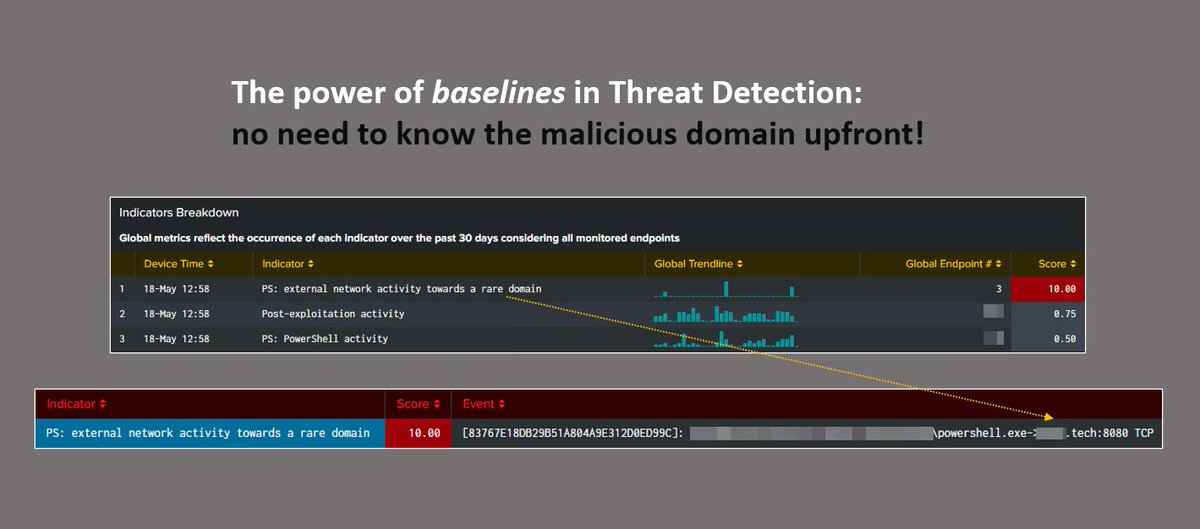
For as advanced and clever a sample as this is, these strings of '111111' as command line arguments are an easy custom detection to write #threathunting #detectionengineering

Intro to Detection Engineering - I have just completed this room! Check it out: tryhackme.com/room/introtode… #tryhackme #security #detectionengineering #blueteam #mitre #ADS #introtodetectionengineering via @realtryhackme

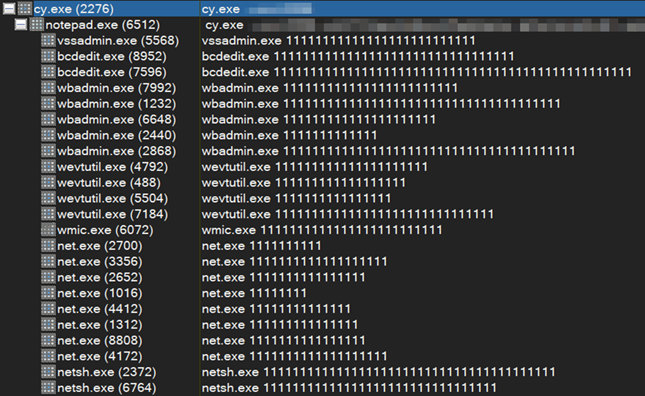
Winlogbeat is amazing. I did a small test in my home lab to parse event_data.GrantedAccess field into the Access Masks at the client side and it worked really well. I’ll write a blog and share the details. Here is how it looks like
#ThreatHunting #DetectionEngineering Elastic
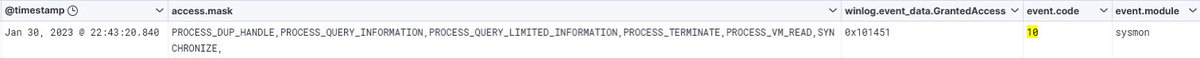

Powershell caret obfuscation with a .net reflection cradle that LOOKS like Cobalt Strike…but is really just a botnet?!? I dunno if I trust that assessment…. #DetectionEngineering #ReverseEngineeringMalware #LazyTrojan


Join us at #TezDev2023 in Paris on July 21! 🫵 Dive into a day of knowledge-sharing and collaboration. Use 'Tez0sEarLy1' at checkout for early bird discounts!



