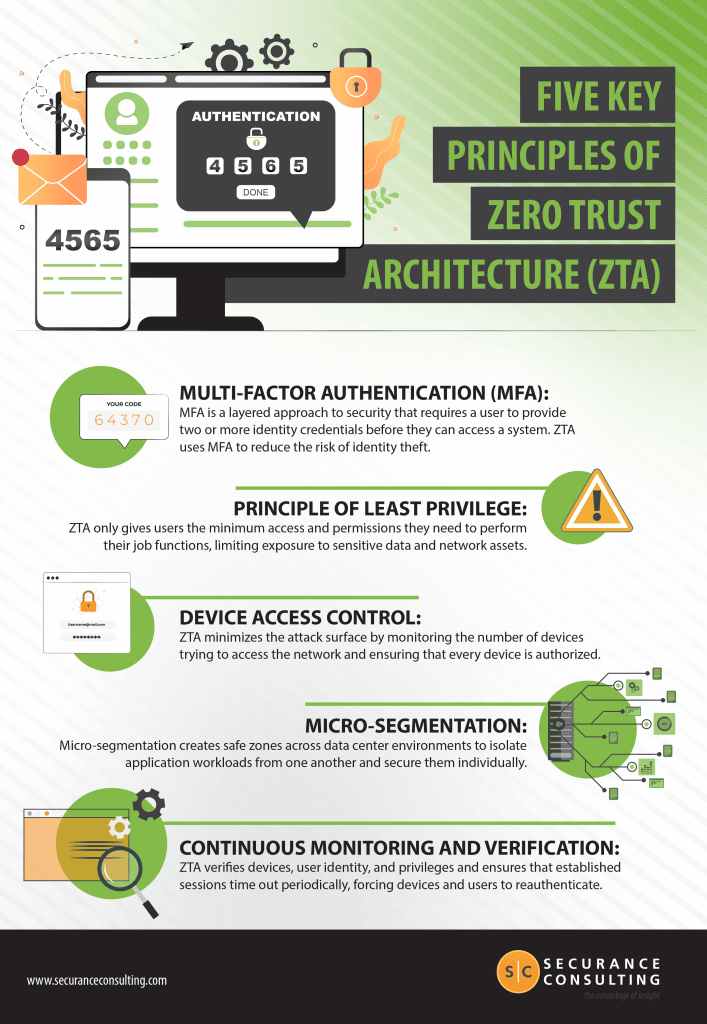
🔒 In today's digital landscape, traditional security models fall short against evolving cyber threats. Embrace Zero Trust Architecture to strengthen your defenses. 🛡️ Learn how to adopt a zero-trust security model and protect your data. 💻
#Cybersecurity #ZeroTrustArchitecture

Why are so many companies launching Zero Trust Architecture (ZTA) initiatives? Because “never trust, always verify' leads to strong authentication, authorization, and encryption methods for all identities.
#ZTA #zerotrust security #zerotrust architecture #zerotrust

You’ve heard a lot about #zerotrust , but did you know that most SaaS applications are well-aligned with #ZeroTrustArchitecture ? If you’re planning to start adopting Zero Trust in your organization, SaaS is an ideal place to start. Read here: hubs.ly/Q023Dlw50



🚨Just learn about the importance of 🔒 Zero Trust Architecture for Industrial IoT security. Check out this FREE industrial resource on #securityict and #industrialcoaching
🔗 securityict.net/resources/
#ZeroTrustArchitecture #IoTsecurity #industrialcoaching #actionplan #IIoT


