Herbie Zimmerman
@HerbieZimmerman
SOC analyst and wanna-be malware researcher.
ID:982533264
https://www.herbiez.com 01-12-2012 13:26:30
3,3K Tweets
2,5K Followers
962 Following









New blog post from Mohamed Ashraf and me. Where we did a deep dive into a recent KamiKakaBot sample we encountered.
Unveiling KamiKakaBot – Malware Analysis nextron-systems.com/2024/03/22/unv…
Nextron Systems


Looking for a fun #CyberSecurity #Infosec project? 😁
Want to practice your #ThreatHunting 🔍 and #Detection 🕵️ skills?
Install the NEW #SecurityOnion 🧅 2.4.60 in a VM:
docs.securityonion.net/en/2.4/first-t…
Then follow along with some of our quick #malware analysis posts:…



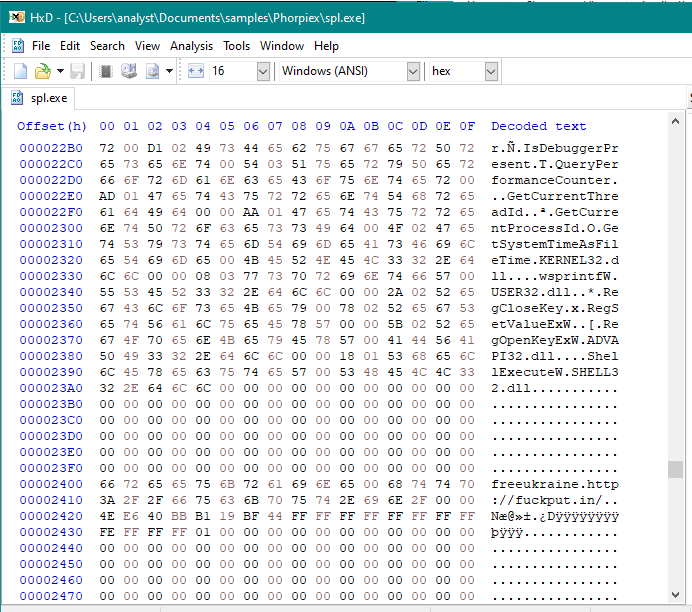
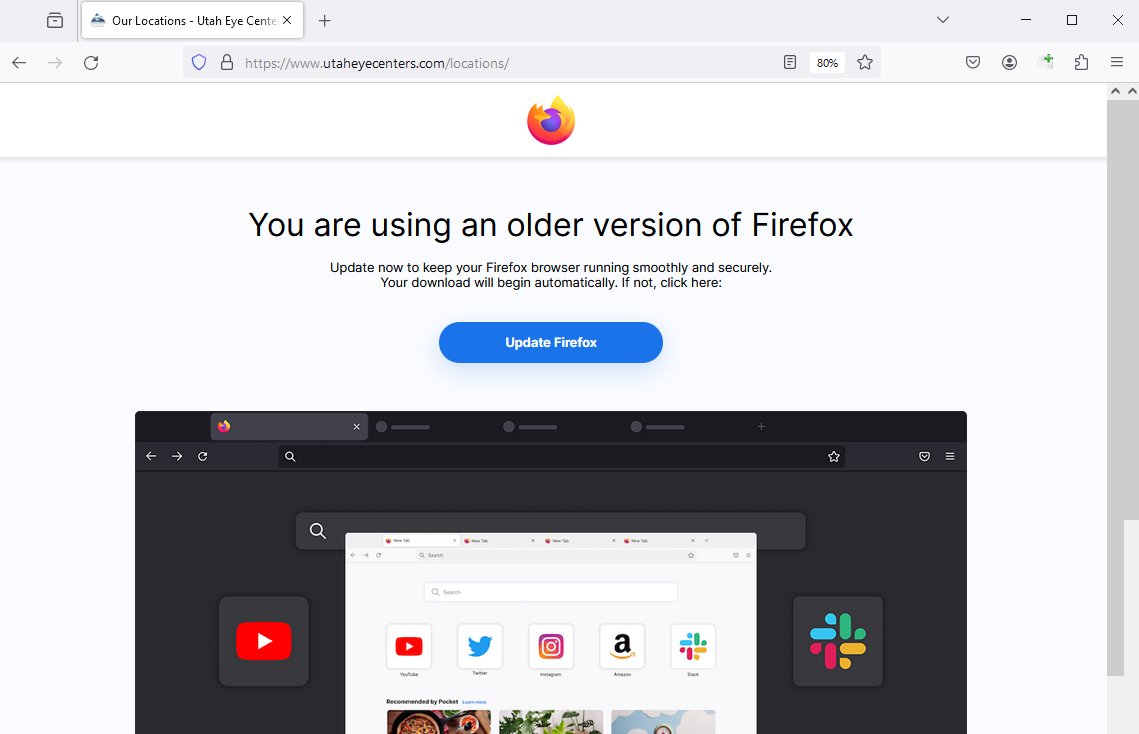
Been a while since I came across #SocGholish , but saw the update.js come from hxxps://invisiblepeople[.]tv/why-i-support-regulating-the-public-feeding-of-homeless-people/<...>. Couldn't pull the file unfortunately.
urlscan.io/result/2857487…




