
Breaking the Silence: The Unseen Risks of Bluetooth Vulnerabilities.
.
#crawsec urity #crawacademy #crawsec #BluetoothSecurity #WirelessThreats #CyberSecurity #BluetoothVulnerabilities #DataBreach #IoTSecurity #CyberAttacks #HackingBluetooth #WirelessIntrusion #SecureConnections

Empower Network Security with ZEXMTE Bluetooth Adapter 5.1: Windows & Kali Linux Support, 492ft Range, Apple BLE Spoofing. Unleash Testing Potential! 🛒 amzn.to/44teyfG via t.me/PentestingShop…
#BluetoothSecurity #cybersecurity #infosec #pentesting #redteam


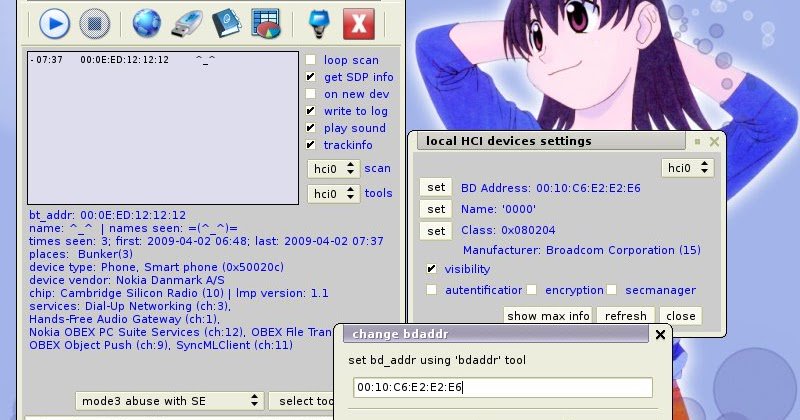
BlueMaho v090417 - Bluetooth Security Testing Suite goo.gl/RwYtQG #BlueMaho #Bluetooth #Bluetooth Security

Boost your cybersecurity: Disable Wi-Fi and Bluetooth when not in use on your smartphone to minimize the risk of unauthorized access.
.
.
#CybersecurityTip #SecureSmartphone #WiFiSafety #BluetoothSecurity #ProtectYourDevice #DigitalSafety #TechSecurity #CyberAwareness #Device

Unlock the secrets of Bluetooth LE security! 🛡️🔒 #BluetoothSecurity #quarktwin quarktwin.com/blogs/other/bl…


Bluetooth Vulnerability
'Explore Bluetooth Vulnerabilities & Solutions across Android, macOS, iOS, & Linux.'
read more - varutra.com/bluetooth-vuln…
#BluetoothSecurity #DeviceVulnerability #Android #macOS #iOS #Linux #CyberSecurity #DataProtection
#infosharesystems #varutra


Disable unnecessary Bluetooth connections when not in use to prevent unauthorized access to your devices. #BluetoothSecurity


1/ 🚨 Breaking News in Tech Security: 'Unmasking Bluetooth: The Hidden Dangers in Your Apple Devices' 🚨 #TechNews #BluetoothSecurity #AppleDevices (1/10) #apple #apple event #iPhone 15 #iPhone #iPhone 15 Pro #iPhone 15 ProMax #techtwitter #BrandedFeatures


Unlock the future with our Advanced Fingerprint Lock featuring Bluetooth connectivity! Experience seamless security at your fingertips.
#FingerprintLock #BluetoothSecurity #NewYearNewBeginnings #ZKTecoSmartSolutions #NewYearNewSecurity #ZKTecoSafety #SecureHolidays #ZKTecoSafety


📡 Secure your wireless connections! Learn about Bluetooth security. Follow @mypeakdigitalinc for cybersecurity know-how! #Cybersecurity #BluetoothSecurity 📶

Presale1 wishes you a great and peaceful weekend and invites you to view the new videos we uploaded in the category:
Mobile Telecom Cyber Warfare
lnkd.in/drmUu_WX
#mobilesecurity #mobilexdr #mobileedr #wifisecurity #bluetoothsecurity
linkedin.com/company/presal…

Beware the BlueBorne Attack!
Learn about this airborne threat exploiting Bluetooth vulnerabilities, and safeguard your devices with knowledge and caution.
#BlueBorneAttack #Cybersecurity #BluetoothSecurity #DigitalSafety #InfoSecInsights


Detroit man steals 800 gallons using Bluetooth to hack gas pumps at station
#GasStationHack #BluetoothSecurity #Cybersecurity
buff.ly/3teZUMq


A 2021 study revealed that over 40 to 50 percent of IoT users leave Bluetooth turned on, making their devices vulnerable to malicious attacks.
#AntiDos #BluetoothSecurity #CyberAttack #DDoSProtection


It's Tip Tuesday!
Bluetooth is super convenient, but did you know it can leave your data vulnerable? Keep Bluetooth turned off while it is not in use to keep your personal data more secure.
#BluetoothSecurity


