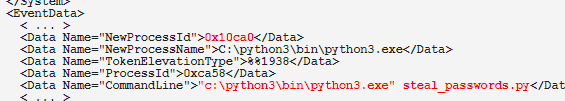
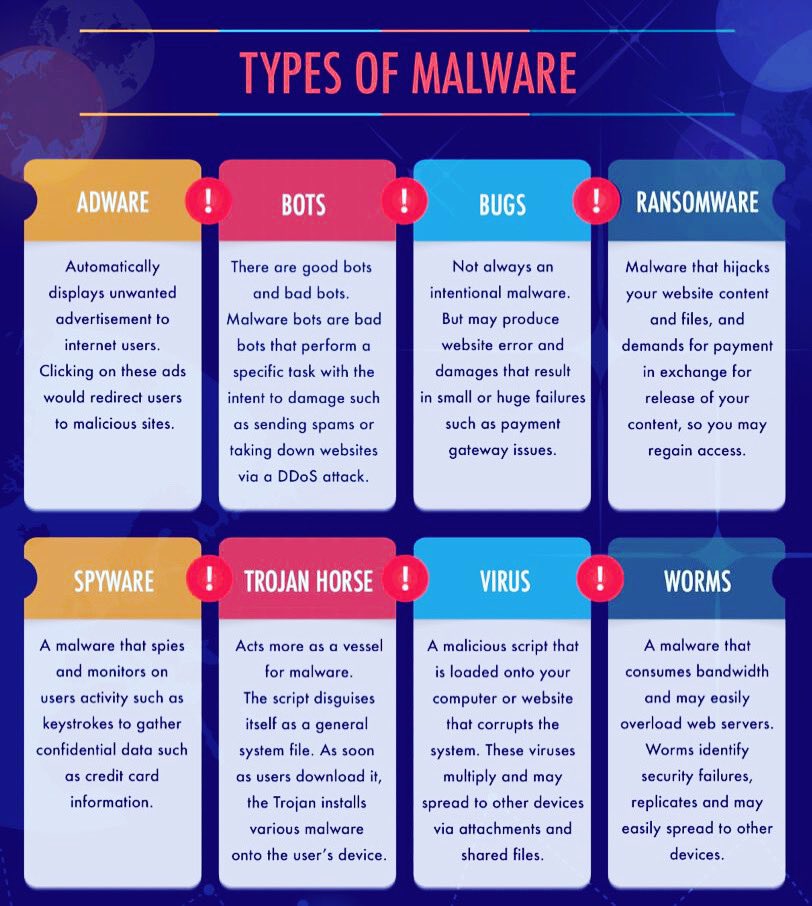
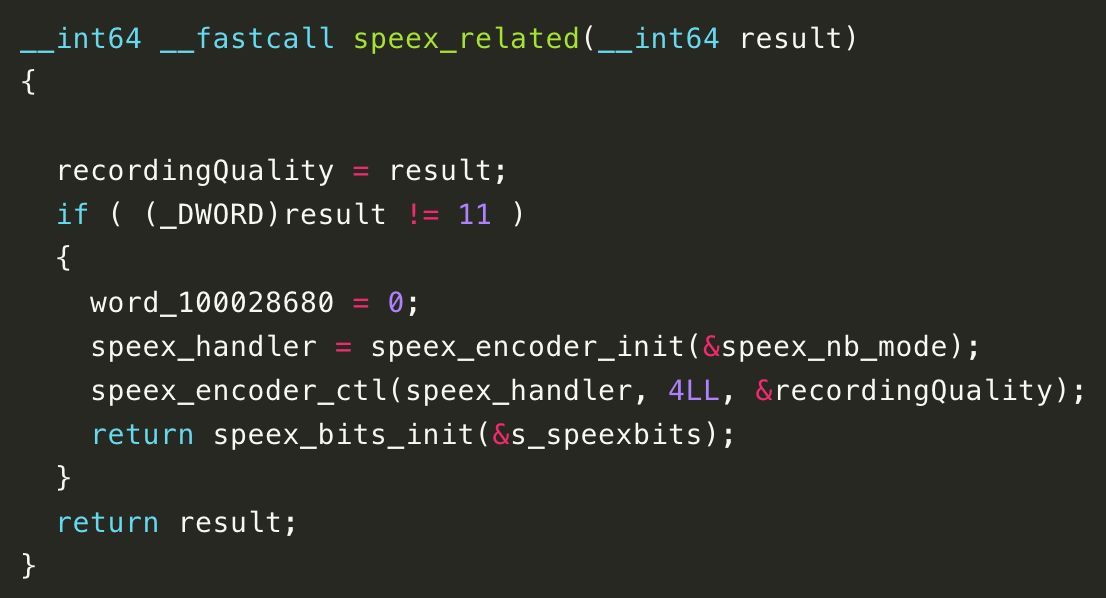
⛔️ #phishing ALERT 🎣
🔗 https://bridge-crypto-transitions[.]com
🔎 urlscan.io/result/55565ab…
#scam #NFT #malware
phishunt.io Jake | JCyberSec_ PeckShield Inc. @sniko_
![PHISH DESTROY (@CarlyGriggs13) on Twitter photo 2024-05-02 02:58:08 ⛔️ #phishing ALERT 🎣
🔗 https://bridge-crypto-transitions[.]com
🔎 urlscan.io/result/55565ab…
#scam #NFT #malware
@phishunt_io @JCyberSec_ @peckshield @sniko_ ⛔️ #phishing ALERT 🎣
🔗 https://bridge-crypto-transitions[.]com
🔎 urlscan.io/result/55565ab…
#scam #NFT #malware
@phishunt_io @JCyberSec_ @peckshield @sniko_](https://pbs.twimg.com/media/GMir9qNXQAEnJdH.png)





🥸 𝙏𝙚𝙡𝙚𝙜𝙧𝙖𝙢 𝙍𝘾𝙀 𝙋𝙊𝘾 - Fixed
A recent Telegram RCE bug has been fixed, but attackers are still trying to bypass the fix.
⚠️ 𝙒𝙖𝙧𝙣𝙞𝙣𝙜: If you receive a picture or video, DO NOT click or download it! It may contain malware.
#Telegram #Cybersecurity #bugbounty






Achcha khasa University chala rahe the. Fir pata chala ki system mein Malware hai.
#GalgotiaUniversity


Top Cyber Security Tools
Follow Cyber Security Edition
#Cybersecurity #InfoSec #CyberAttack #DataBreach #Ransomware #Malware #Phishing #CyberCrime #Hacking #Security #CyberThreats #IoTSecurity #CloudSecurity #CyberRisk #DataProtection




![PHISH DESTROY (@CarlyGriggs13) on Twitter photo 2024-05-02 02:42:13 ⛔️ #phishing ALERT 🎣
🔗 https://ashcryptocoin[.]com
🔎 urlscan.io/result/0bd2511…
#fake #malware #malware
@CloudflareHelp @1nf0s3cpt @sniko_ @JAMESWT_MHT ⛔️ #phishing ALERT 🎣
🔗 https://ashcryptocoin[.]com
🔎 urlscan.io/result/0bd2511…
#fake #malware #malware
@CloudflareHelp @1nf0s3cpt @sniko_ @JAMESWT_MHT](https://pbs.twimg.com/media/GMioUnaWUAA7SHK.png)