Malware: Cuckoo Behaves Like Cross Between Infostealer and Spyware blog.kandji.io/malware-cuckoo… #Pentesting #Malware #CyberSecurity #Infosec


#Ciberseguridad
#Infostealers : 5 tipos de #malware que roban información.
Explicamos qué es un infostealer, cuáles son los tipos más comunes y sus principales características:
welivesecurity.com/es/malware/inf… twitter.com/messages/compo…


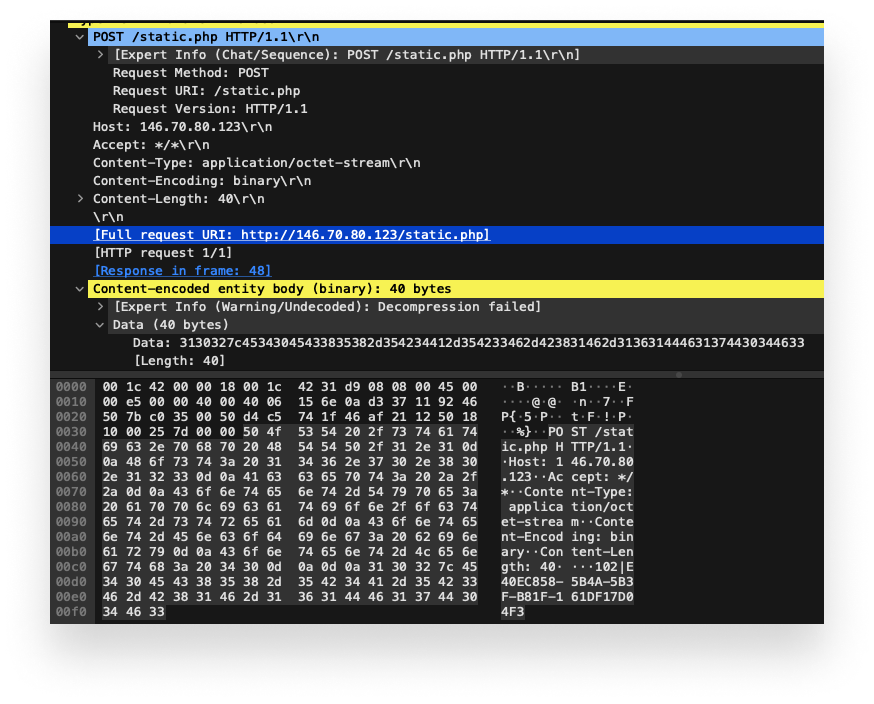
A threat actor has been using a content delivery network cache to store information-stealing malware in an ongoing campaign targeting systems U.S., the U.K., Germany, and Japan.
bleepingcomputer.com/news/security/…
#threatactor #infostealer #cybersecurity #threatresq


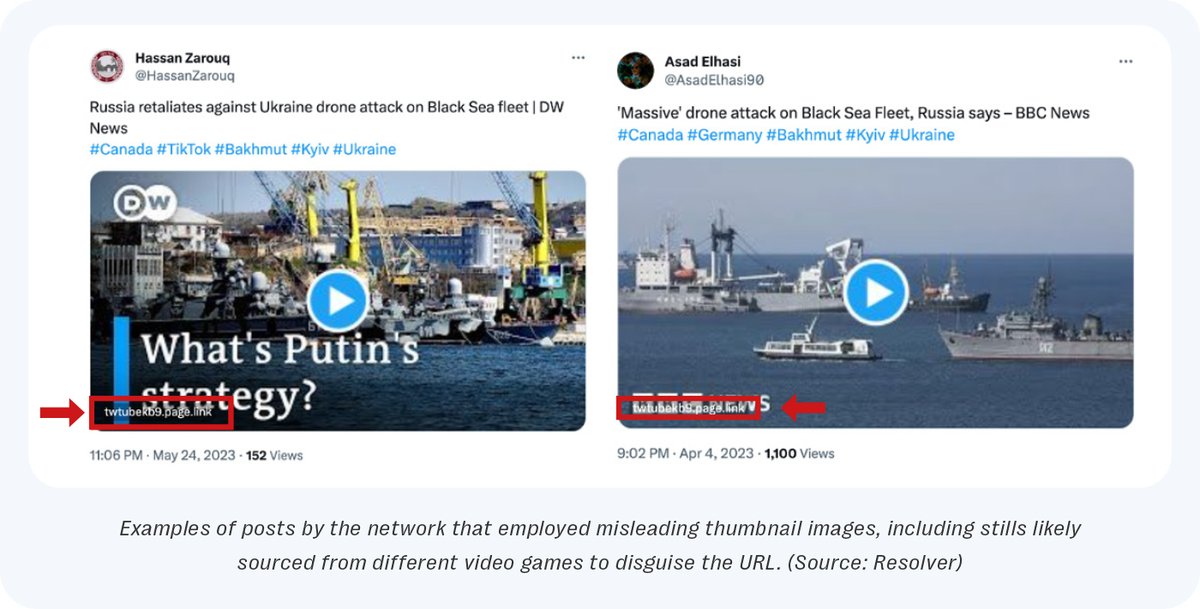
Malware Masquerades as News on Social Media - Unveiling the deceptive tactics employed by a Coordinated network to disguise pernicious Infostealer malware as traditional media coverage of the #RussiaUkraineWar #Investigation
resolver.com/blog/ukraine-w…


