
The DFIR Report
@TheDFIRReport
Real Intrusions by Real Attackers, the Truth Behind the Intrusion.
Services: https://t.co/XW613EKt2w
ID:1245886895458078722
https://thedfirreport.com/ 03-04-2020 01:33:43
1,2K Tweets
52,5K Followers
0 Following


At The DFIR Report we try to get information across in multiple ways. One of them is the introduction of a podcast, to add to each report. Here analysts discuss whats on their minds and what context might not be in the report. After the success of the first podcast, here is #2 :)

Today's Training Tuesday Highlight is The DFIR Report
They provide FREE detailed DFIR Reports on their website that you can learn from: thedfirreport.com
They also recently launched DFIR labs where you can get hands-on access to to report data. You also get CPE credits, a…


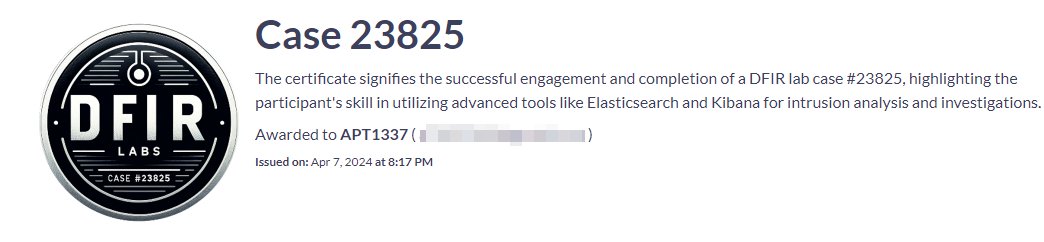
Fun times beta testing The DFIR Report new lab training platform! I love to see them turning their articles into hands-on, interactive learning experiences. api.badgr.io/public/asserti…

Just want to express my appreciation to the team at The DFIR Report for their dedication to putting this together. I'm not sure if I enjoyed the struggle of squinting my eyes out looking through thousands of logs, but it is real, and if you plan to be a defender and handle…

Finished the lab of BlueSky Ransomware from The DFIR Report Great learning journey and experience by analyzing the real-world intrusion logs and building query skills with Elasticsearch and Kibana. Appreciate their excellent work!


SUPER neat opportunity to really touch the reporting we 💙
Thanks The DFIR Report 🫡🥂
the-dfir-report-store.myshopify.com/collections/df…



Interesting #CobaltStrike server:
➡️canarapay-f5agf9ccgteqbpg2[.]z03[.]azurefd[.]net
➡️Using Azure Front Door
➡️Staged/backend on Digital Ocean (AS14061)
➡️URIs: /safebrowsing/
➡️Spawn: WerFault.exe
More info available in our AllIntel service @ thedfirreport.com/services/threa…


If you are in infosec and are NOT reading reports from The DFIR Report you are missing out!
Talk about the most ACTIONABLE and PRACTICAL information.
The amount of time and research that goes into these reports 🔥
And they are free 💜
