Is Palo Alto Networks down?
#PaloAltoNetworks status:
Prisma Cloud Compute service disruption. More: bit.ly/454ddOF
Seeing this? Please retweet. 🙏
Palo Alto Networks can you help?
#PaloAltoNetworks Down 😱


Things are moving fast at the #PaloAltoNetworks booth #OfficialCybersecurity Summit today.
Our cloud security experts are hwre and ready to rock your world! Swing by our booth, say hello, and let's chat all things security. See you there! #CyberSecurity #CloudSecurity

Is Palo Alto Networks down?
#PaloAltoNetworks status:
WildFire Global Cloud Issue. More: bit.ly/44N5V1f
Seeing this? Please retweet. 🙏
Palo Alto Networks can you help?
#PaloAltoNetworks Down 😱


Is Palo Alto Networks down?
#PaloAltoNetworks status:
WildFire Issue. More: bit.ly/3UYCncT
Seeing this? Please retweet. 🙏
Palo Alto Networks can you help?
#PaloAltoNetworks Down 😱


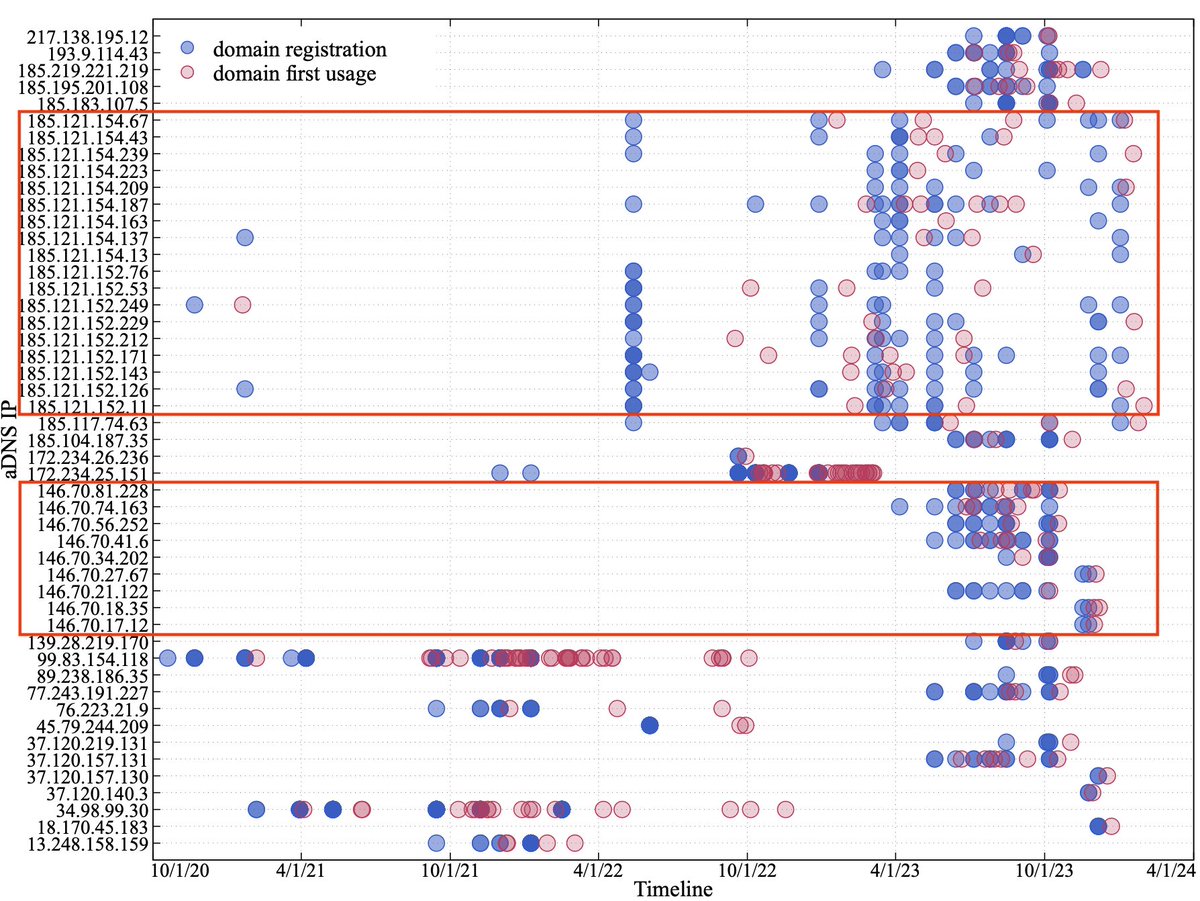
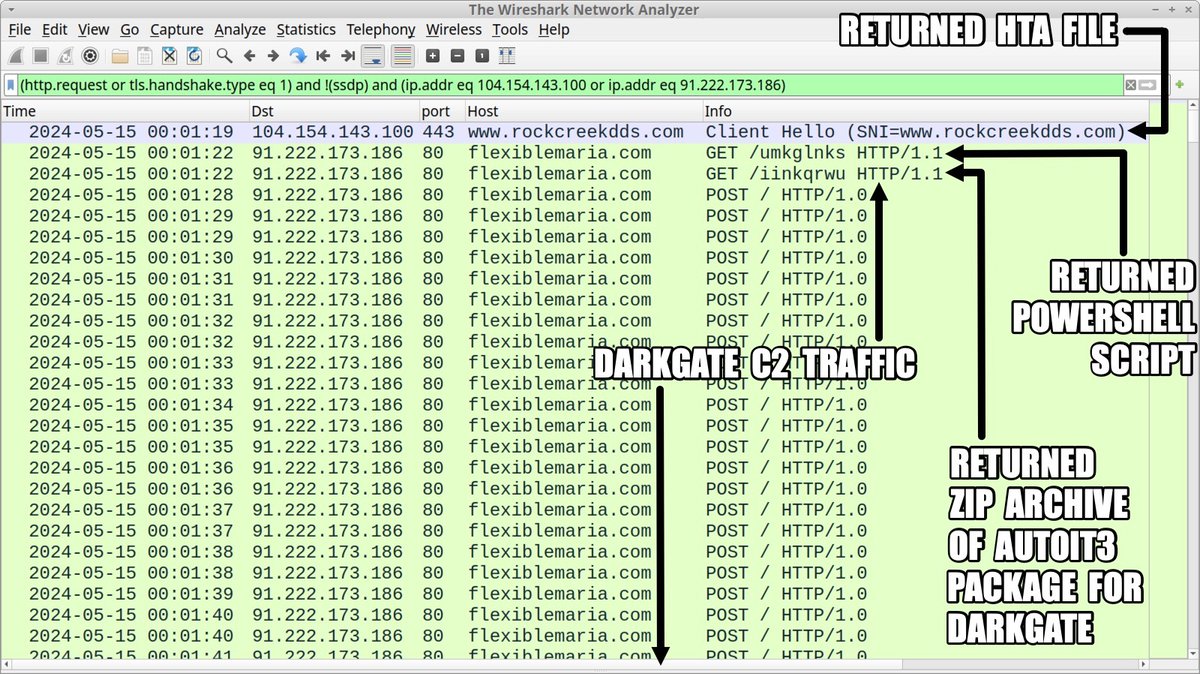
2024-05-14 (Tuesday): #DarkGate activity. HTML file asks victim to paste script into a run window. Indicators available at bit.ly/4bjvMAC
#TimelyThreatIntel #Unit42ThreatIntel #Wireshark #InfectionTraffic

