Lennert
@LennertWo
PhD Researcher @CosicBe | Hardware Security
@[email protected]
ID:322560263
23-06-2011 11:16:07
401 Tweets
3,8K Followers
1,4K Following

A team of security researchers have revealed to WIRED's Andy Greenberg (@agreenberg at the other places) a lock hacking technique that impacts millions of locks in thousands of hotel properties across 131 countries.
They call his hack Unsaflok. Read the full story here: wired.com/story/saflok-h…






A Starlink User Terminal is a dish best served reversed and that is exactly what Carlo Ramponi did for the past 6 months.
Here he shares his journey and the tools he built during his internship at Quarkslab.
Dive deep into Starlink's UT firmware!
blog.quarkslab.com/starlink.html



'A popular Bluetooth car battery monitor app sends GPS, cell phone tower cell IDs and Wifi beacon data to servers in Hong Kong, mainland China.'
Most apps are actively adversarial to users. Need much stronger permissions protections from operating systems.
doubleagent.net/2023/05/21/a-c…

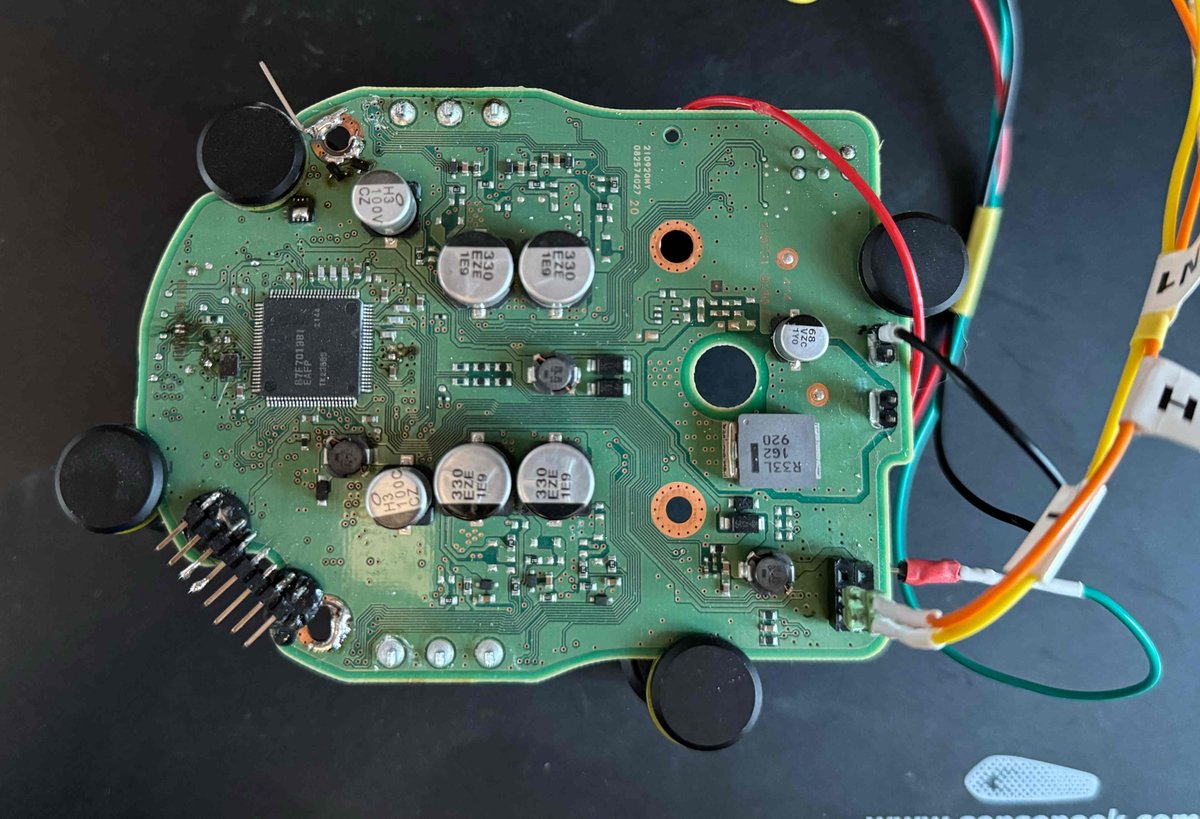
We (Lennert, rqu and me) just demonstrated some nice bugs we found in the Google Nest Wifi Pro & Chromecast to the Google VRP (Google Bug Hunters) team at hardwear.io

It's ShowTime! We discovered how to mount CPU timing attacks with... the human eye? 👀
How? Find out in our (w/ marton bognar) new paper 'ShowTime: Amplifying Arbitrary CPU Timing Side Channels'.
To appear at AsiaCCS '23: antoonpurnal.github.io/files/pdf/Show…


