
Doing this social engineering attack project reminded me of the Cisco Module (Cyberthreat Management) which taught the ethics of a cybersecurity specialist.
The difference between a cybersecurity specialist and a cybercriminal is ETHICS.
#cybergirl #socialengineeringattack

Microsoft Releases New-Open Source Tool for OT Security #CyberSec #InfoSec #DataBreach #CyberAware #CyberThreat databreachtoday.com/microsoft-rele…

FTC Finalizes Health Breach Notification Rule Update #CyberSec #InfoSec #DataBreach #CyberAware #CyberThreat databreachtoday.com/ftc-finalizes-…


Initial Access Brokers (IABs) facilitate network access for attackers by selling access points on the Dark Web. Multifactor authentication and credential monitoring mitigate risk against IAB-driven #ransomware attacks. #Cybersecurity #CyberThreat tiny-link.io/FwZ0coQ1jQ8FuG…


The best defense against cyber threats? A well-informed user! Stay educated, stay empowered. #CyberEducation #cyberthreat slickcybersystems.com/2024/02/05/cyb…


Cheap, independently produced #ransomware is on the rise — we found 19 new variants since June 2023.
While these unsophisticated offerings might look like a lesser #CyberThreat than RaaS, adversaries can extort sizable profits from individuals and SMBs. Learn more ⬇️

The top 10 things AI security tools should know for CISOs
Read more⬇
bigfishtec.com/news/4-152-The…
#bigfishtec #bigfishcanada #cybersecurity #AISECURITYTOOLS #AIPOWEREDCLOUDDELIVERED #AIPOWEREDCYBERSECURITY #CYBERADVERSARY #CYBERSECURITY #cyberthreat


RANSOMWARE ALERT
-
Herron Todd White falls victim to BLACK SUIT Ransomware
Group claims to have obtained organization's data.
-
#data_breach
#data_leak
#infosec
#dark_web
#DataBreach
#DataLeak
#Services
#CyberThreat
#CyberAttack


Sometimes #malware isnt detected, we need to be proactive & diligent in our #security #planning , #defense and #monitoring .
Maware in #Ukraine evaded #detection for a decade
buff.ly/4d9CU3A
#breakingnew #technews #cybernews #cybersecurity #cyberthreat #cybercrime


The protection of our personal and sensitive data has never been more critical. The alarming rise in data breaches and cyber threats has put data security at the forefront of global concerns.
istratus.com/blog/secure-yo…
#DataEncrytion #DataProtection #SensitiveData #CyberThreat


