Check Point Software
@CheckPointSW
You deserve the best security. Get the protection you need against Gen V attacks.
ID:35138066
http://www.checkpoint.com 25-04-2009 03:52:45
15,6K Tweets
71,3K Followers
2,7K Following
Follow People


With 350,000 locations across 140 countries, the security team at Tuttnauer USA needed to ensure the protection of patient data and safety.
Learn why they integrated Check Point Quantum IoT Nano Agent® with their device software to improve security: bit.ly/3U6MEmy





It's #TaxDay , and experts are warning last-minute filers to stay vigilant against tax scams.
Tune in as our own Jeremy Fuchs joins Greg Nibler on FOX 12 Oregon to warn people what to watch out for and how to avoid becoming a victim: youtube.com/watch?v=c8YVE2…

ICYMI, last week we introduced the following #emailsecurity features:
• Unified Quarantine
• DMARC Monitoring
• Archiving
• Smart Banners
Read the full update here 👉 bit.ly/43X4xJ7




.Brisbane Catholic Education achieves deep visibility into data center traffic, secures vital school services, and improves reliability with Quantum Security Gateways.
Read the full story here: bit.ly/3PYLTuM


🆕 #EmailSecurity features available in Harmony Email & Collaboration:
• Unified Quarantine
• DMARC Monitoring
• Archiving
• Smart Banners
Learn how they work here: bit.ly/43X4xJ7


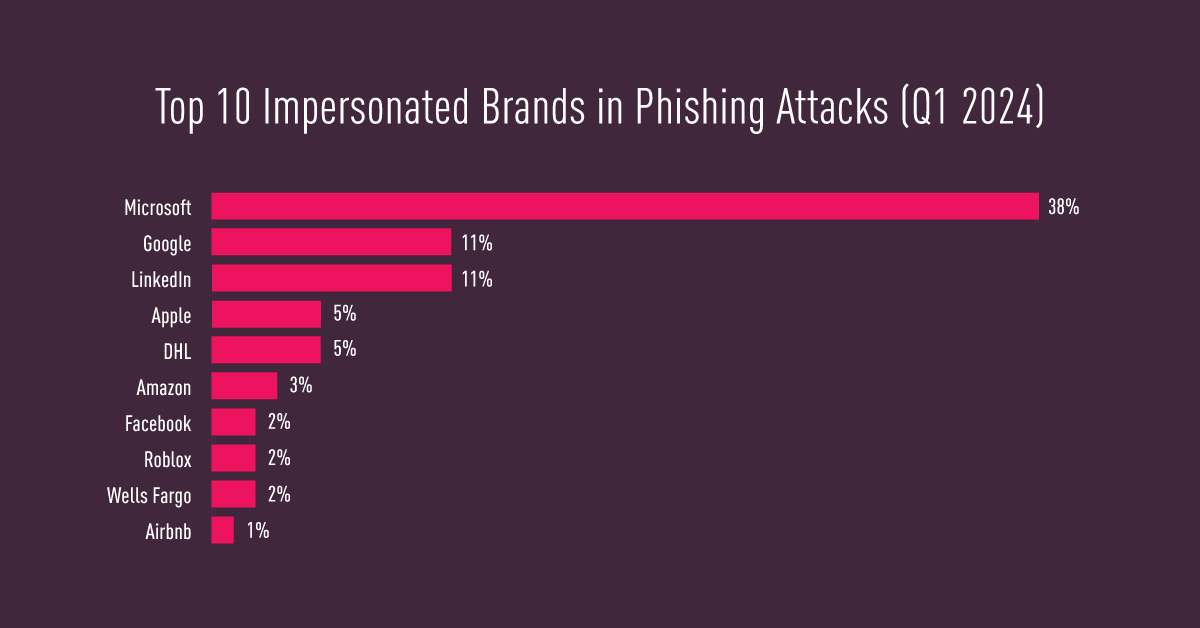
The stats are in... 📊 Organizations experienced a 28% increase in global #CyberAttacks in Q1 2024, with North America emerging as the region most impacted by ransomware.
Learn more:
blog.checkpoint.com/research/shift…

“It used to be that seeing was believing, but not so much anymore.” -Rupal Shah Hollenbeck
From election misinformation to business cybercrime, deepfake tech powered by #GenAI is going mainstream. Learn how to prevent and spot #deepfakes on CNBC:
cnbc.com/2024/04/10/how…


Check Point's @cindibcarter joined News 12's Tara Rosenblum to discuss why 88 million Americans were impacted by data breaches in 2023, and what both hospitals and patients can do to protect their data. Tune in! connecticut.news12.com/turn-to-tara-i… #turntotara