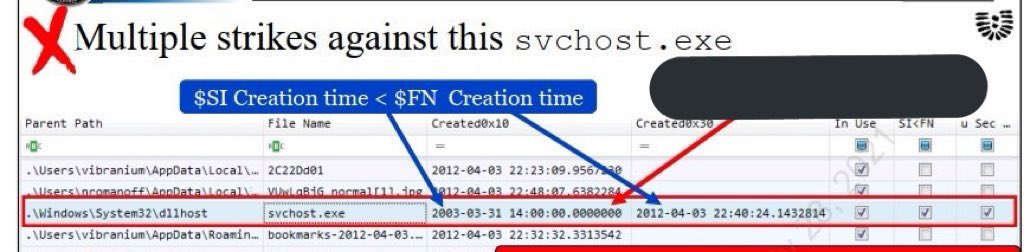
Just released a post covering timestomping as an anti-forensics technique! I dig into the implementation as well as detections. Big thanks to my team SpecterOps for pushing me to look into defense as well as offense 💜
posts.specterops.io/revisiting-ttp…



Skillful attackers use #timestomping to hide malicious files, slowing down detection and response.
Join Kroll on June 15th to learn how to detect timestomping using Kroll Artifact Parser and Extractor ( #KAPE ).
#cyberrisk #cyberthreat
bit.ly/3LRMvNZ


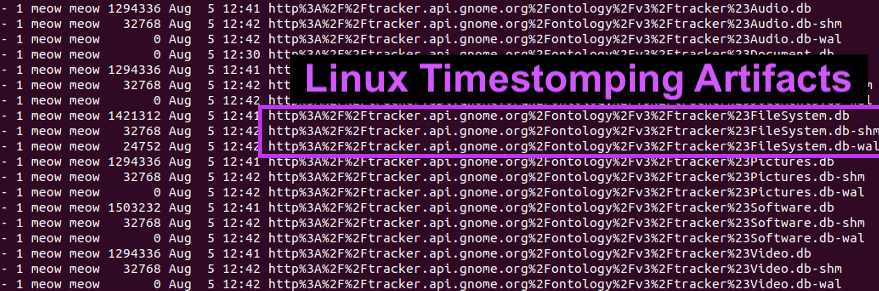
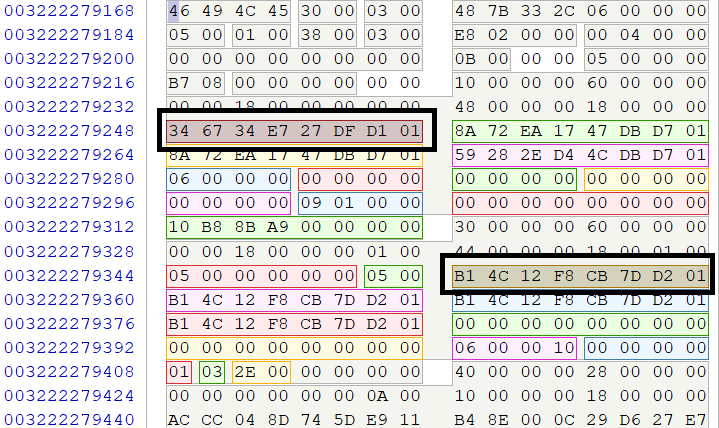
#RedTeamTip If you're ever on a linux box and want to hide the fact you modified a file, here's a basic timestomping example.
#tradecraft



In our new series covering sophisticated anti-forensic tactics, our #cyberrisk expert Andrew Rathbun dives into timestomping, how threat actors are using it and how to detect it on a compromised system.
Learn more: bit.ly/3zAJwGW
#cyberthreat #cybersecurity



