Samir
@SBousseaden
Detection Engineering | Elastic Security
Mastodon: @[email protected]
ID:1112645486
22-01-2013 21:08:28
2,6K Tweets
23,7K Followers
1,1K Following

Interested in securing the lifecycle of your LLM? The newest article from Mika Ayenson details his research into native protections against the OWASP® Foundation Top Ten with ES|QL. Check it out: go.es.io/3Qht7i9
#ElasticSecurityLabs #GenerativeAI #LLM #securityresearch







#ElasticSecurityLabs researchers SolidSnake and Daniel Stepanic share new details about an emerging #PikaBot campaign using obfuscation to evade defenses and deploy a variety of malware payloads. Read more at elastic.co/security-labs/…

Wrote a blog on monitoring Okta threats with Elastic Security. This is a step-by-step guide on getting started with a FREE trial. More to come on #threatdetection and #threathunting very soon! Thanks for reading.
go.es.io/3V5ujZx

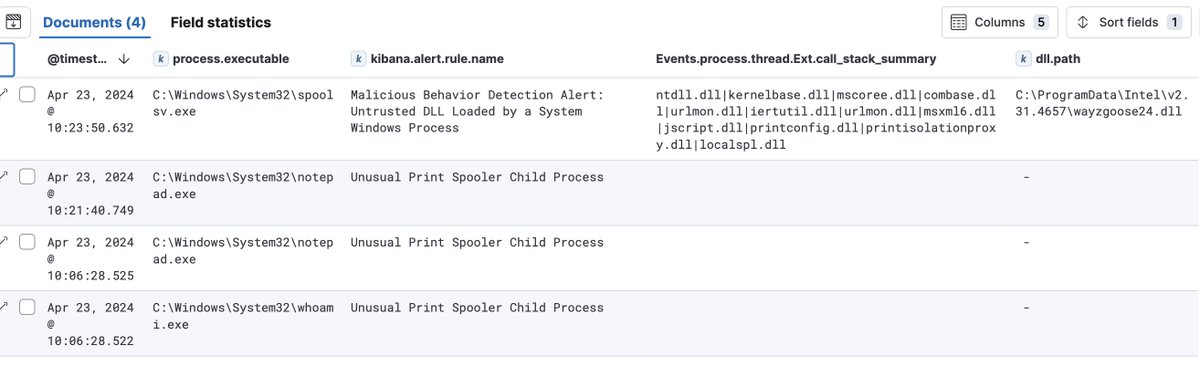
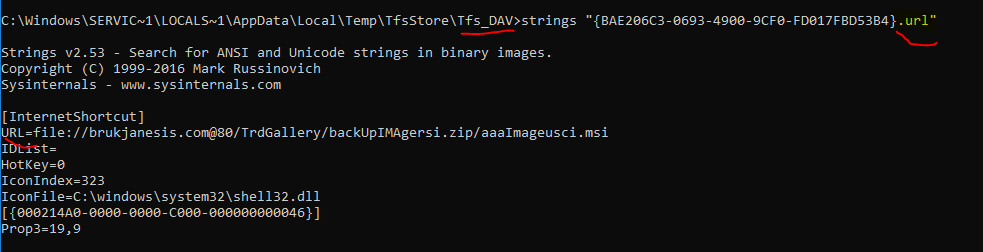
useful forensics artifacts for #CVE_2024_21412 : .url file in the WebDav cache folder
C:\Windows\ServiceProfiles\LocalService\AppData\Local\Temp\TfsStore\Tfs_DAV\*.url







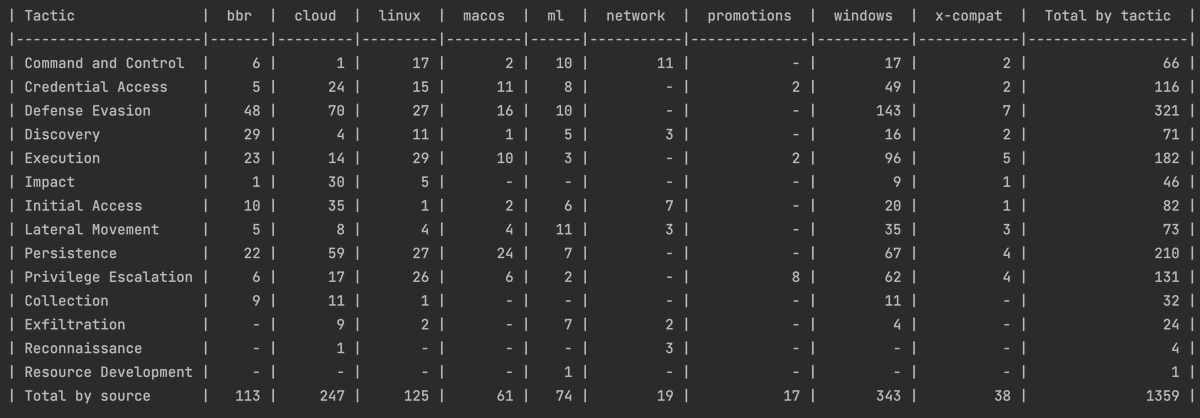
in a year period we almost doubled our rules using #Elastic Defend behavior protection (600+):
github.com/elastic/protec…
h/t Mika Ayenson DefSecSentinel w0rk3r Ruben Groenewoud Joe Desimone Gabriel Landau John U Justin Ibarra Terrance DeJesus & ofc the entire team


Analyzing data for threats can be an incredibly daunting task. Luckily, Terrance DeJesus and Eric Forte — two major contributors for the Global Threat Report — have laid out their step-by-step process of data analysis with Google Cloud: go.es.io/48iNjXO
#ElasticSecurityLabs