Nick Britton
@nerbies
Penetration Testing Practice Development Lead @protiviti
ID:236111448
09-01-2011 20:49:17
493 Tweets
236 Followers
448 Following


 's Twitter Profile Photo Ray [REDACTED](@RayRedacted) 's Twitter Profile Photo](https://pbs.twimg.com/profile_images/1760640601081491457/YLWr-Xgc_200x200.jpg)
The PancakesCon 2 videos for this year are available now at PancakesCon.org/videos.
Our A/V crew had a secret goal of releasing these within a week of the con. We hope you enjoy them as much as we do.
HUGE thx to Dustin (BusySignal), @c1ph0r, and Golgothus (Zach He/Him) for their work this week!


Thanks Ray and a huge shoutout to everyone involved with PancakesCon (Virtual Hacking Conference). Awesome conference format and so well run!
 's Twitter Profile Photo Ray [REDACTED](@RayRedacted) 's Twitter Profile Photo](https://pbs.twimg.com/profile_images/1760640601081491457/YLWr-Xgc_200x200.jpg)
Nick Britton Nick,
I loved your talk. It was awesome.
Here's a video:
youtu.be/CDIkW3AALCo

Huge shout out to Lesley Carhart and all the volunteers and helpers for organizing and running PancakesCon (Virtual Hacking Conference). I had a blast and enjoyed all the talks thoroughly. Well done everyone!

Prepping pizza for my talk on PancakesCon (Virtual Hacking Conference) starting in just over an hour from now (7pm EDT). The votes were overwhelmingly for live demo, so I will be attempting to design #KQL threat hunting queries while baking a pizza simultaneously streaming live on pancakescon.org/track2



'Modern Web Application Vulnerabilities (on the perimeter right now)' by Cary Hooper
Cary (h00p) #BSidesDFW2020


'Managing Misfits: Lessons Learned from a decade leading a penetration testing team.' by Krissy Safi and Nick Britton
#BSidesDFW2020

'A Drop of Jupyter: A Modular Approach to Penetration Testing' by Omar Bheda, Nate Kirk, Cody Ruscigno
#BSidesDFW2020

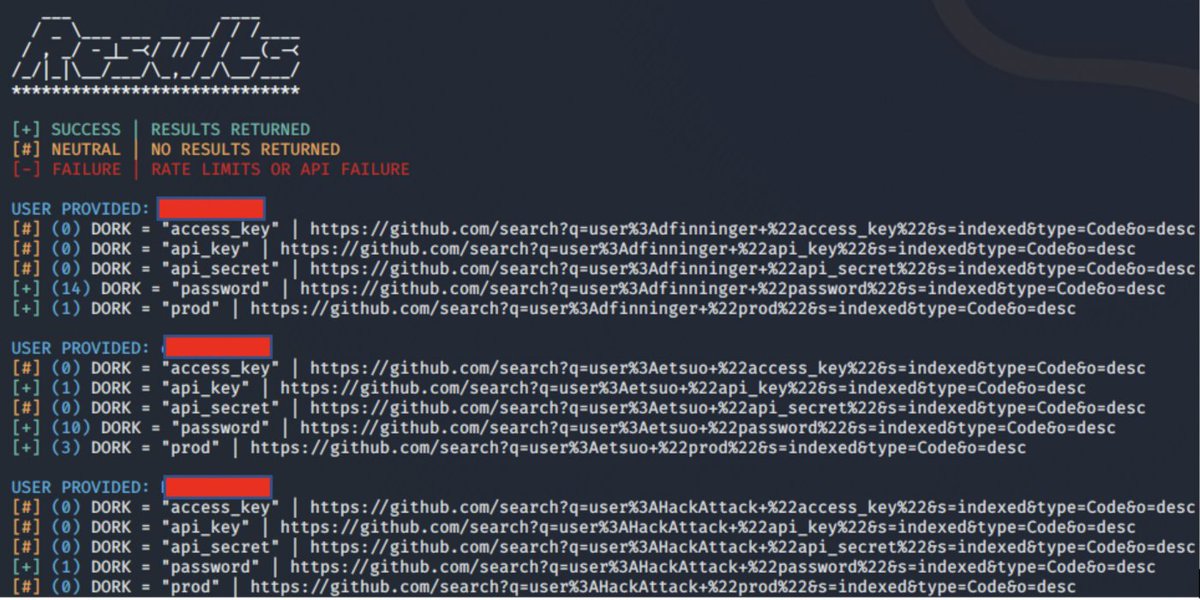
Introducing GitDorker - My automated GitHub dorking tool with over 240+ dorks for easy bug bounty wins :)
#HackerOne #infosec #Synack #bugcrowd #bugbountytip s #bugbountytip #CyberSecurity #100DaysOfCode
Check out my blog post for more details!
medium.com/@obheda12/gitd…


The #Zerologon bug is going to be game over for a lot of companies and I reckon the weaponised payloads in ransomware will be pretty bad now; Destroy the DC by changing the password, get DA ransom the network and it's maximum pay day for criminals.