Is Palo Alto Networks down?
#PaloAltoNetworks status:
Issue with onboarding new apps. More: bit.ly/4bC8Yvo
Seeing this? Please retweet. 🙏
Palo Alto Networks can you help?
#PaloAltoNetworks Down 😱



“Cyber hacking activities are at an all-time high,“ says Palo Alto Networks #CEO Nikesh Arora.
He tells Jon Fortt how the expanded partnership between IBM & #PaloAltoNetworks will use “AI to stop these threats in real time.”
$IBM $PANW #AI #Exclusive

IBM and Palo Alto Networks Forge AI-Powered Security Partnership
#AI #AI poweredsecurity #artificialintelligence #CortexXSIAM #Cybersecurity #IBM #llm #machinelearning #PaloAltoNetworks #QRadarSaaS
multiplatform.ai/ibm-and-palo-a…





パロアルトネットワークとIBMがサイバーセキュリティ戦略で連携
Palo Alto Networks and IBM Align Cybersecurity Strategies #SecurityBoulevard (May 16)
#PaloAltoNetworks #IBM #データセキュリティ #クラウドセキュリティ #AIセキュリティ
securityboulevard.com/2024/05/palo-a…


🔒 Future-focused at #PaloAltoNetworks : driving towards fully autonomous security, leveraging #AI & advanced analytics to revolutionize #cybersecurity . From ML-based prevention to autonomous operations. #CyberSec #Innovation #RSAC

Leveraging DNS Tunneling for Tracking and Scanning unit42.paloaltonetworks.com/three-dns-tunn… #Pentesting #CyberSecurity #Infosec