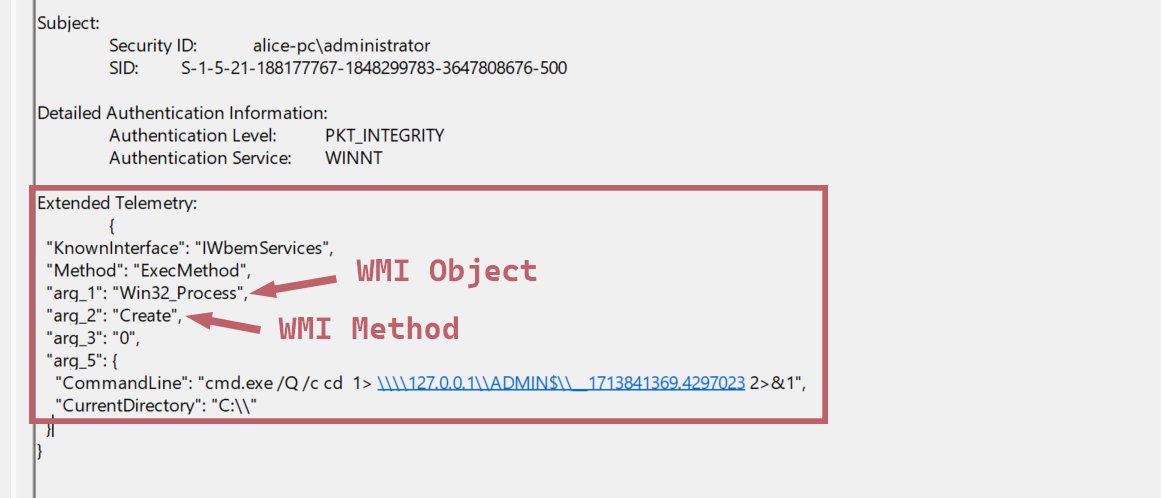
As a DFIR Engineer, you should notice something suspicious going on here!!
But how many techniques do you know that an attacker can use to hide this easy detection from you?!
#C5W #DFIR #Malware #ThreatHunting #Cybersecurity



We published #korean version's report '2023 ACTIVITIES SUMMARY OF SECTORB GROUPS REPORT' tinyurl.com/yb9k5ujm #APT #Malware #cybercrime #threatintel #ThreatIntelligence #threathunting #phishing #vulnerability

.Jess Garcia is here to cover what you need to know to integrate #GenAI into your everyday #DFIR tasks.
Register for Free & Join Here: sans.org/u/1uVn
#SANSAiForum #DigitalForensics #IncidentResponse #ThreatHunting #AI

Learn how #Edgewater 's team of experts works together to review the data, share insights, and develop strategies for improving our Federal client's security posture. edgewaterit.com/2024/05/02/thr…
#EFS #Edgewater Cyber #ThreatHunting #MidnightBlizzard #ATPs #Cybersecurity #CyberDefense


In the latest episode of the Adversary Universe podcast, CrowdStrike's Andrew Munchbach breaks down the concept of OODA in #ThreatHunting .
1️⃣ Observe what's happening
2️⃣ Orient yourself around what's happening
3️⃣ Decide
4️⃣ Act
🎧 Full episode on Spotify: crwdstr.ke/6018jrWwj


In the latest episode of the Adversary Universe podcast, CrowdStrike's Andrew Munchbach breaks down the concept of OODA in #ThreatHunting .
1️⃣ Observe what's happening
2️⃣ Orient yourself around what's happening
3️⃣ Decide
4️⃣ Act
🎧 Full episode on Spotify: crwdstr.ke/6014bNYem

In the latest episode of the Adversary Universe podcast, CrowdStrike's Andrew Munchbach breaks down the concept of OODA in #ThreatHunting .
1️⃣ Observe what's happening
2️⃣ Orient yourself around what's happening
3️⃣ Decide
4️⃣ Act
🎧 Full episode on Spotify: crwdstr.ke/6012b0aRm

In the latest episode of the Adversary Universe podcast, CrowdStrike's Andrew Munchbach breaks down the concept of OODA in #ThreatHunting .
1️⃣ Observe what's happening
2️⃣ Orient yourself around what's happening
3️⃣ Decide
4️⃣ Act
🎧 Full episode on Spotify: crwdstr.ke/6016b0aM8

In the latest episode of the Adversary Universe podcast, CrowdStrike's Andrew Munchbach breaks down the concept of OODA in #ThreatHunting .
1️⃣ Observe what's happening
2️⃣ Orient yourself around what's happening
3️⃣ Decide
4️⃣ Act
🎧 Full episode on Spotify: crwdstr.ke/6012bauwI

In the latest episode of the Adversary Universe podcast, CrowdStrike's Andrew Munchbach breaks down the concept of OODA in #ThreatHunting .
1️⃣ Observe what's happening
2️⃣ Orient yourself around what's happening
3️⃣ Decide
4️⃣ Act
🎧 Full episode on Spotify: crwdstr.ke/6010jHPcY

In the latest episode of the Adversary Universe podcast, CrowdStrike's Andrew Munchbach breaks down the concept of OODA in #ThreatHunting .
1️⃣ Observe what's happening
2️⃣ Orient yourself around what's happening
3️⃣ Decide
4️⃣ Act
🎧 Full episode on Spotify: crwdstr.ke/6010jDoCa

In the latest episode of the Adversary Universe podcast, CrowdStrike's Andrew Munchbach breaks down the concept of OODA in #ThreatHunting .
1️⃣ Observe what's happening
2️⃣ Orient yourself around what's happening
3️⃣ Decide
4️⃣ Act
🎧 Full episode on Spotify: crwdstr.ke/6010jBTfi

Dive deep into #cybersecurity with our hands-on #training by 0xbad53c and Thomas Eugène! Join red and blue teams in live attack-defense exercises against simulated APT 0x00. Learn #ThreatHunting , #DetectionEngineering , and #IncidentResponse techniques 🛡️
x33fcon.com/#!t/DennisVanE…