Rahul Maini
@iamnoooob
Research at @httpvoid0x2f @pdiscoveryio
ID:2897791291
https://blog.noob.ninja/ 12-11-2014 17:35:54
764 Tweets
14,1K Followers
2,3K Following



🚀 Just released our in-depth analysis of CVE-2023-22527, a critical RCE vulnerability in Atlassian Confluence Data Center & Server. 🛡️ Don't miss out on our findings and learn how to detect and protect your systems! 🔍 blog.projectdiscovery.io/atlassian-conf…
#cybersecurity #CVE #RCE …


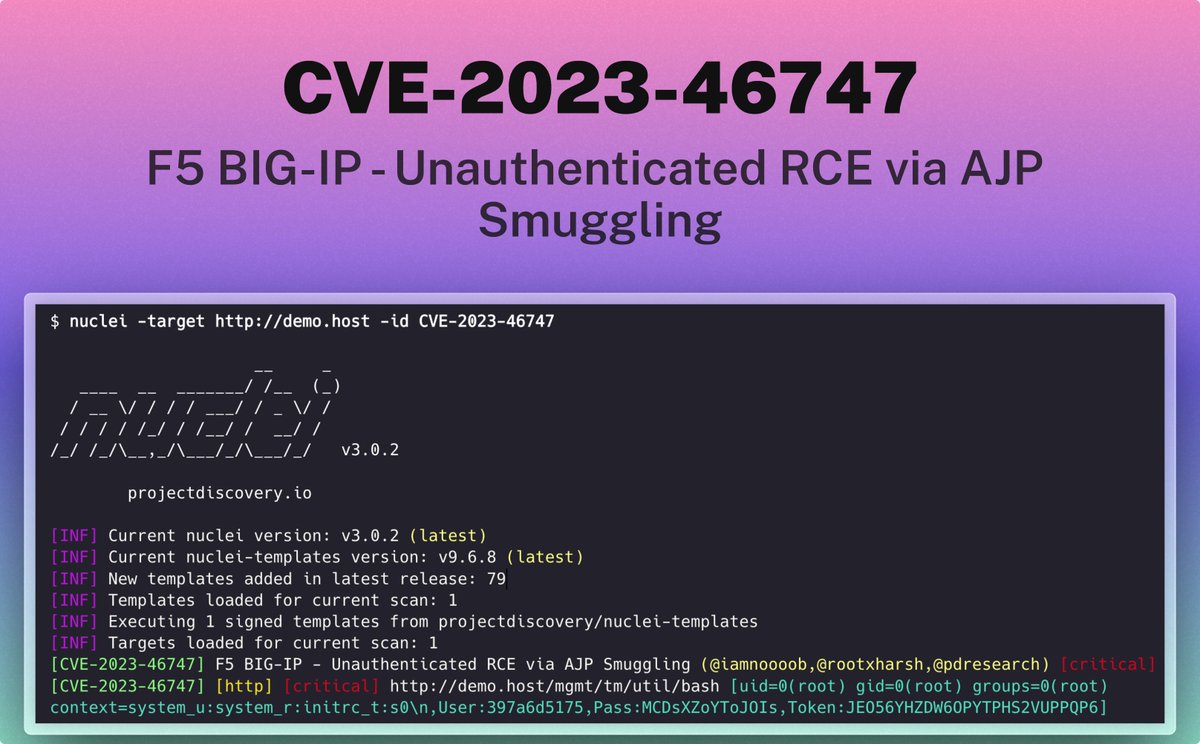
Given that nuclei has posted a full PoC for CVE-2023-46747, we're sharing the full F5 RCE blog post now. Link is praetorian.com/blog/refresh-c…. Shout outs to Rahul Maini Harsh Jaiswal for getting the PoC in < 72 hours and to OrangeTsai for the inspiration! #f5 #cve202346747 #nuclei

Scan for F5 BIG-IP - Unauthenticated RCE via AJP Smuggling (CVE-2023-46747) using nuclei templates shared by Rahul Maini Harsh Jaiswal
Template - github.com/projectdiscove…
Analysis - praetorian.com/blog/refresh-c… by Praetorian
Advisory - my.f5.com/manage/s/artic……




The security research team at Assetnote found and reported a critical pre-auth RCE vulnerability to Metabase earlier this month CVE-2023-38646:
blog.assetnote.io/2023/07/22/pre…
This one was an incredibly fun discovery as there are many roads to RCE through JDBC. We've published details…



