
Duane Michael
@subat0mik
Adversary Simulation Operator, Researcher, Teacher, Leader @SpecterOps
ID:994808635812347904
11-05-2018 05:17:16
446 Tweets
854 Followers
464 Following

It's a big day- Lee Chagolla-Christensen, Max Harley, and I are proud to announce that Nemesis 1.0.0 has landed! We have a ton of awesome new features and a streamlined installation, check out the details at posts.specterops.io/nemesis-1-0-0-… and the code at github.com/SpecterOps/Nem…

Heading to #MMSMOA next month? Make sure to add this session to your schedule. Chris Thompson will be joining Kim Oppalfens (MVP) ✖️ & Tom Degreef to speak on how to secure your ConfigMgr environment & defend against publicly known attacks.
Learn more ➡️ ghst.ly/4459csL #SCCM




Identify every TAKEOVER and ELEVATE attack in Misconfiguration Manager.
Check out our latest blog post from Chris Thompson to learn more about the MisconfigurationManager.ps1 script that will quickly identify risky configurations worth looking into further. ghst.ly/4aQLWAF

This PowerShell script is a quick way to audit your SCCM configuration to determine whether you have unidentified/unnecessary risks. Great stuff from Chris Thompson!

Chris Thompson did some awesome work with this! Find out where you may be at risk with SCCM with this one simple trick




Something cool for CRED-2 from Misconfiguration Manager: You can use the hash from a compromised computer to spoof enrollment. Works with Adam Chester 🏴☠️ 's github.com/xpn/sccmwtf tool as well (since the http module is built around his code >_>) Kerb auth is a WIP






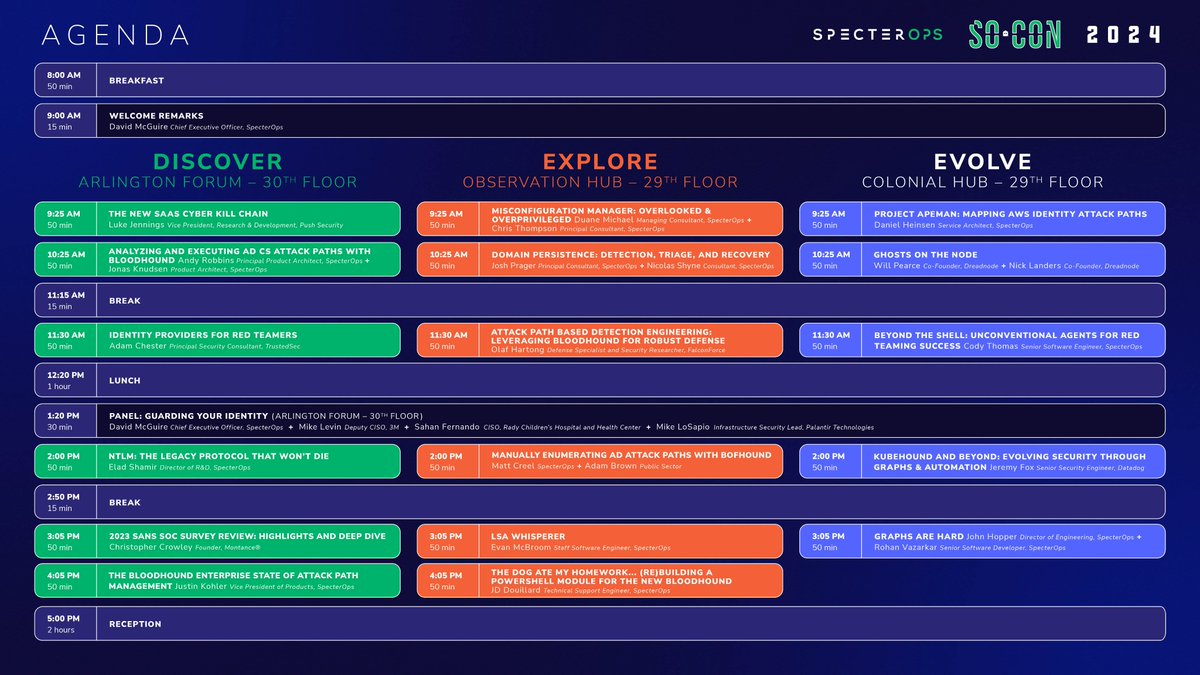
All slides for presentations at #SOCON2024 sponsored by SpecterOps 🇺🇦 are now live! github.com/SpecterOps/pre…


New blog post is up... Identity Providers for RedTeamers. This follows my #SOCON2024 talk, and provides the technicals behind the presentation, looking at other IdP's and what techniques are effective beyond Okta. blog.xpnsec.com/identity-provi…


Today at #SOCON2024 Chris Thompson & Duane Michael announced Misconfiguration Manager, a repository w/ attacks based on faulty MCM configs that provides resources for defenders to harden their security stance. Read more from Ionut Ilascu for BleepingComputer. ghst.ly/49KSYH9