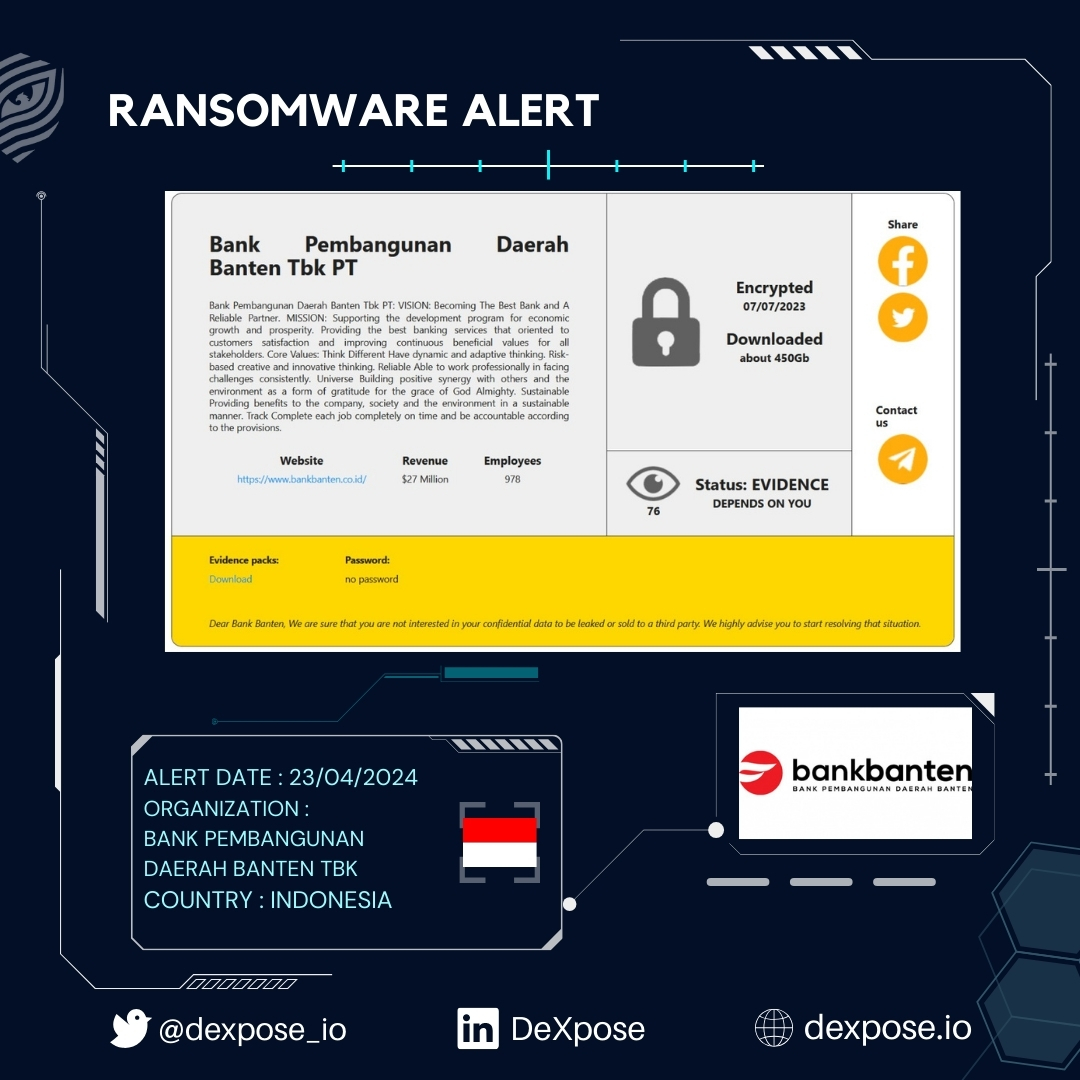
RANSOMWARE ALERT
-
Bank Banten falls victim to RansomHouse Ransomware
The group claims to have access to 450 GB of the organization's data.
-
#data_breach
#data_leak
#infosec
#dark_web
#DataBreach
#DataLeak
#Services
#CyberThreat
#CyberAttack

Cloudy with a chance of ransomware: Third-party cloud tools are putting you at risk, says OmniIndex
mvnt.us/m2414638 OmniIndex #Ransomeware #Cloud #Computing #CyberDivision #CyberThreat


Rubrik Execs on How Going Public Will Drive More Innovation #CyberSec #InfoSec #DataBreach #CyberAware #CyberThreat databreachtoday.com/rubrik-execs-o…

Scammers can target anyone, even 👉🏻 U 👈🏼
Stay alert and cautious of online threats at all times and always #CheckTheClick .
#CyberPeace ☮️ #cybersecurity #cybercrime #cyberthreat #cybersecurity awareness #cyberattackdefense #cyberattackers


Researcher Strips ROM For Binary Code #CyberSec #InfoSec #DataBreach #CyberAware #CyberThreat databreachtoday.com/researcher-str…


Initial Access Brokers (IABs) facilitate network access for attackers by selling access points on the Dark Web. Multifactor authentication and credential monitoring mitigate risk against IAB-driven #ransomware attacks. #Cybersecurity #CyberThreat link-shortener.io/SQKur9RJgCBvPB…


🔥 Is Your Business Fire-Ready? 🔥
Small business owners, picture this: a fire engulfs your business. What's your first move? 🏢
supporttree.co.uk/protect-my-bus…
#report #cyberthreat #cyberrisk #cyberattack #ceo #coo #cto




