
Innovate your prototyping process by incorporating reverse engineering into your toolkit, alongside cutting-edge technologies like 3D scanning and 3D printing.
#InnovatePrototyping #ReverseEngineering #3DScanning #3DPrinting #DesignWorkflow #RealLifeReferences


In some situations during vulnerability research I've found functions flagged as functions of no return, so it may be useful to remember how to identify them and, eventually, fix problems. This picture is just a quick review.
#idapro #vulnerability #reverseengineering


The Artec 3D | Professional 3D solutions Leo stands out as the sole wireless and completely standalone professional 3D scanner, engineered to simplify the scanning process.
Read more: altem.com/artec-leo/
#ArtecLeo #3DScanning #FastScanning #HandheldScanner #ReverseEngineering

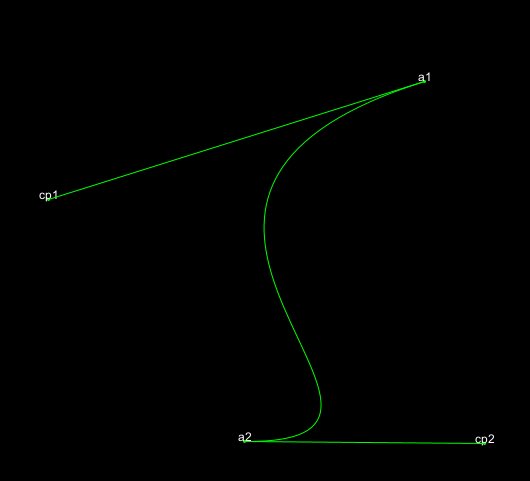
Early experiments in bezier curves from a couple of years back. Can’t remember where I saw something similar but thought I’d give it a crack. I see Kiwis? #WIP #creativecoding #genart #generativeart #bezier #mathart #p5js #processing #reverseengineering #RecodeRethink

🔍 Ready to shed light on vulnerabilities? Join clearbluejar's training at x33fcon! Learn to analyze real-world Windows and Android vulnerabilities, progressing from knowing about CVEs to understanding their root cause. x33fcon.com/#!t/JohnMcInto… #Cybersecurity #ReverseEngineering


Harness the potential of reverse engineering with our meticulous process, seamlessly converting your current part into a precise digital model while maintaining its original geometry.
#ReverseEngineering #DigitalModeling #PartConversion #GeometricReplication #EngineeringProcess


Excited to share my new post on how Gemini 1.5 Pro can now analyze entire binaries, offering a new & scalable approach to threat detection.
Working on producing these reports at scale - stay tuned!
cloud.google.com/blog/topics/th…
#malwareanalysis #reverseengineering #AI

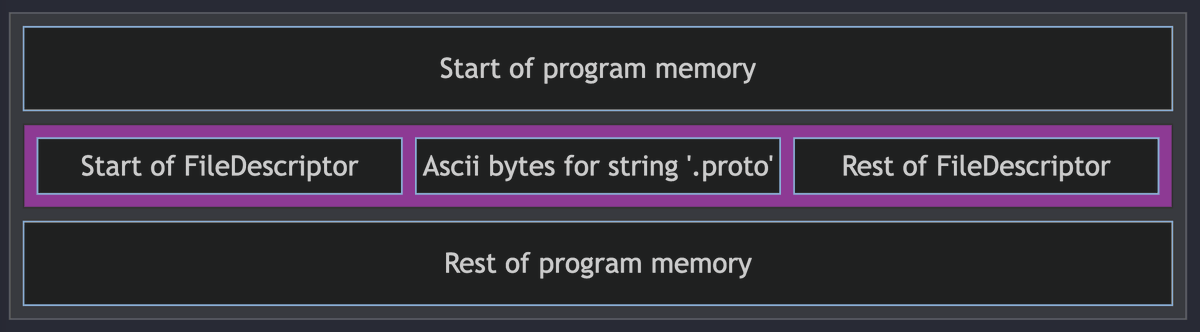
Reverse Engineering Protobuf Definitions From Compiled Binaries arkadiyt.com/2024/03/03/rev… #Pentesting #ReverseEngineering #CyberSecurity #Infosec

