

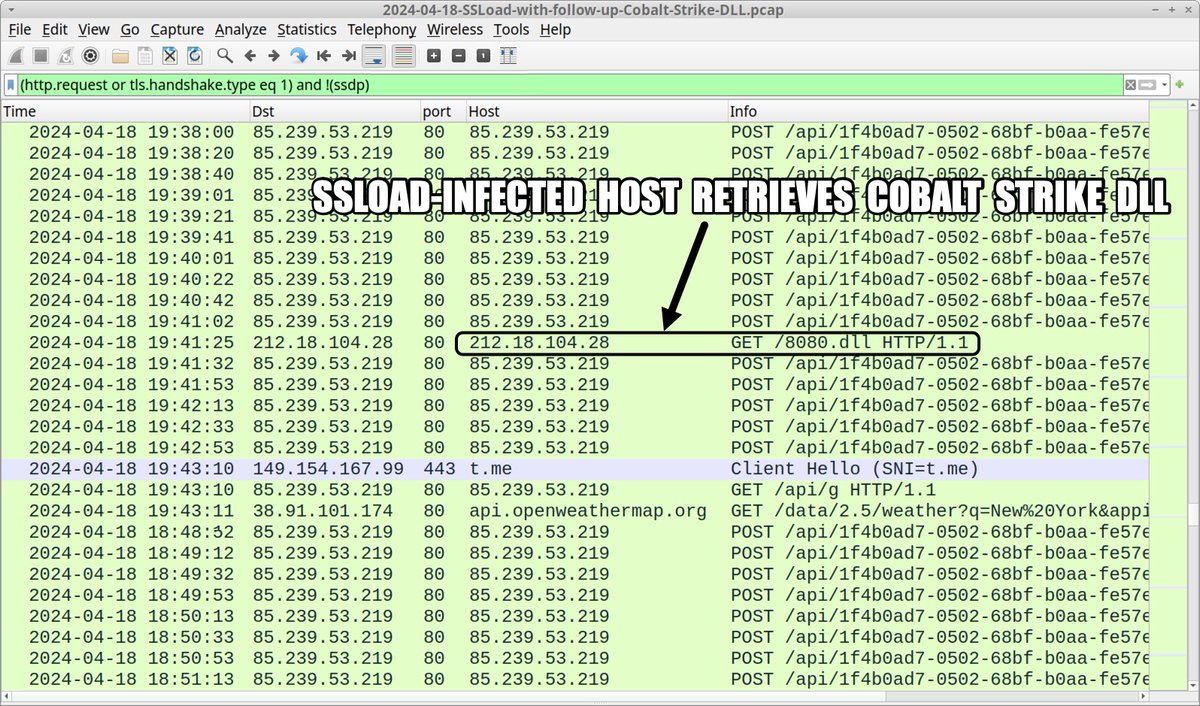
2024-04-18 (Thursday): #SSLoad infection leads to #CobaltStrike DLL. In this case we saw no follow-up Cobalt Strike C2 traffic. List of indicators available at bit.ly/3Q9SORR
#TimelyThreatIntel #Unit42ThreatIntel #Wireshark #InfectionAnalysis



#RCE attempt targeting #Drupal #CVE -2018-7600
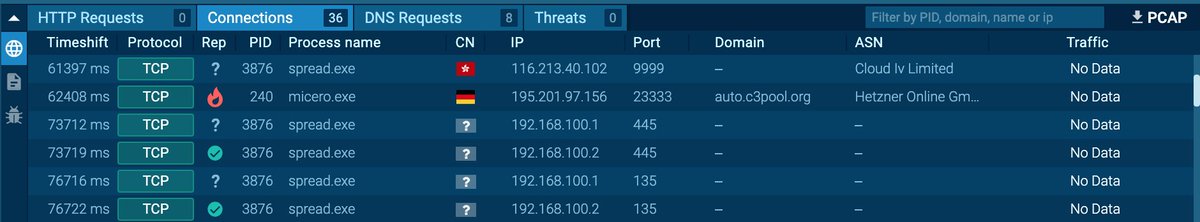
Spread.exe is a #coinminer that also connects to 116.213.40.102:9999 🇭🇰
Same IP was a #cobaltstrike server back on 2023-12-31
2024-04-17 15:17:52 UTC
Source IP: 206.238.221.2 🇸🇬
POST /user/register?element_parents=account/mail/


#RaspberryRobin 🍓🐦 is putting organizations at risk by acting as a precursor to other malware families, including #SocGholish , #IcedID and #CobaltStrike
And what’s worse, a new campaign is slipping through unnoticed: ow.ly/4OL150RcvXl














![Aaron Jornet (@RexorVc0) on Twitter photo 2024-04-22 06:25:48 #TTP
💥[T1204] Rust Loader execution
🧩[T1027] Encode info (XOR)
🪢[T1140] Decode info
🔃[T1620] Load SC in memory
🛠️[S0154] CobaltStrike usage
🔍[T1021] SMB CobaltStrike
📡[T1071] Beacon #C2 communication #TTP
💥[T1204] Rust Loader execution
🧩[T1027] Encode info (XOR)
🪢[T1140] Decode info
🔃[T1620] Load SC in memory
🛠️[S0154] CobaltStrike usage
🔍[T1021] SMB CobaltStrike
📡[T1071] Beacon #C2 communication](https://pbs.twimg.com/media/GLv30PhWgAA-dGe.png)