Luan de Mattos
@luan_demattos
Cybersecurity Analyst | Reverse Engineering and Malware Analysis Enthusiast.
Tweets are my own.
ID:301388269
19-05-2011 11:39:03
523 Tweets
183 Followers
1,0K Following








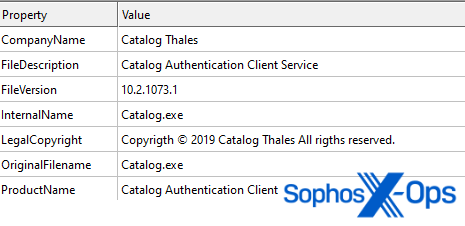
A security backdoor was recently discovered in liblzma 5.6.0 and 5.6.1. #Wireshark 's Windows and macOS installers ship with liblzma, but not with those versions.


Here is my #Friday #giveaways !
Like, retweet and share with your network... I'll randomly choose on Monday 4/1 two winners to get the full 'C5W Certified Malware Analysis' course and certification for FREE... You should not miss this! #DFIR #Malware
academy.cyber5w.com/courses/C5W-Ce…




Check out the recorded Off By One Security stream with Duncan Ogilvie 🍍 !! The slides and files used for debugging are available in the video description. Thanks again for joining as a guest, Duncan!
youtube.com/watch?v=AKcADa…




Join us this Friday at 11AM PT with Kuba Gretzky as he shares with us his latest work on Evilginx and MFA bypasses!
We will be giving away THREE free seats to Kuba's 'Evilginx Mastery' course! For those who don't win, we'll provide a 20% discount code!
youtube.com/watch?v=bomHX1…

🔥 #BinaryNinja 4.0 is now out, this includes a new FREE edition :) Definitely worth checking out, especially if you aren't a current user 👇
binary.ninja/2024/02/28/4.0…
Other updates: projects, UI overhaul, support for Windows kernel debugging, and a new Types view, to name a few