cybersecurity-help.cz/blog/3959.html
An ongoing cyber campaign targets victims across multiple countries with the Cryptbot, LummaC2, and Rhadamanthys infostealer malware variants
#CiscoTalos #malware #CoralRaider


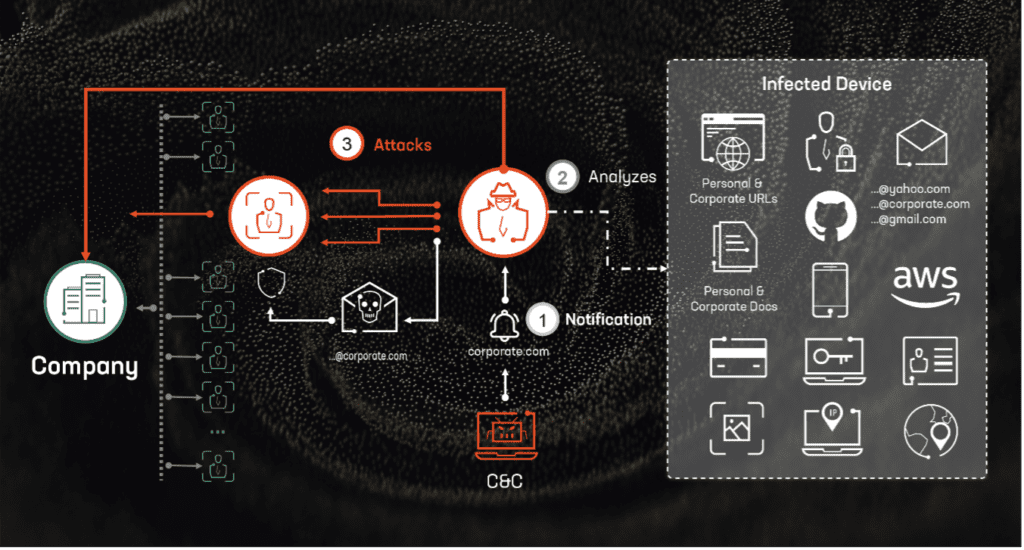
These tactics, including the use of misleading thumbnail images, URL shorteners, targeted hashtags and evocative language were designed to lure users into clicking on the malicious links, leading to the infection of their browsers with #infostealer malware.