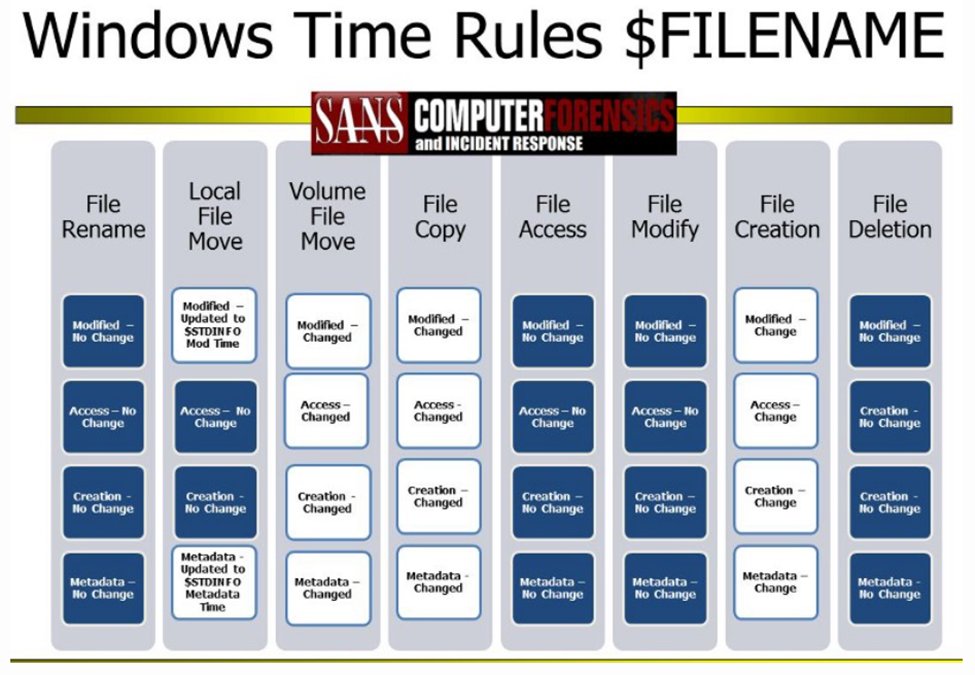
In this insightful webinar, our #cyberrisk expert Andrew Rathbun demonstrates how to use Kroll Artifact Parser and Extractor ( #KAPE ), MFTECmd and Timeline Explorer to acquire, parse and analyze an $MFT file to detect #timestomping .
Watch the replay here: bit.ly/3aiCegS





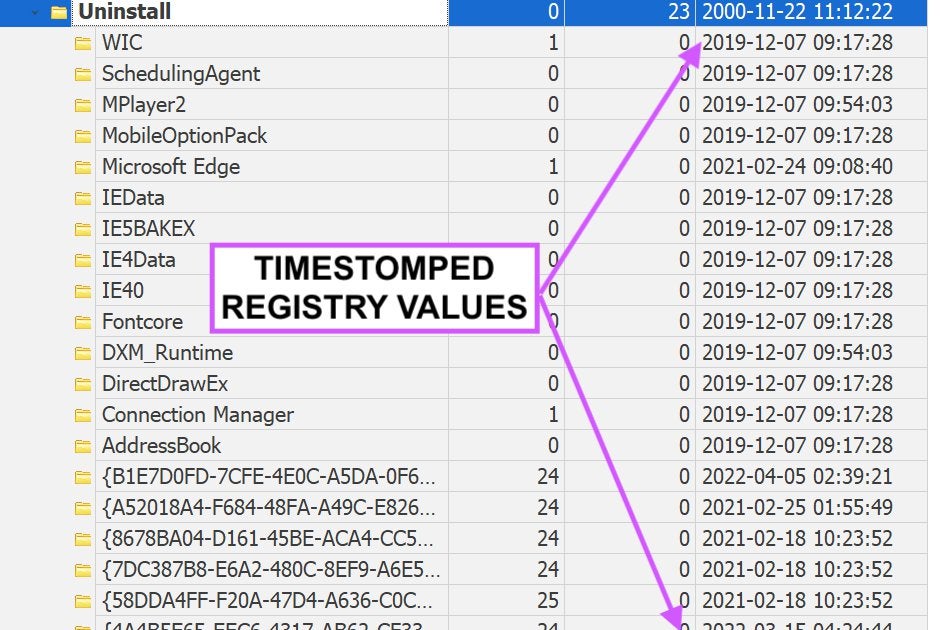
Great list of adversarial defense evasion techniques listed. But it’s a logging article after all, so let’s not forget the most obvious TTP of all - log tampering via wiping or timestomping
New The White House CyberSecurity Executive Order mandates log integrity monitoring (Sec8b)