Stay in front of #cybersecurity trends with ISC2 Cloud Security Skill-Builders. Stop bad actors in their tracks with fast learning available on demand.
Get started: ow.ly/hyQL50RiFKW
#CloudSecurity #SkillBuilders


Cybersecurity journey so far. ISC2 physical exam in few days.
Cyber Security Challenge UK Cyber Caramel_Choco🍫 CyberPatron ©



FREE Webinar - Wednesday, May 1 at 1 pm ET
Join Steve Piper, CISSP, CEO & Founder, CyberEdge Group for the Exploring Five Emerging Cybersecurity Defenses webinar.
Register Now: ow.ly/PFo850R83xh
#ISC2Events #ISC2Webinar #CybersecurityLeadership


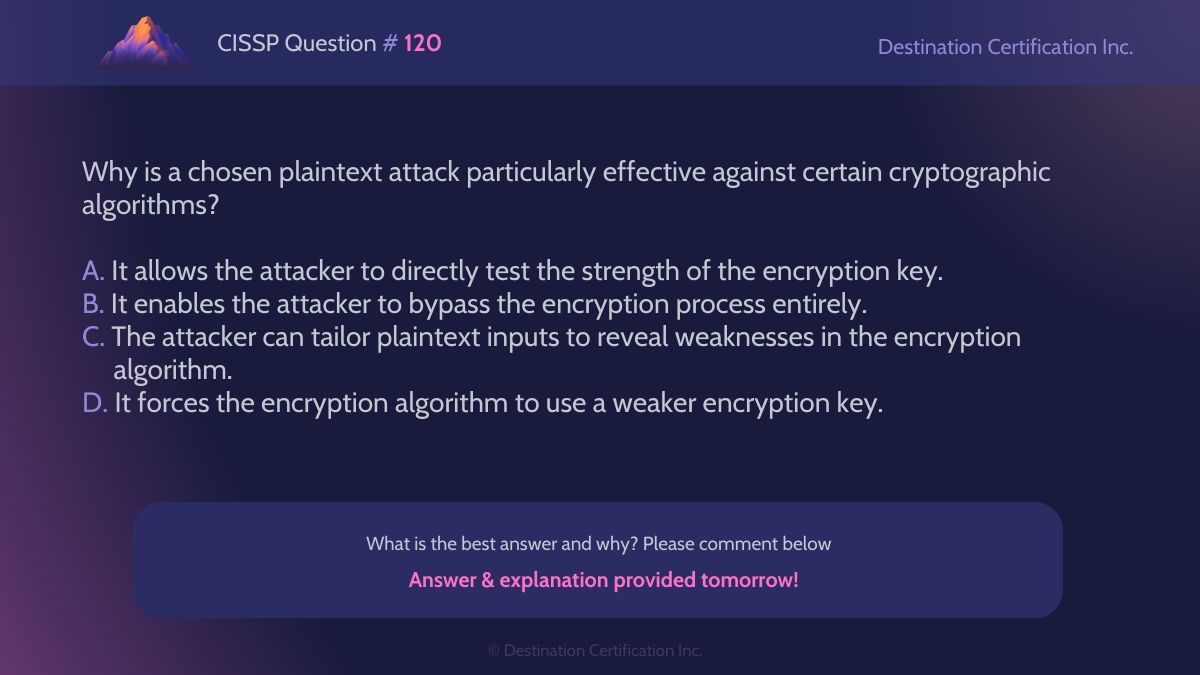
#CISSP Question #120
Analyze the information and question at hand, then let us know your answer in the comments.
We'll post the answer tomorrow with a full explanation. Follow us to see it!
#WeeklyCISSPChallenge #QuestionOfTheWeek #CyberSecurity #CISSP practice #ISC2



Generative #AI making big impact on #security pros, to no one's surprise
buff.ly/3Tdu64Q
CSOonline ISC2 #cybersecurity #infosec #tech #business #leadership #management #recruitment #jobs #skills gap #skills #talent #security jobs #CISO #CIO #CTO #genAI #generativeAI







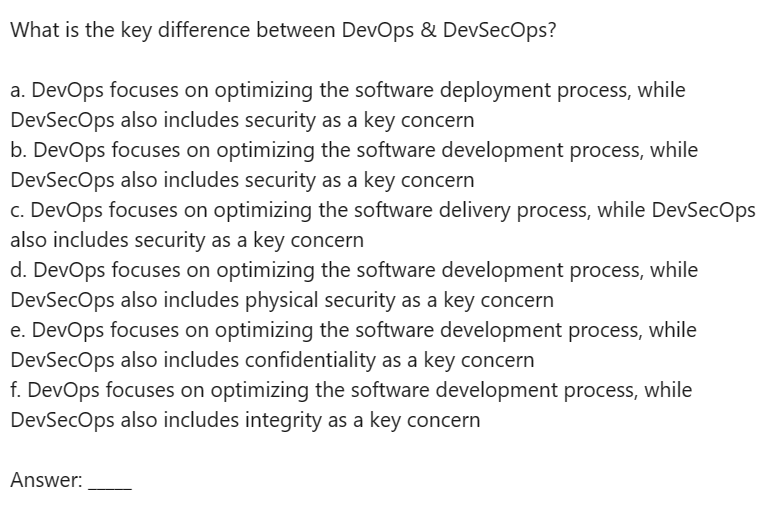
#CISSP Question #119 Answer and Explanation
Here is the answer and an analysis of how to reach the correct answer. If you want to see more content like this, do let us know!
#WeeklyCISSPChallenge #QuestionOfTheWeek #CyberSecurity #CISSP practice #practicequestions #ISC2