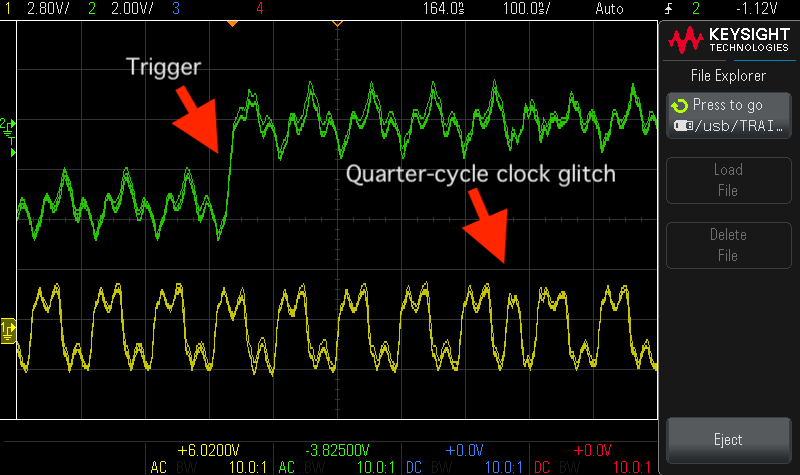
Clock glitching an STM32F042 with nothing but a Raspberry Pi Pico😎🥳
Thanks to PIO it's trivial to achieve 32MHz with 1/4 width clock glitches. With overclocking more than double that is possible!

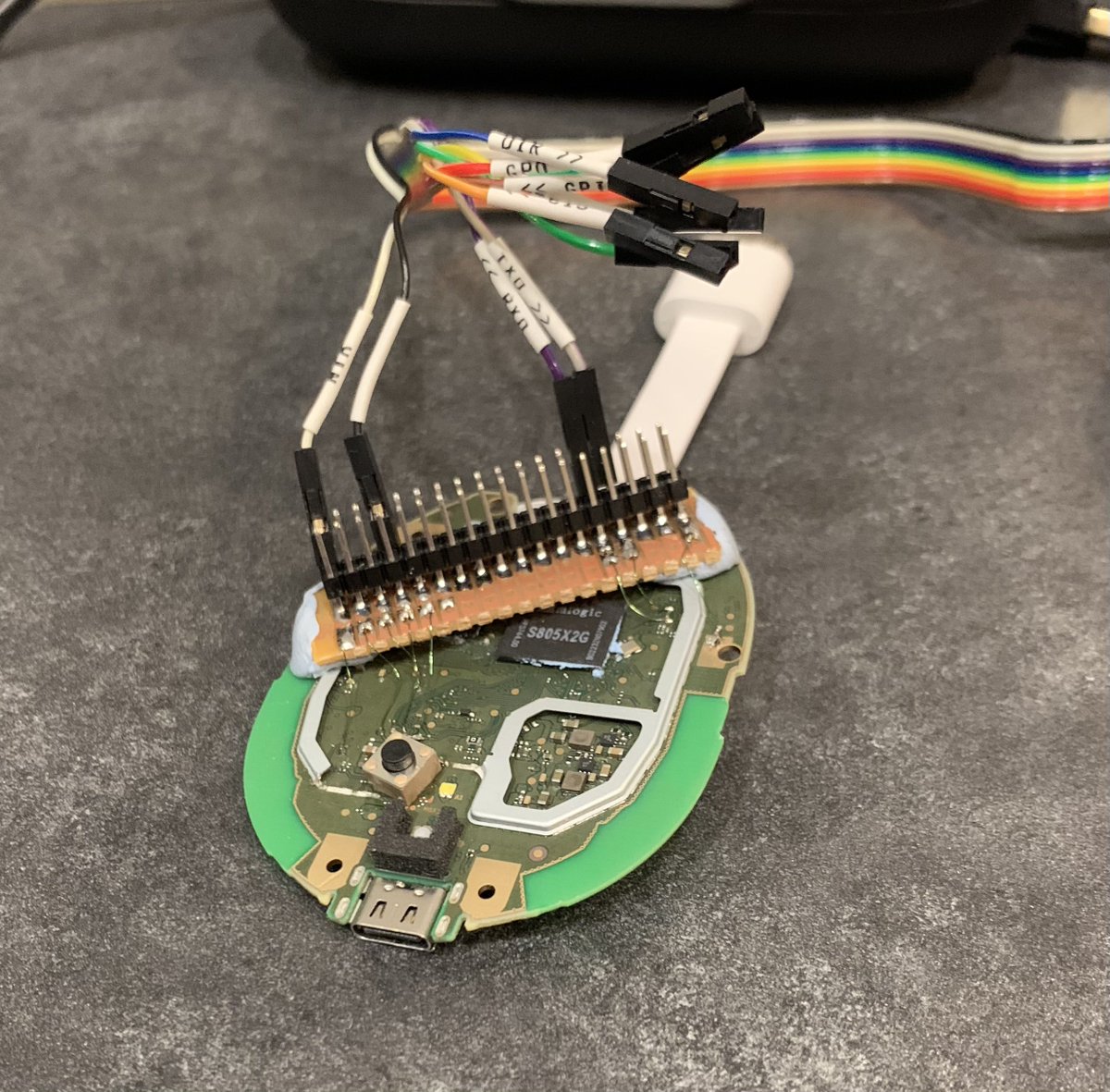
So I'm sure all are aware my RAV4 was stolen last year, ironically via 'CAN Injection 🚘💉'. Myself and Ken Tindell 🌻 🐘 [email protected] have been reverse engineering the device that I beleive was used for the theft. More details are on his blog kentindell.github.io/2023/04/03/can…



📡Showcase your cutting edge #hardwaresecurity research with the World to help build a safer 📟 #connected future
😎We are looking out for your uber cool research here➡️bit.ly/3hyPIIy
#hw_ioUSA2023 #CFP #embedded #callforpapers @[email protected] #hardwarehacking