Jorge Orchilles
@jorgeorchilles
SANS Principal Instructor & Author #SEC565 | #RedTeam | #PurpleTeam | #PenTest | #C2Matrix Creator | ATT&CK & Atomic Red Team Contributor | Published Author
ID:19165893
https://www.orchilles.com 19-01-2009 01:32:48
13,8K Tweets
11,1K Followers
468 Following

Looking for effective ways to support the decision-making process of your stakeholders? My friend Aperture and Noise & I presented about this topic, specifically by utilizing 'attack trees', at this weeks FIRST CTI Conference.
Slides are now available via: github.com/gertjanbruggin…



Join us at #SANSAiForum on Thursday, April 25 when Jorge Orchilles & Tim Schulz will share strategies, tips, and quick wins for how to start building an #AI Red Team.
➡️ Register for Free: sans.org/u/1uVn
#ReadTeam #PenTest


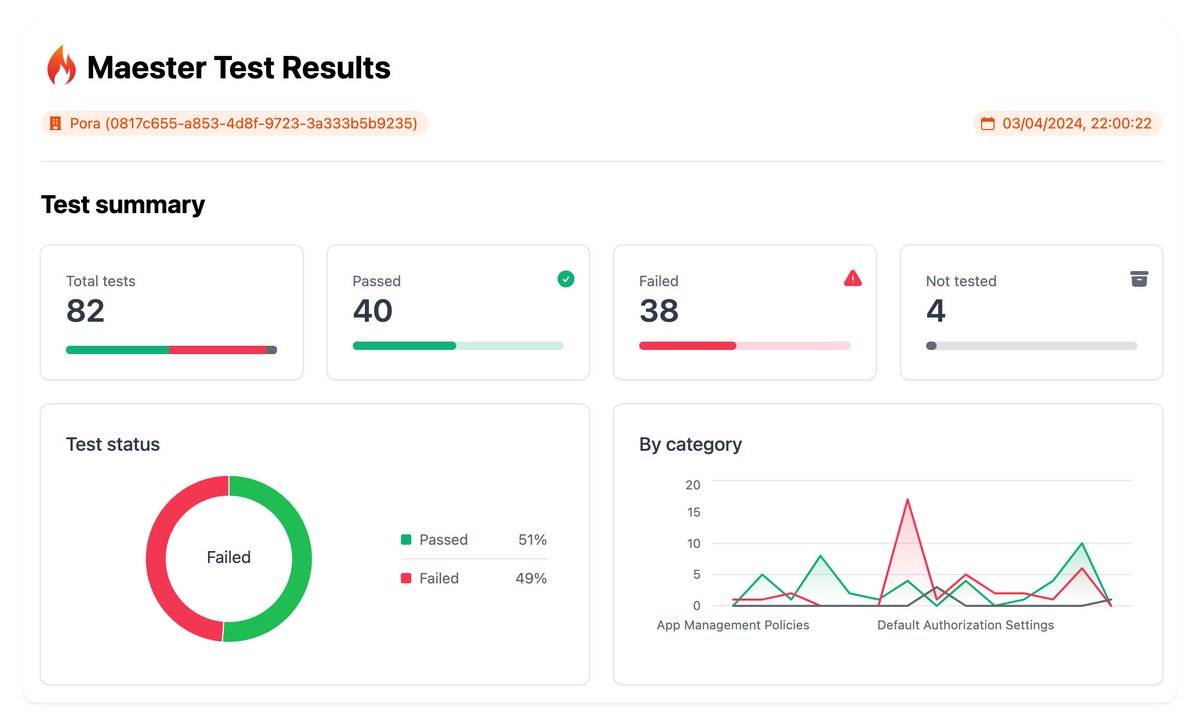
🥳 🎉 Folks, Fabian Bader, Thomas Naunheim & I are excited to launch Maester today after working on this over many long nights & weekends!
Maester is an open source, test framework that you can set up in minutes to test & continuously monitor your Microsoft security config
🧵⬇️