Intro to Detection Engineering - I have just completed this room! Check it out: tryhackme.com/room/introtode… #tryhackme #security #detectionengineering #blueteam #mitre #ADS #introtodetectionengineering a través de @realtryhackme


Intro to Detection Engineering - I have just completed this room! Check it out: tryhackme.com/room/introtode… #tryhackme #security #detectionengineering #blueteam #mitre #ADS #introtodetectionengineering via @realtryhackme #CyberSecurity #infosec #infosec urity



Read the interview with our passionate #ThreatBounty developer Aung Kyaw Min Naing sharing expert tips on Sigma rules writing and emphasizing the transformative power of collective cyber defense in tackling industry challenges.
socprime.com/blog/interview… #detectionengineering


Intro to Detection Engineering - I have just completed this room! Check it out: tryhackme.com/room/introtode… #tryhackme #security #detectionengineering #blueteam #mitre #ADS #introtodetectionengineering via @realtryhackme


My article about using chatGPT for threat detection is out
securelist.com/ioc-detection-…
#chatgpt #dfir #detectionengineering #ioc #incidentresponse

🔥👀Think TryHackMe is just for Red Teamers? Think again!👀🔥 💻🔍TryHackMe offers great introductory training for Detection Engineers.🔍💻 Check out some of my favorites:
#DetectionEngineering #CyberSecurity #TryHackME

Let’s get into some analysis techniques shall we?🛡️📊 #DetectionEngineering #Cybersecurity

New room Intro to Detection Engineering from TryHackMe :
Introduce the concept of detection engineering and the frameworks used towards crafting effective threat detection strategies.
tryhackme.com/room/introtode…
#tryhackme #detectionengineering



Detect:
- Double extensions (pdf.lnk)
- Wscript -> vbs with IWR to non-standard IP address format
- Long PS command with '.replace' in it
- Run Key with obfuscated PS containing 'HKCU'
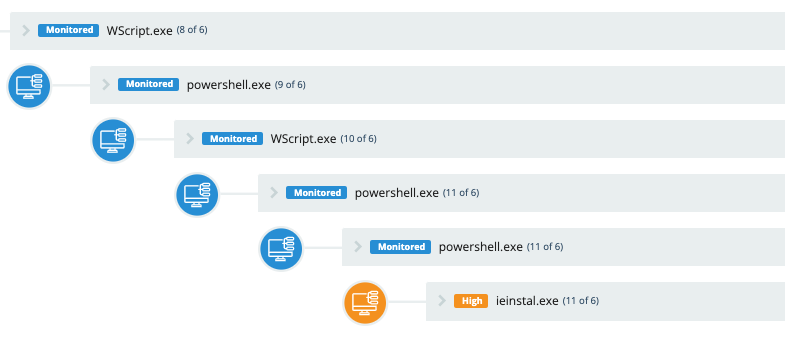
- This very long and interesting process tree has some options also 😀
#detectionengineering

“Play with Splunk | Sigma Rule Project — Custom REST Endpoint” by Burak Karaduman #splunk #siem #sigmarule #detectionengineering
link.medium.com/sFWi0xzMZyb


Threat Hunting allows for greater flexibility in data analysis to find activity that would be too noisy for detections. The diagram in this article does a great job of displaying the relations and outputs between #ThreatHunting and #DetectionEngineering .

And zip TLD started to be exploited! Tracking DNS and Web Proxy logs will give you some visibility ✨ #CTI #ThreatIntel #Splunk #DetectionEngineering