▶️Infostealers: malware que roba información
▶️Suelen buscar datos de tarjetas de crédito y credenciales de todo tipo de cuentas: desde redes sociales, correo electrónico y aplicaciones en general
#Ciberseguridad #Infostealer #Malware #Hacking
blog.elhacker.net/2024/04/infost…



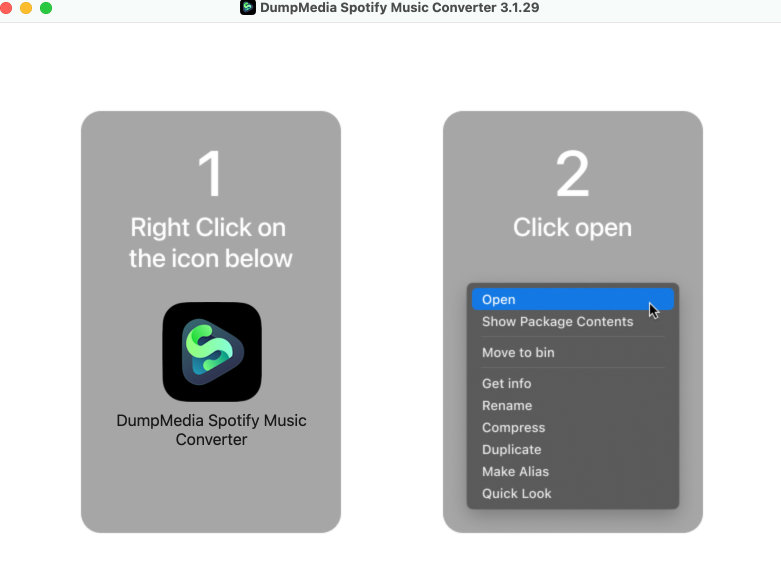
Alright here’s a new blog post for a new macOS malware by Adam Kohler and I!
This was a fun one to reverse: stripped, encoded strings, persistence, and more :)
Enjoy!!
blog.kandji.io/malware-cuckoo…

Last week we identified another new malware “Cuckoo” for #macOS that has Spyware and Infostealer capabilities.
I am proud of the work L0Psec and I did to get this out!
#malware #spyware #infostealer #music #streaming #recoverytools


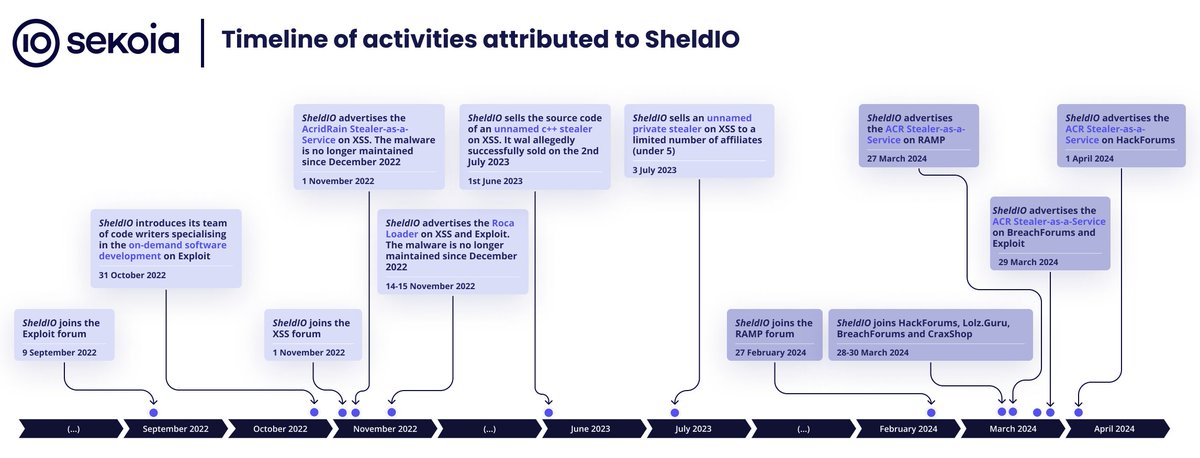
SheldIO has previously sold #AcridRain Stealer, Roca Loader and another unnamed private infostealer, available to only a limited number of affiliates, that we link to GrMsk Stealer.
Here is a timeline of activities attributed to SheldIO between 2022 and 2024.
⬇️

El término infostealer se utiliza para agrupar a distintos tipos de malware que tienen capacidad de robar información. Suelen buscar datos de tarjetas de crédito y credenciales de todo tipo de cuentas bit.ly/3y2m5rh vía ESET Latinoamérica #malware #ciberserguridad #infostealer