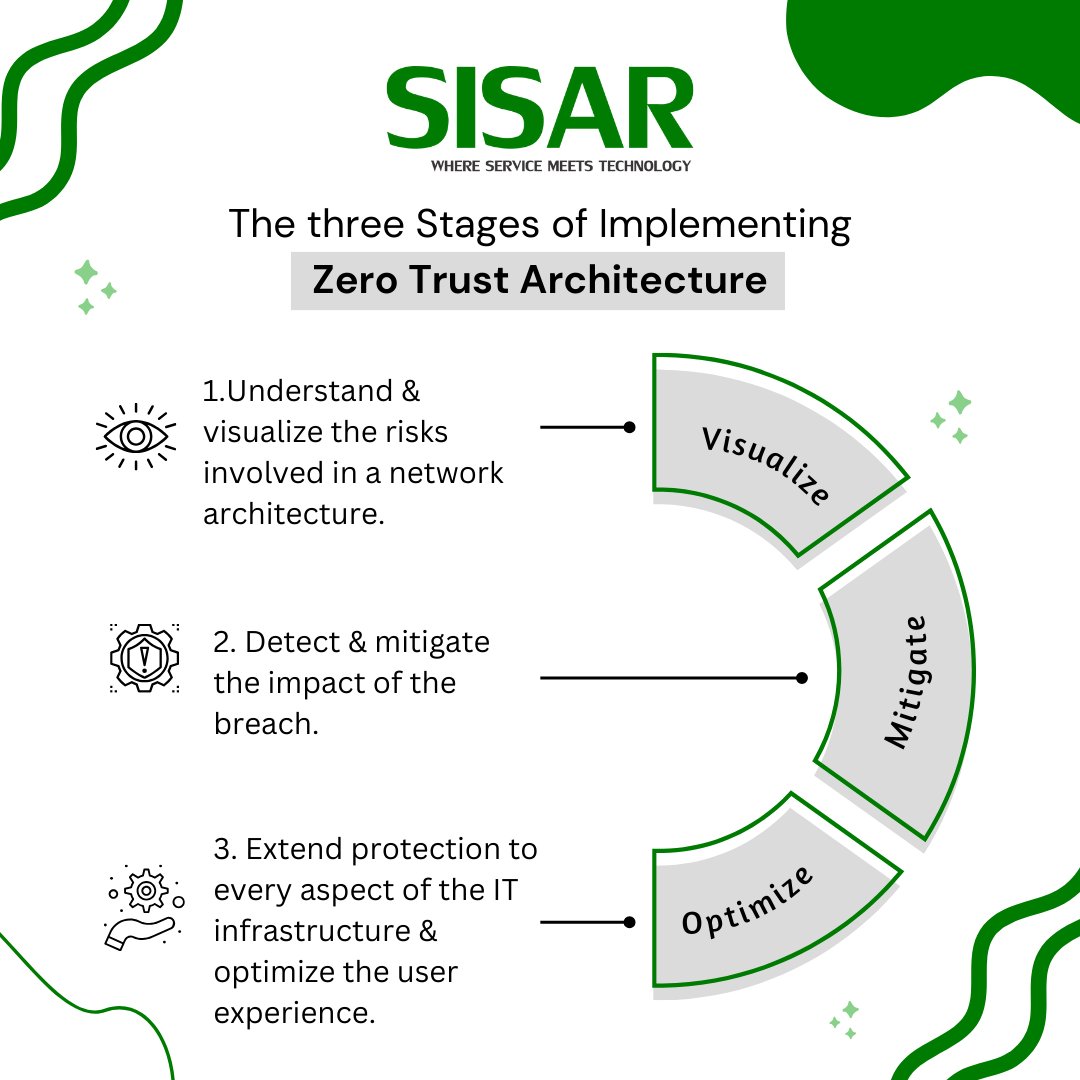
A comprehensive post about the different stages of Zero Trust implementation: visualize, mitigate, & optimize your security strategy to protect your IT infrastructure effectively.
Contact us via: bit.ly/3Pb6pZz
#zta #zerotrustarchitecture #CyberSecurity #DataSecurity

Skillmine’s #cybersecurityservices can provide your business with a robust, flawless, & secure infrastructure.
Follow Skillmine Technology Consulting
#zerotrustsecurity #zerotrustarchitecture #cybersecuritystrategy #cyberthreat #cybersecurityservices #cybersecurityexpert #Skillmine


Introducing #AWS VerifiedAccess for general availability! This is an important step for #ZeroTrustArchitecture as it enables organizations to secure access to their workloads and resources on AWS. #AWS #CloudSecurity
buff.ly/42gGDq8


Join our #webinar tomorrow at 7am PT for a technical overview of our #ZTNA solution BlastShield. Our solution helps companies in #manufacturing and other sectors meet the federal requirements of #ZeroTrustArchitecture . Register now: hubs.ly/Q01yXhpm0


What measures can organizations take to defend against #ransomware ?
CEO Ⓙⓐⓒⓚ Ⓗⓘⓓⓐⓡⓨ speaks with Bank of America's Haim Israel about how #ZeroTrustArchitecture and strong #encryption are crucial to protect organizations against current and future #AI and #quantum threats.

