Sophia d’Antoine
@Calaquendi44
Founder @Margin_Research, Hacker in Residence @ NYU, @RPISEC
ID:768856800682713090
https://sophia.re 25-08-2016 17:05:20
360 Tweets
2,9K Followers
125 Following




To quote Dave Aitel: ‘It's only hard to find vulnerabilities if you look for hard vulnerabilities. You should look for easy ones.’ 🔍🦗


PROGRAM ANALYSIS FOR VULNERABILITY DISCOVERY by Sophia d’Antoine and Jordan Wiens offensivecon.org/trainings/2024…

Thrilled that my alma mater Rensselaer has claimed #1 in the latest Cyber Power Rankings! This achievement reflects their exceptional skills & dedication to cybersecurity. I'm sure my fellow cybersec alums Dave Aitel Robert C. Seacord (@[email protected]) Mark Russinovich Perri Adams are proud too
news.rpi.edu/approach/2023/…


The proliferation of offensive cyber capabilities poses risks to national security and human rights.
To better understand this ecosystem we asked Winnona 💾 Sophia d’Antoine Daniel Moore Chris Bing Ollie Whitehouse Monica M. Ruiz Forscey Jen Roberts for their insights.
atlanticcouncil.org/content-series…

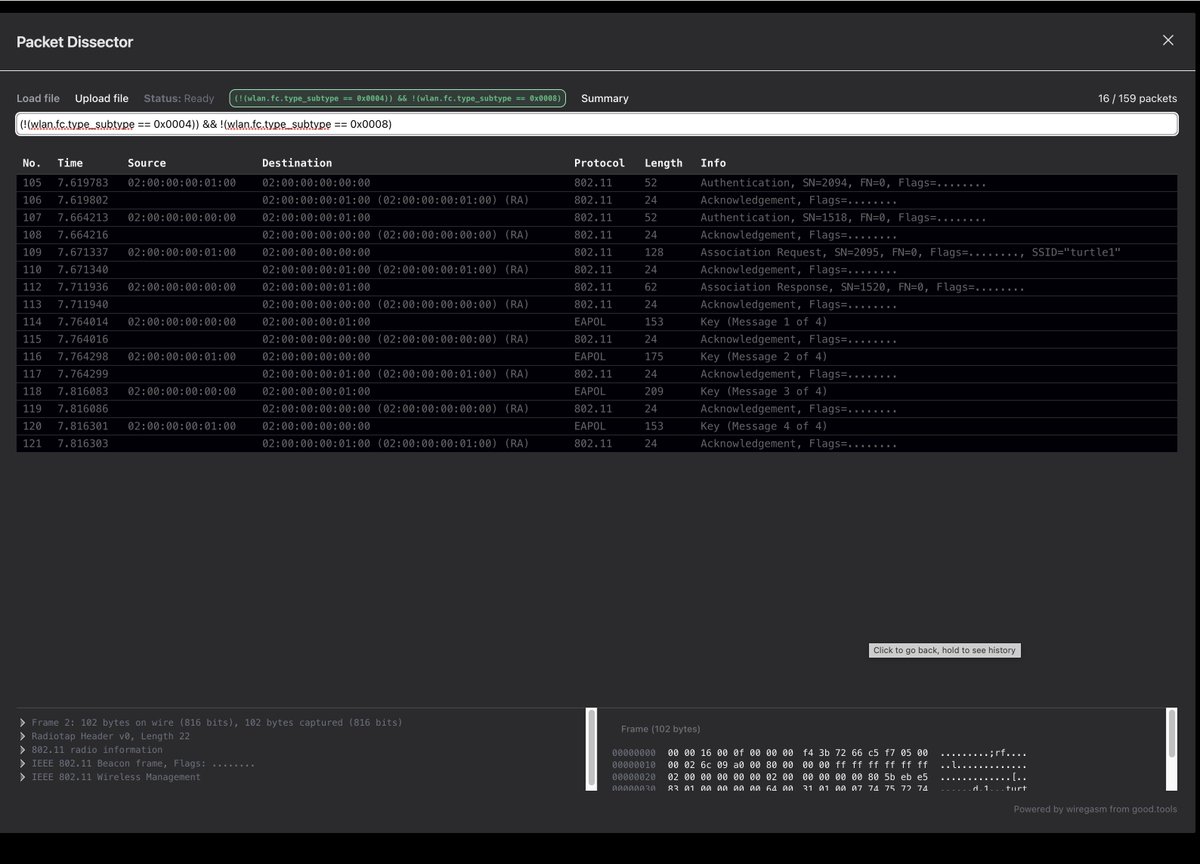
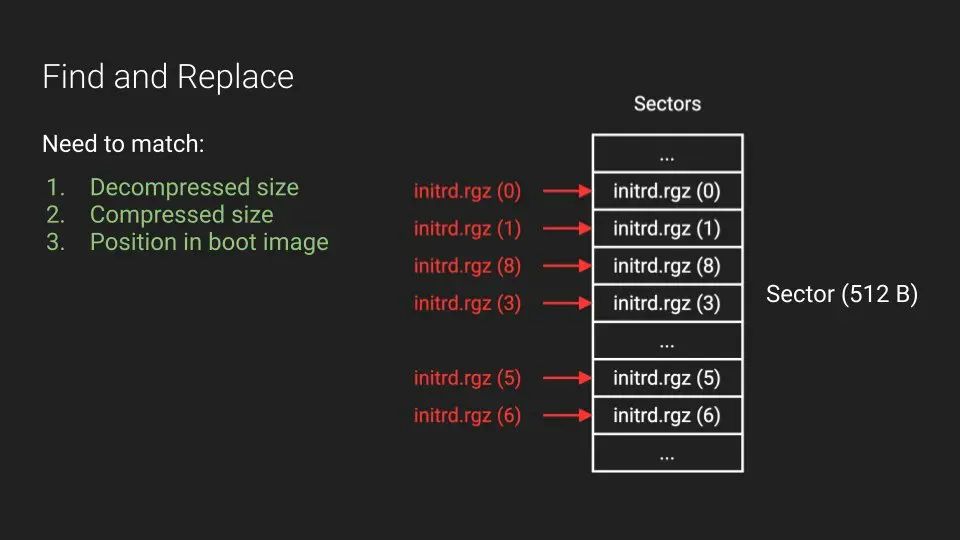
Great writeup about reverse engineering MikroTik router by Harrison Green and ian dupont
Blog post: margin.re/2022/06/pullin…
Slides (RECon): margin.re/content/files/…
#iot #embedded #mikrotik #reverseengineering #cybsersecurity

Interested in learning more about offensive cyber capabilities market place and how these vendors tend to operate?
Check out our blogpost featuring Winnona 💾, Sophia d’Antoine, Daniel Moore, Chris Bing, Ollie Whitehouse, Monica M. Ruiz Forscey, and Jen Roberts here:
atlanticcouncil.org/content-series…


Margin is proud to sponsor some of the best CTF players from around the world.
Come say hi at our #MidnightSun23 table👋

💪 Security is about building as well as breaking!
🍎The next speaker, Sharvil Shah will teach us about building next-gen security tools, with a focus on macOS at #MidnightSun23
➡️conf.midnightsunctf.com/speakers/sharv…







The proliferation of offensive cyber capabilities poses an expanding set of risks to national security and human rights. To better understand this opaque ecosystem, we asked Winnona 💾 Sophia d’Antoine Daniel Moore Chris Bing Ollie Whitehouse Monica M. Ruiz Jen Roberts atlanticcouncil.org/content-series…