Anton Cherepanov
@cherepanov74
Malware researcher at ESET Slovakia. Opinions are my own.
ID:1381601046
26-04-2013 10:44:12
1,3K Tweets
4,4K Followers
854 Following






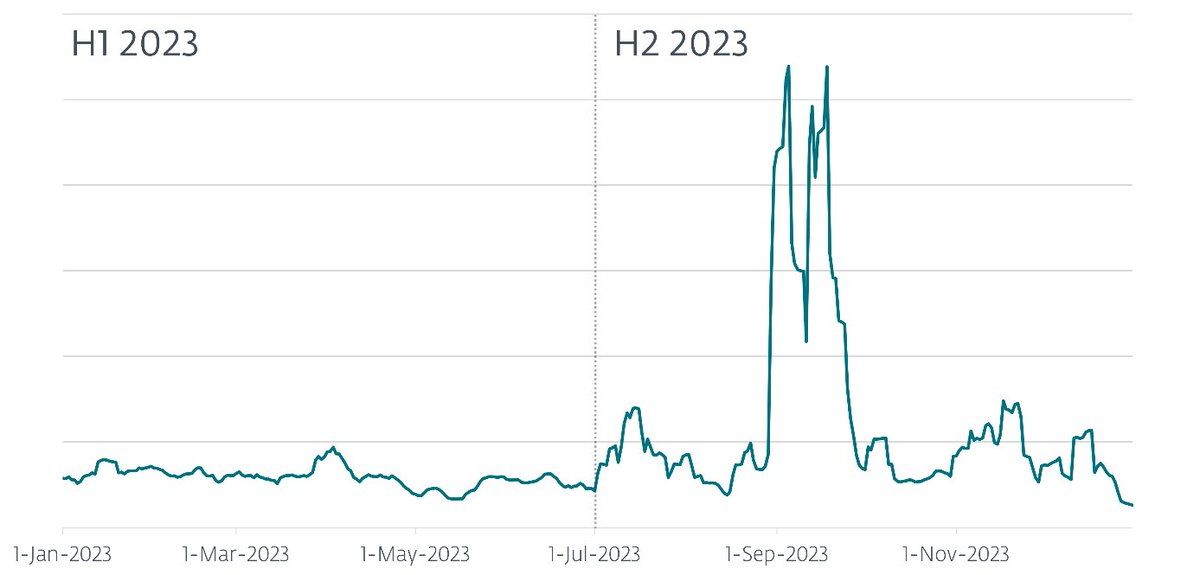
#ESETresearch ’s monitoring of #AceCryptor shows that the activity of this notorious #cryptor -as-a-service (CaaS) has reached new heights. In H2 2023, the number of AceCryptor attack attempts we detected tripled when compared to the first half of 2023. welivesecurity.com/en/eset-resear… 1/6


#ESETresearch has discovered a new campaign by 🇨🇳China-aligned #APT #EvasivePanda , leveraging the Monlam Festival to target Tibetans. The campaign included a targeted watering hole, compromised news website, and an additional supply-chain attack ... welivesecurity.com/en/eset-resear… 1/7








#ESETresearch has discovered a China-aligned APT group, which we named #Blackwood , that leverages adversary-in-the-middle (AitM) to deliver the NSPX30 implant via software updates. NSPX30 is a sophisticated implant evolving since at least 2005. facundo Mz welivesecurity.com/en/eset-resear… 1/6

#ESETresearch has documented a growing series of OilRig downloaders using legitimate cloud service providers for C&C communication, all deployed against a small group of especially interesting, repeatedly victimized targets in Israel. welivesecurity.com/en/eset-resear… Zuzana Hromcova 1/7

#ESETresearch warns about malicious Python packages in the official @PyPI repository that target Windows and Linux. This cluster shares metadata or has similar payloads, and seems different from the one we reported in May: x.com/esetresearch/s…. Marc-Etienne M.Léveillé 1/6