Justin Ibarra
@br0k3ns0und
threat research & detection engineering lead @elastic by way of @endgameinc | compulsive heavy iron displacer | I always like my own tweets
ID:3305197544
https://br0k3nlab.com/ 03-08-2015 13:54:56
712 Tweets
1,3K Followers
808 Following




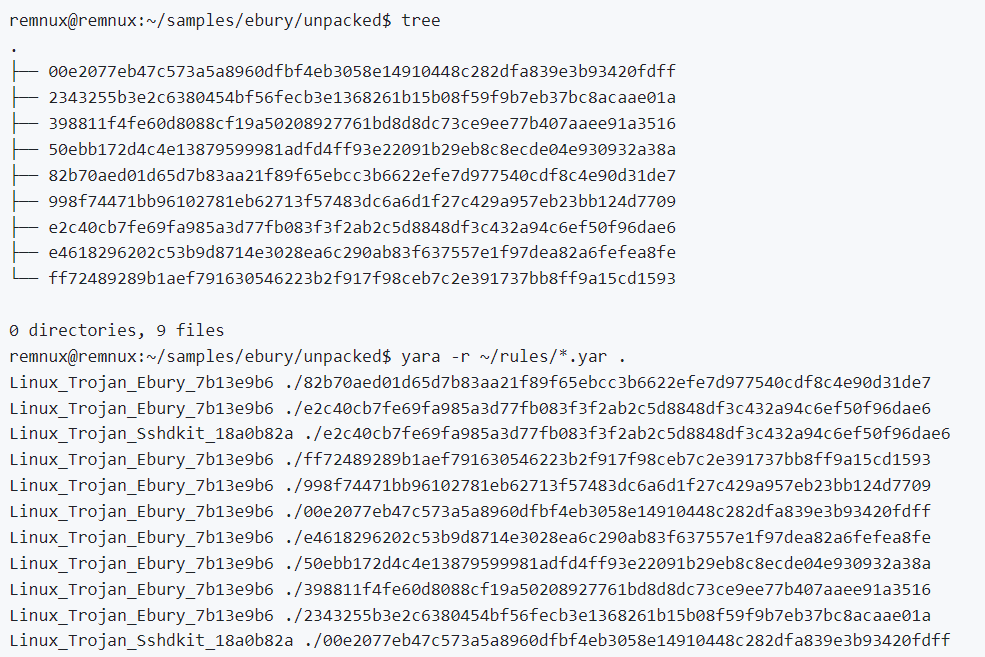
Ebury is some fascinating and sophisticated malware! Props to ESET Research for their extensive threat research report. Happy to see our coverage at Elastic is on point. 🔍👏
#ebury #ElasticSecurityLabs #elastic




🔒 Gear up, hackers! 🔒
#CloudVillage CTF BSidesSF is just an hour away⏰
Join the cyber showdown and prove your skills!
Register now at ctf.cloud-village.org and prep your tools for battle! 💻🛡️
#BSidesSF2023 #cloudsecurity #CTFChallenge #CaptureTheFlag #InfoSec






Interested in securing the lifecycle of your LLM? The newest article from Mika Ayenson details his research into native protections against the OWASP® Foundation Top Ten with ES|QL. Check it out: go.es.io/3Qht7i9
#ElasticSecurityLabs #GenerativeAI #LLM #securityresearch

Our experts have released part two of our analysis on the #XZbackdoor .
The findings reveal a dual-layered strategy used by the attackers, combining social engineering with sophisticated technical exploitation to breach XZ Utils' integrity.
More ⇒ kas.pr/w27p