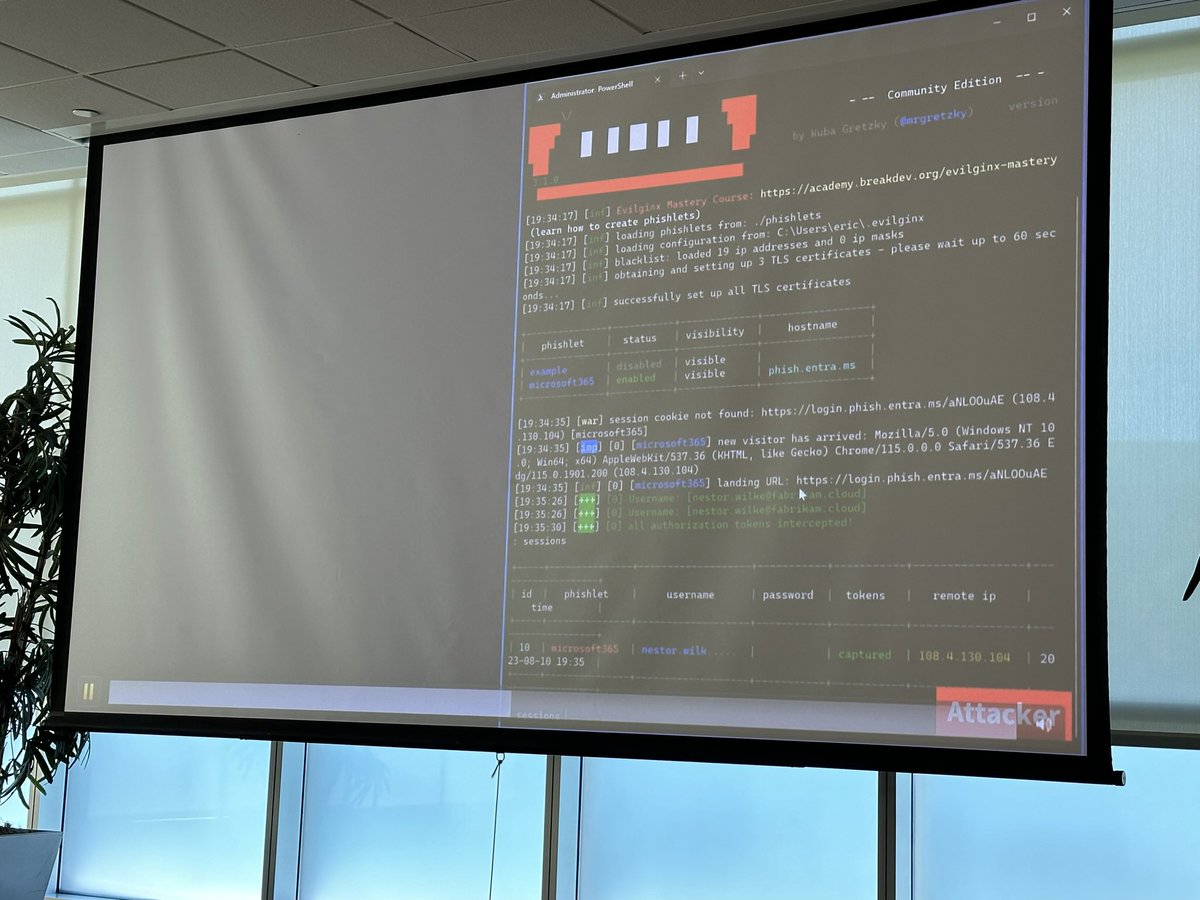
Spotted B-Sides Tampa IT Security Conference Learning some more Azure stuff with Christopher Peacock and a nice little demo Kuba Gretzky may recognize the tool





I should have stayed up for this race! My fantasy team did terrible but how about Ferrari!!!!! #InfoSecF1



These terms are often conflated and it seems like more people just lump any type of “hacking” activity into “red”.
Jorge Orchilles did a write-up explaining the difference: sans.org/blog/shifting-…



I'm thrilled to let you know that the agenda for the SANS Faculty Led event is now available. #SANSAIForum Mick Douglas 🇺🇦🌻 david_hoelzer @[email protected] Jess Garcia sethmisenar Jorge Orchilles Looking forward to hosting these talks on the forum on April 25. Register now!


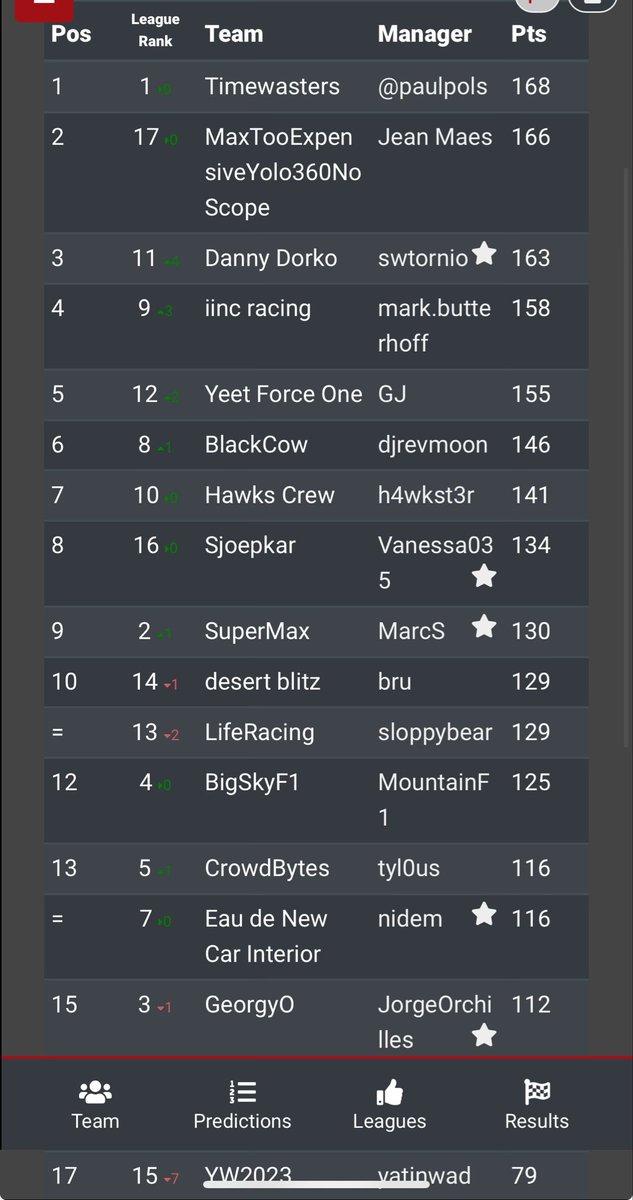
2nd race of the 2024 season in the books with Christopher Peacock taking P1. Paul Pols and I sharing the podium with him. Paul manages to hold on to the lead but a long way to go with 22 more races this season! #InfoSecF1