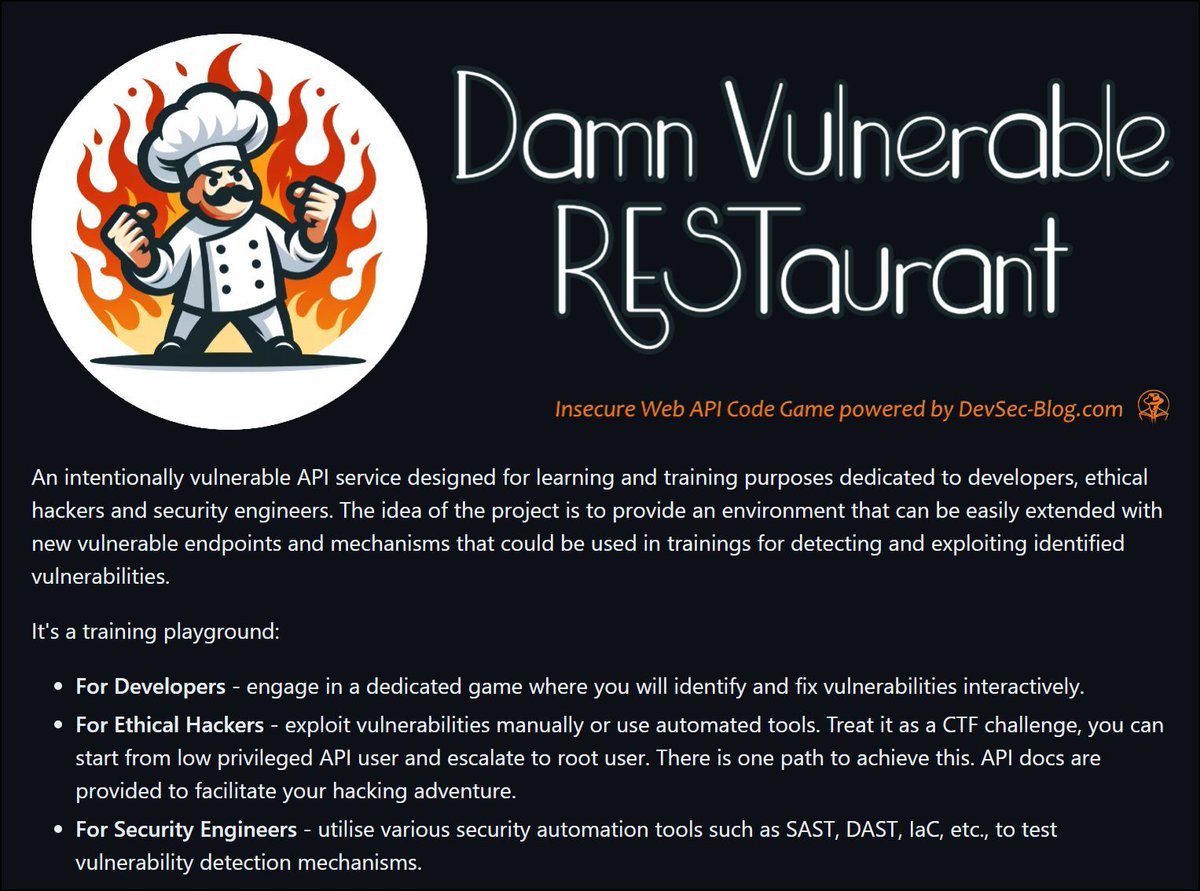
𝗗𝗮𝗺𝗻 𝗩𝘂𝗹𝗻𝗲𝗿𝗮𝗯𝗹𝗲 𝗥𝗲𝘀𝘁𝗮𝘂𝗿𝗮𝗻𝘁 - is an intentionally vulnerable Web API game for learning and training purposes dedicated to devs, ethical hackers, and security engineers.
Blog: buff.ly/3vAM9Jh
Repo: buff.ly/3J2xjhT
#CyberSecurity


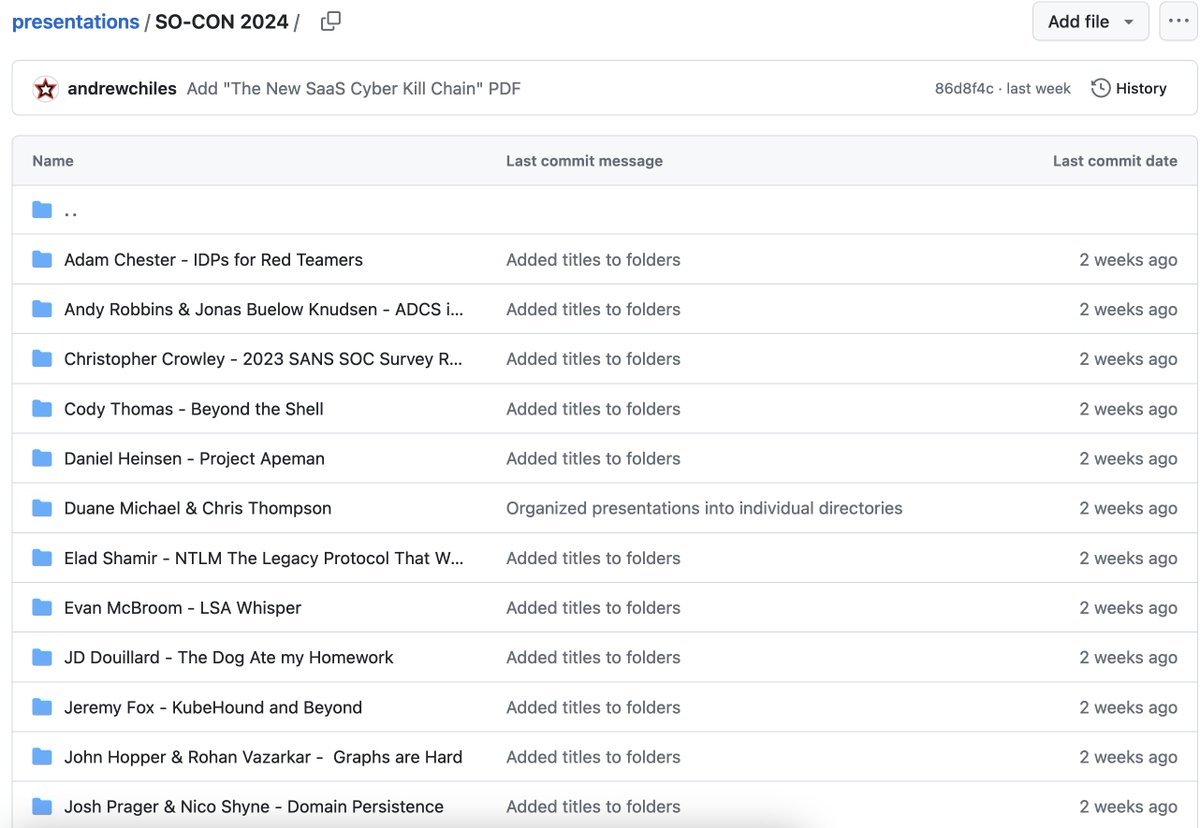
👥 SO-CON 2024 slides are now available
SpecterOps 🇺🇦's conference, with a big focus on graph based defense
I found a few particularly interesting:
Elad Shamir on NTLM security
Luke Jennings on the SaaS kill chain
Daniel Heinsen on AWS identity attack paths
github.com/SpecterOps/pre…