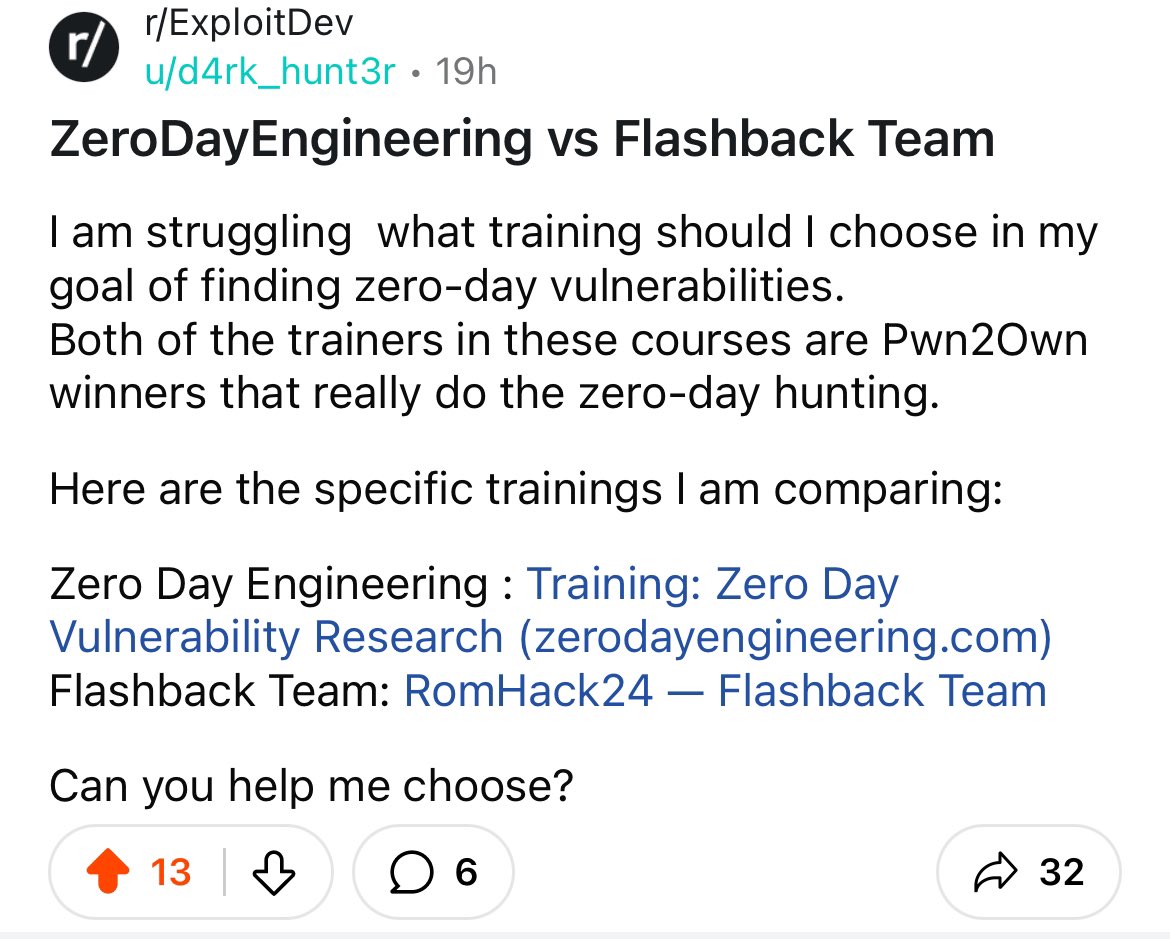
Alisa Esage Шевченко Zero Day Engineering Someone is marketing your training in Reddit haha I also saw it in ReverseEngineering subreddit. Might be interested for you.

FARO Q1 FY2024 Conference Call on May 2, 8AM ET
dailycadcam.com/faro-q1-fy2024… via DailyCADCAM.com
FARO Technologies #Q1FY2024 #RevenueResults #3DScanning #3DMeasurements #3DInspection #3DMetrology #ReverseEngineering #CAM



Creaform Launches Enhanced HandySCAN Portable 3D Scanners
dailycadcam.com/creaform-launc… via DailyCADCAM.com
Creaform #HandySCAN3D #Portable3DScanners #3DScanning #3DMeasurements #3DMetrology #3DInspection #ReverseEngineering #CAM


Unlock the secrets of reverse engineering with Central Scanning!
Starting with 3D scanning, we shape detailed CAD models, transforming physical objects into digital masterpieces.
Learn more - central-scanning.co.uk/reverse-engine…
#ReverseEngineering #3DScanning #CentralScanningInnovation


Creaform Launches Enhanced HandySCAN Portable 3D Scanners dailycadcam.com/creaform-launc… #3Dscanning #reverseengineering #qualitycontrol #testing #productdevelopment Creaform


It's hard to get much bigger than a 747 and the #SpaceShuttle , so we wanted to put the Leo from Artec 3D | Professional 3D solutions through its paces. Check out it even picks up the discoloration on the final scan!
Discover the Artec Leo: hubs.la/Q02w1J2h0
#reverseengineering

🚘 This article delves into the role played by #iReal3D scanners, leveraging their swift data capture, adaptability of various materials, and precision to meet the multiple demands of the automotive sector.
#3dscanning #automotive #reverseengineering
ireal3dscan.com/case/ireal-3d-…

Hello! Check out ObjectSecurity's new blog post 'You Should be Automating Binary Reverse Engineering: Here’s Why.' (24 April 2024) bit.ly/3WfyPoP #reverseengineering #binaryanalysis - enjoy!

Hi! Check out ObjectSecurity's new blog post 'You Should be Automating Binary Reverse Engineering: Here’s Why.' (4/24/24) bit.ly/44eFQba #reverseengineering #binaryanalysis - enjoy!

قسمت اول از فصل دوم ، دوره ی رایگان مهندسی معکوس نرم افزار منتشر شد.
در این قسمت نگاهی به زبان #اسمبلی انداختیم.
youtu.be/LpRRj_w45ao
#ReverseEngineering #مهندسی_معکوس

Hi! Check out ObjectSecurity's new blog post 'You Should be Automating Binary Reverse Engineering: Here’s Why.' (24 April 2024) bit.ly/4aPmJqB #reverseengineering #binaryanalysis - enjoy!