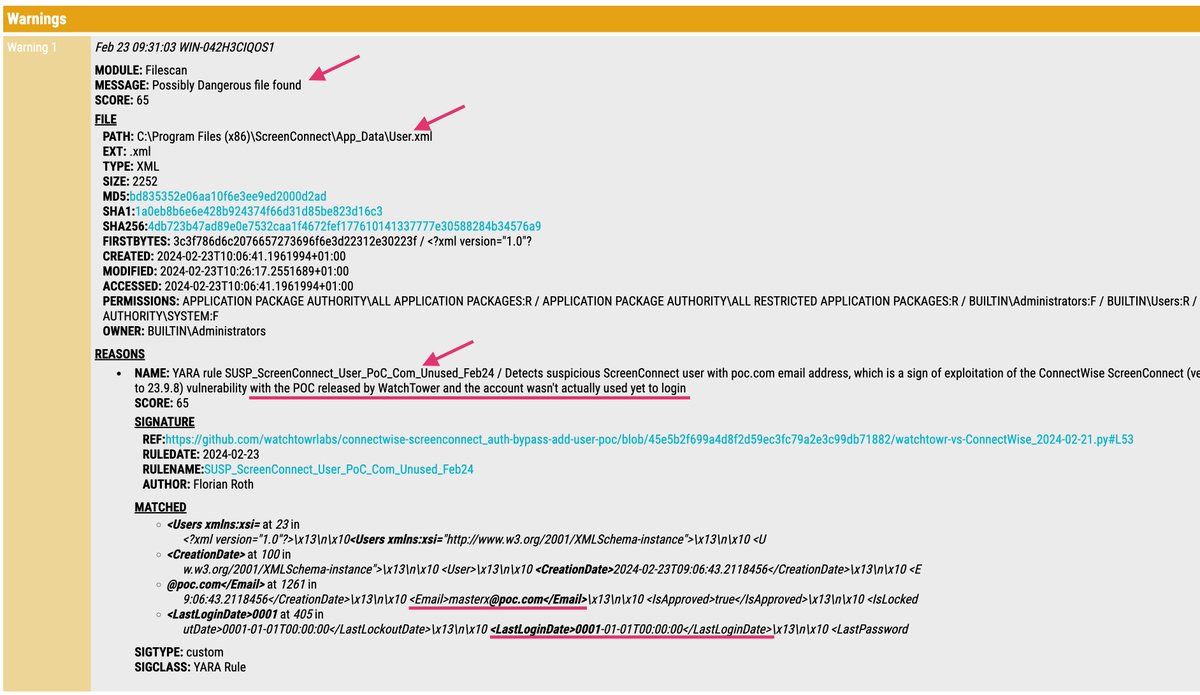
I've processed Huntress' awesome report on post-exploitation activities observed in relation to the #ScreenConnect vulnerability and created 15 YARA rules
Report
huntress.com/blog/slashandg…
Rules
github.com/Neo23x0/signat…
(I've put the THOR APT Scanner only rules at the end)
IOCs…