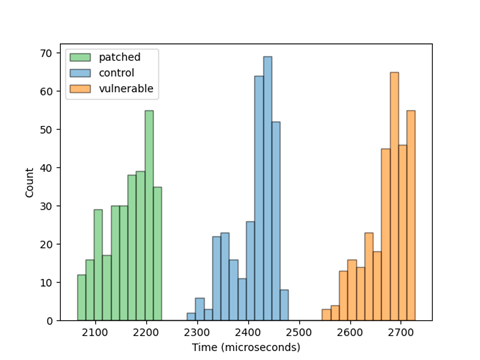
[Akamai Bypass] Open Redirect to XSS
Open Redirect
/path?next=//evil,com --> redirected to evil,com
Tried XSS
/path?next=javascript:alert(7) --> blocked by Akamai WAF
[1/2]
#BugBounty #bugbountytip s #bugbountytip #vulnerability #infosec #akamaibypass
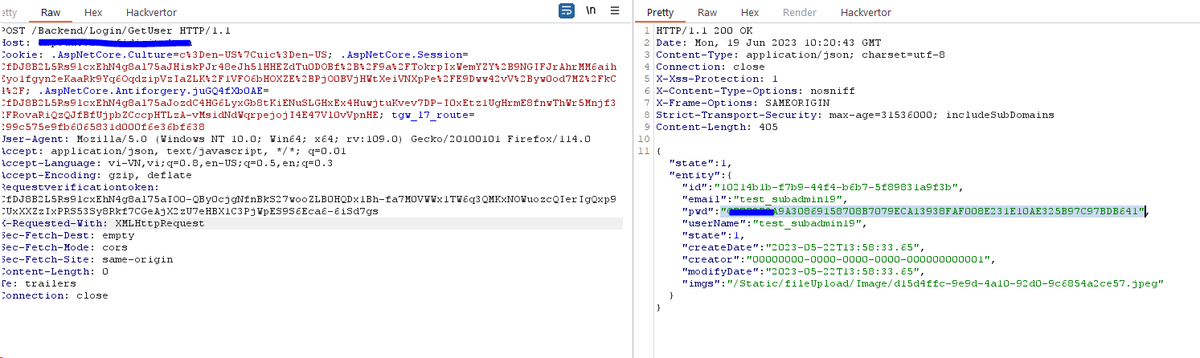
![Jefferson Gonzales (@gonzxph) on Twitter photo 2023-06-16 12:39:50 [Akamai Bypass] Open Redirect to XSS
Open Redirect
/path?next=//evil,com --> redirected to evil,com
Tried XSS
/path?next=javascript:alert(7) --> blocked by Akamai WAF
[1/2]
#BugBounty #bugbountytips #bugbountytip #vulnerability #infosec #akamaibypass [Akamai Bypass] Open Redirect to XSS
Open Redirect
/path?next=//evil,com --> redirected to evil,com
Tried XSS
/path?next=javascript:alert(7) --> blocked by Akamai WAF
[1/2]
#BugBounty #bugbountytips #bugbountytip #vulnerability #infosec #akamaibypass](https://pbs.twimg.com/media/FyvqkS3X0AMO_qL.png)







I addressed the United Nations Human Rights Council 📍 #HRC53 53rd Regular Session, shedding light on the ongoing persecution faced by the Hazara people. I empathised the extra layers of vulnerability faced by Hazara women due to the intersectional factors of gender, religion & ethnicity.
Written statement:…


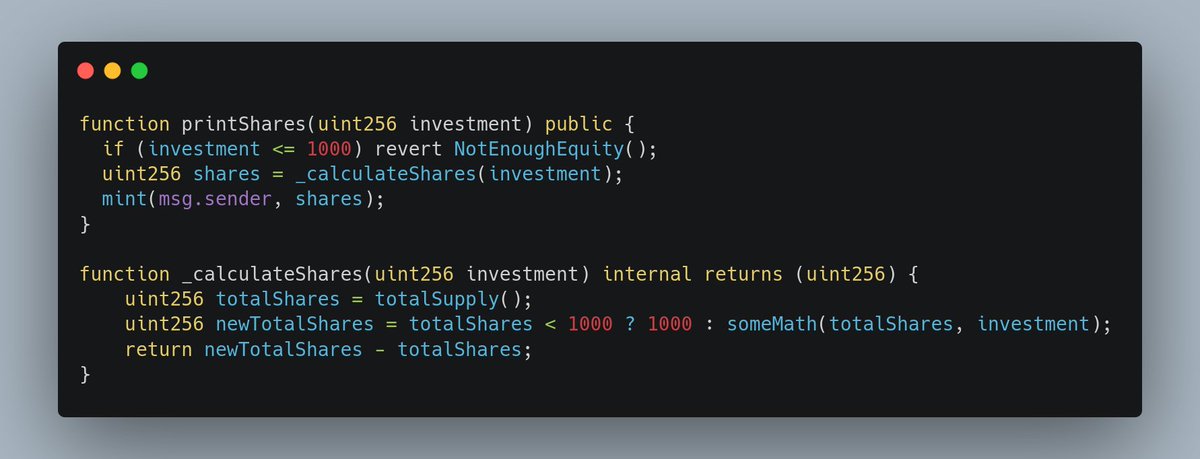
We’ve created a tool to quickly check if a remote #FortiGate firewall is affected by critical #vulnerability #CVE -2023-27997. noperator walks through the design of the timely #vulnerability assessment tool in this write-up. #infosec bfx.social/3pbdEGj



It is an honour that my research at Land Economy on reducing the vulnerability of open spaces to extreme conflict and violence in Nigeria received the 2023 CSAR PhD award for outstanding research at @cambridge_Uni from the pro-VC Prof. Andy Neely
#ThinkingNigeria #Nigeria










My brilliant team at Bishop Fox developed a safe, no-crash vulnerability check for the recent CVE-2023-27997 heap overflow in FortiGate firewalls allowing RCE. You can try the tool out yourself at github.com/BishopFox/CVE-…. Check out the blog, too! Clever technique, worth a read.