📱A lost phone can cause quite a scare, but you don't have to care with a remote wipe. Keep your devices secure.
Read about REMOTE WIPE at staysafeonline.in/concept/mobile….
🛡️ #DataSecurity #CyberSafetyTips #DigitalIndia


8 strange ways employees can (accidently) expose data
📌bit.ly/3M633Dj
#DataSecurity #Privacy #100DaysOfCode #CloudSecurity
#MachineLearning #Phishing #Ransomware #Cybersecurity
#CyberAttack #DataProtection #DataBreach #Hacked #Infosec


Dm me now for any #Hacked accounts or Recovery, #infosec #cybersecurity #pentesting #oscp #informationsecurity #hacking #DataSecurity #CyberSec #Hackers #tools #bugbountytips #Linux #websecurity #BTC B #cybersecurity awareness
#Snapchat #Instagram #Tiktok
#WhatsApp #Gmail


🔐 Data security? Piece of cake! 🍰 1️⃣ Regular updates 2️⃣ Strong passwords 3️⃣ Employee training Easy, right? 💪 Need help implementing these? We've got you covered at mac-pc-assist.com 🚀 Share your data security tips below! 👇 #DataSecurity #CyberSafety #TechTips

Writing the “Data Bill of Rights” as the very first data stored on the Crown Sterling Chain, sets in place the Personal Data Sovereignty Mission of Crown Sterling& ORION Messenger.
.
Join the ORION movement: hubs.li/Q02vWKSW0
#ORION #DataSovereignty #DataSecurity

Day 25 of #100daysofcoding : Explored Data Structures & Algorithms today, focusing on Hash Maps in Java and solving the Contains Duplicate II problem. github.com/DEveL0perLuckY…
#AI #Java #DSA #learning #DataSecurity #LearnInPublic #SoftwareDevelopment #SoftwareEngineering

Day 26 of #100daysofcoding : Explored Data Structures & Algorithms today, focusing on Design the Key in Java and solving the Group Anagrams problem. github.com/DEveL0perLuckY… #AI #Java #DSA #learning #DataSecurity #LearnInPublic #SoftwareDevelopment #SoftwareEngineering

Why wait for a cyberattack? Regular security audits can prevent disastrous data breaches. Don't just be reactive, be proactive! #DataSecurity #CyberRiskManagement #SentryOpsTech

#magecart alert!
beztech[.]site (IP: 195.242.110[.]8) fakes the MoneticoPaiment payment form on a French merchant #ecommerce website.
The stolen #payment data are sent to the same domain.
#PCIDSS #DataSecurity #FormJacking
![Source Defense Research (@sdcyberresearch) on Twitter photo 2024-05-06 11:59:06 #magecart alert!
beztech[.]site (IP: 195.242.110[.]8) fakes the MoneticoPaiment payment form on a French merchant #ecommerce website.
The stolen #payment data are sent to the same domain.
#PCIDSS #DataSecurity #FormJacking #magecart alert!
beztech[.]site (IP: 195.242.110[.]8) fakes the MoneticoPaiment payment form on a French merchant #ecommerce website.
The stolen #payment data are sent to the same domain.
#PCIDSS #DataSecurity #FormJacking](https://pbs.twimg.com/media/GM5OC-dXUAAGno9.png)

Rest easy with Mastermind—where data backup and restoration are always a fact, never a hope. Feel the difference reliability makes! #DataSecurity #TrustedBackup

🔒 Curious about revolutionizing your data security? Watch our latest video! Discover how Wahaya IT is keeping you ahead in safeguarding your digital assets. Don't miss out! #DataSecurity #WahayaIT #BatonRouge 🔒



Cybercrime can have significant effects on various entities, ranging from individuals to organizations & even nations.
Here's an overview of the impacts on different entities.
.
#cybercorp #cybercorp limited #cybersecurity #cloudsecurity #dataprivacy #dataprotection #datasecurity

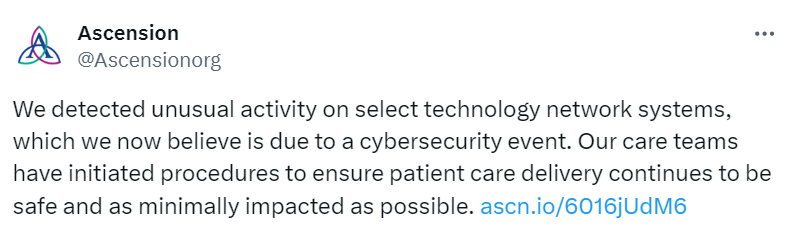
#Cybersecurity Alert!
Ascension Healthcare, a major private healthcare system in the US, has identified suspicious activity on specific tech networks, indicating a potential cybersecurity incident.
#DarkWeb #HealthcareSystems #DataSecurity

1 Data breach = Entire Digital Life Exposed
Don't be a meme 🤡
Use Strong, Unique passwords & 2 Factor Authentication!
#dataprivacy #datasecurity #password #password security #odeinfinity #odeholdings #safedata


Small or large business, proper cybersecurity is essential! 🔒💼
#CybersecurityForAll #ProtectYourBusiness #DataSecurity #TechSafety


Step into the era of machine learning-powered security analytics and unlock unparalleled insights into cyber threats. Discover how ML is revolutionizing cybersecurity bit.ly/3Wp8t3w
#USCSI #CyberAware #CyberSecurity #DataSecurity #CyberHygiene #cyber security #cyber

Data Sanitization is the Green Solution fidelityheight.com/data-sanitizat… #encryption #datasecurity #cybersecurity #sustainability