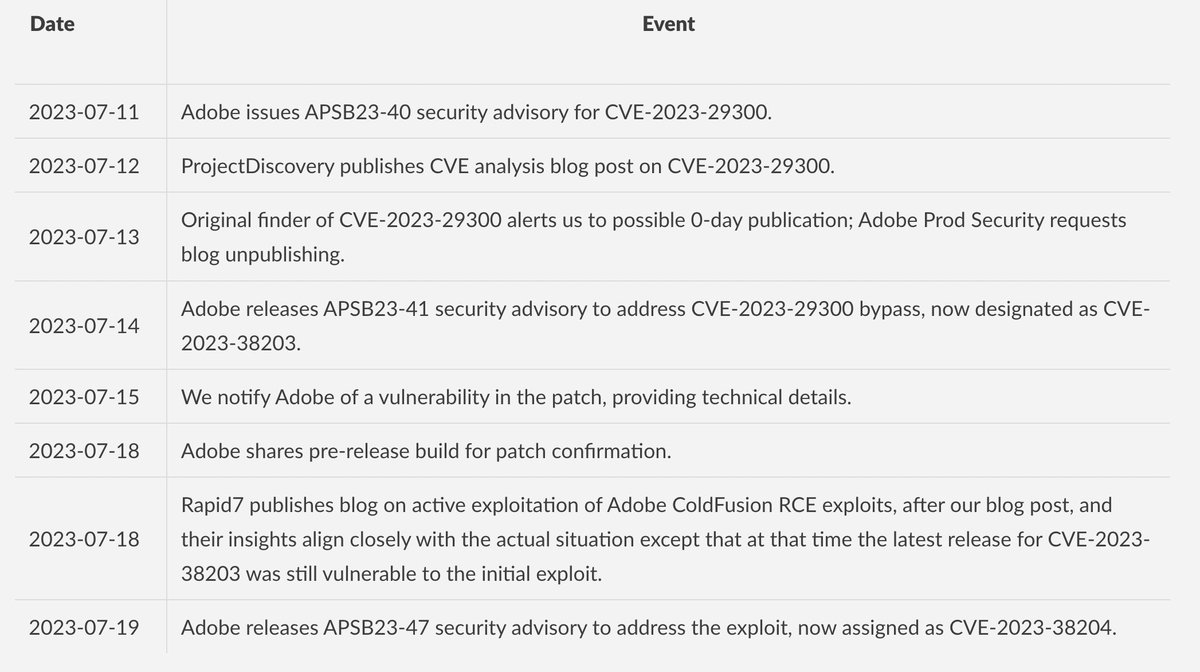
🔐 What a week in #cybersecurity ! We accidentally published a 0-day, quickly pulled it at Adobe's request, and now, with Adobe's hard work, the issue is finally fixed.
🛠️ We're bringing our blog post back online to share our journey with CVE-2023-29300 and its patches. Curious…



📚 Dive into our new blog analyzing the Adobe ColdFusion Pre-Auth Remote Code Execution vulnerability (CVE-2023-29300).
Visit 👉 blog.projectdiscovery.io/adobe-coldfusi…
Also, check out our nuclei template for effective vulnerability detection.
#AdobeColdFusion #Cybersecurity #CVEanalysis …


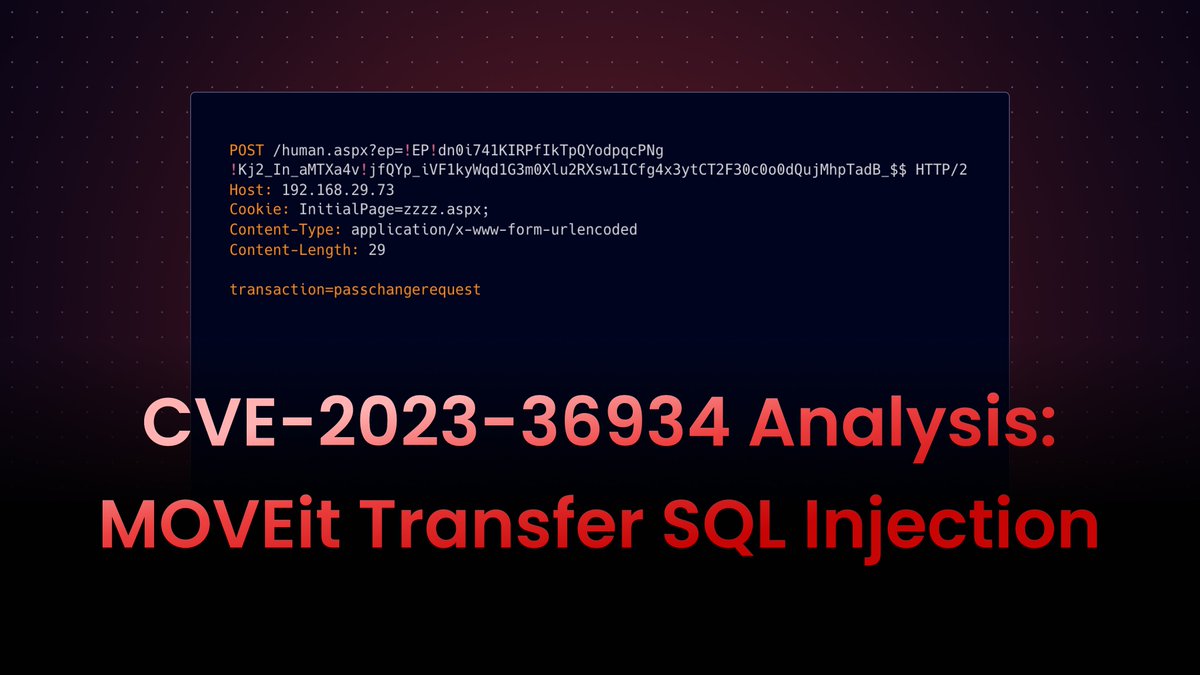
I and Rahul Maini reproduced this latest CVE of Moveit (CVE-2023-36934). This is pretty neat finding, props to original finder.

📚 Learn about the MOVEit Transfer SQL Injection vulnerability (CVE-2023-36934) in our latest blog.
Plus, we've also released nuclei template to detect and aid quick mitigation.
blog.projectdiscovery.io/moveit-transfe…
#MOVEit #Cybersecurity #hackwithautomation