Q: What keeps you up at night?
A: Where are the vulnerabilities in your supply chain?
#SupplyChain #Blockchain #ZeroTrustArchitecture
#Resilience #NationalSecurity Geeq
Morpheus.Network


Read URM’s blog, in which we drill down into the #PCIDSS v4 requirements around forced password changes, with a particular focus on the inclusion of #ZeroTrustArchitecture , what it is, and whether its implementation is right for your organisation:
urmconsulting.com/blog/pci-dss-v…
#PCIDSS


CASE STUDY: IMPLEMENTING TRUST ARCHITECTURES AND DIGITAL IDENTITY IN THE RETAIL INDUSTRY
kiktronik.com/case-study-imp…
#ZeroTrustArchitecture #ZTA #GoogleBeyondCorp #CyberArk #DigitalIdentity #MicrosoftAzureActiveDirectory #Blockchain #PrivacyEngineering #HashiCorpVault #technews



We also got tired of this question, so we created EZSSH! #zerotrust #zerotrust security #zerotrust architecture #pki #passwordless #passwordless authentication

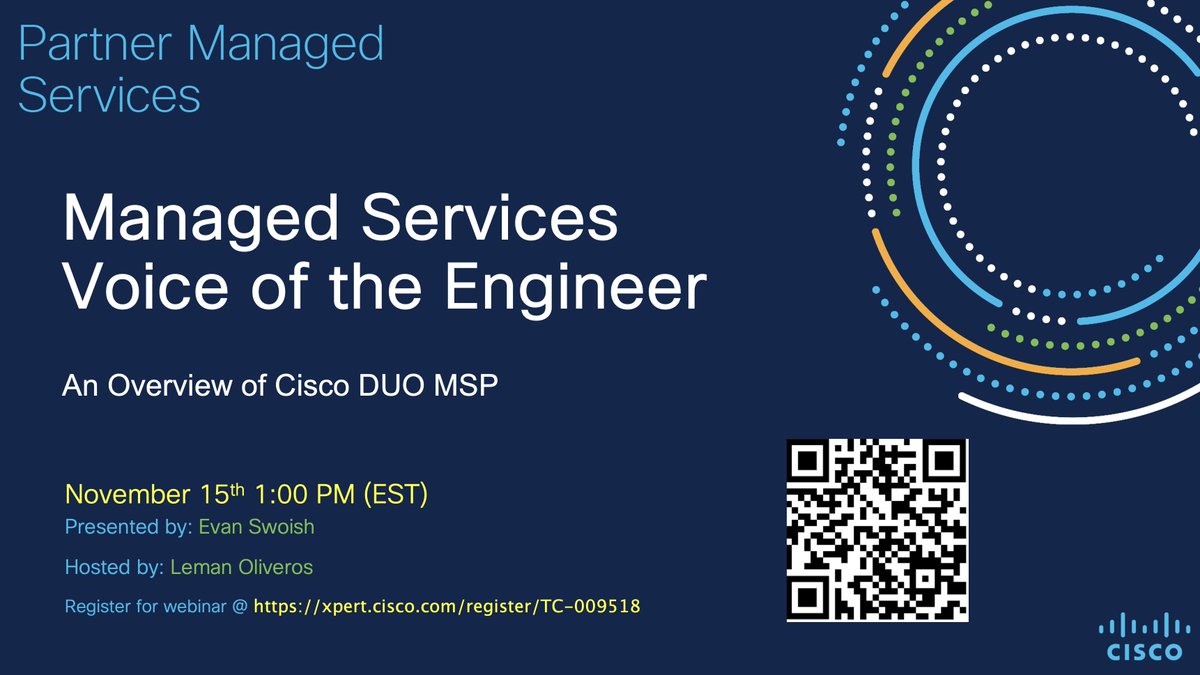
📢 Join us for the Managed Services Voice of the Engineer webinar on Nov 15th, 1:00 PM ET (10:00 AM PT). Get insights into Cisco DUO MSP, a crucial part of Zero Trust architecture.
Register here: cs.co/6013uctLN
See you there! #CiscoDUO #GoManaged #ZeroTrustArchitecture

Just under 2 weeks until #VMwareExplore where I will be joined by Martin Kniffin, Peter Björk, and #NIST ’s own Murugiah Souppaya to discuss #ZeroTrust projects and the work we have done with Cybersecurity @ NIST NCCoE on putting #ZeroTrust Architecture into practice.
event.vmware.com/flow/vmware/ex…


By embracing ZTA, banks can enhance their security, reduce breach risks, and much more.
Watch our latest on-demand webinar to discover how ZTA can strengthen your cybersecurity framework: hubs.ly/Q02rXZ6T0
#Zeta #NextGenProcessing #ZeroTrustArchitecture #Cybersecurity


Up to 💲250,000 for User and Entity #BehaviorAnalysis ( #UEBA ) technology that may enable the implementation of the #USArmy ’s #ZeroTrustArchitecture while improving the tactical network’s #cybersecurity posture.
Apply here: spr.ly/6013nqao9
#ArmyTech #SmallBusiness