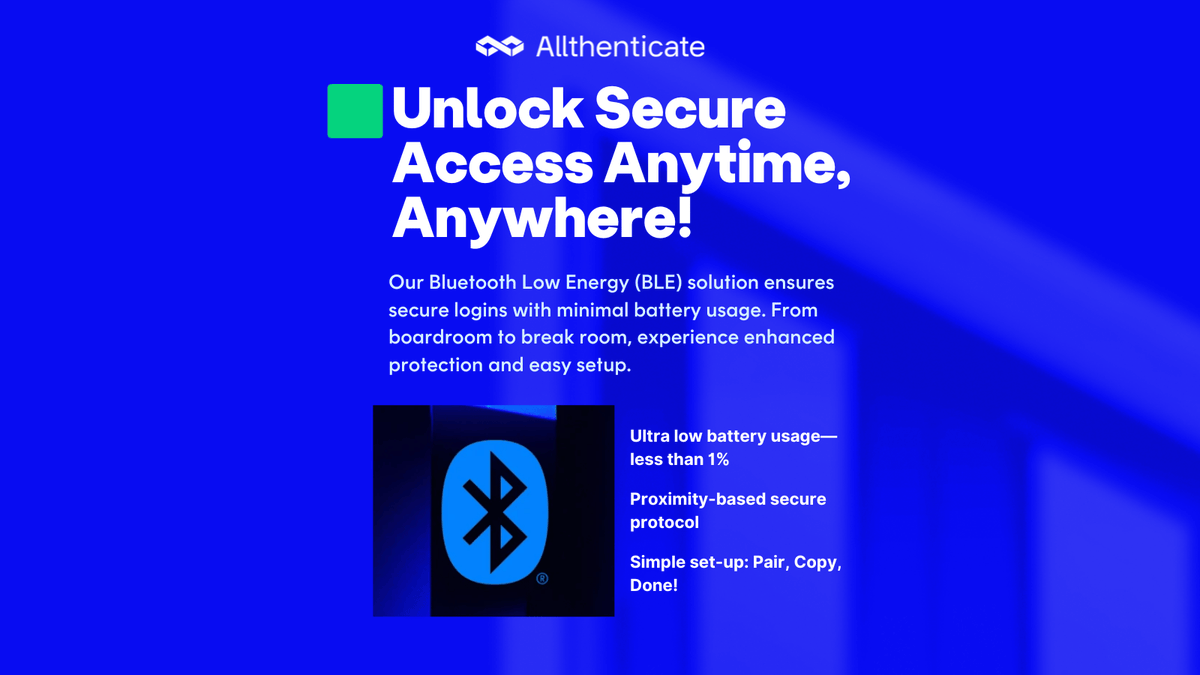
Embark on the next level of security innovation! 🚀🛡️ Our Bluetooth Low Energy (BLE) solution transforms your smartphone into a digital fortress, offering unbeatable protection and peace of mind.
Dive into innovation at allthenticate.com #BluetoothSecurity #SecureAccess

📢 Attention! There's a new article highlighting a critical Bluetooth flaw that allows hackers to take control of Android, Linux, macOS, and iOS devices.
linkedin.com/feed/update/ur…
#BluetoothSecurity #StayProtected #SecureYourDevices #DataPrivacy #ITSecurity


#Bluetooth Not sure whether there is #Bluetooth security when it comes to complicated politics.
But a Bluetooth receiver is a must-have device for #oldcars without Bluetooth stereo, so we can make hands-free calls and voice navigation on the road, for safer driving.

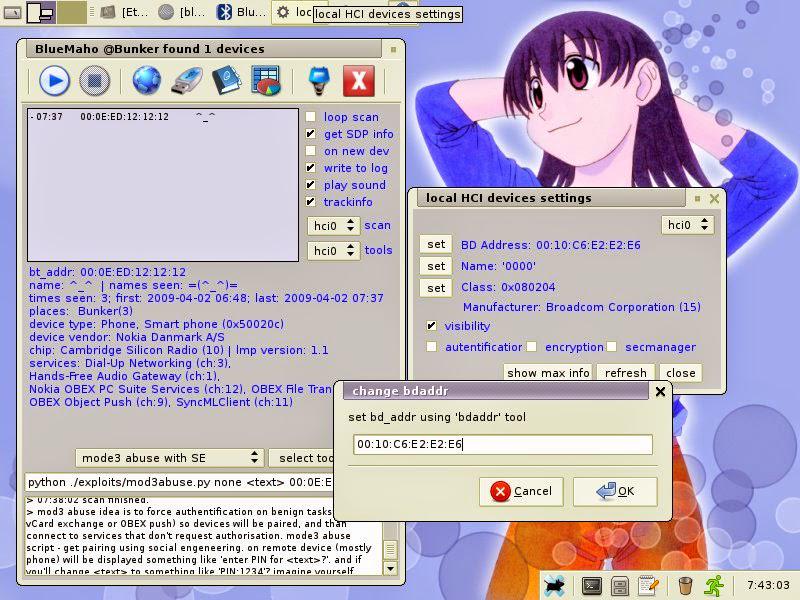
BlueMaho - Bluetooth Security Testing… goo.gl/5ROyYS #BlueMaho #Bluetooth #Bluetooth Security #PenTest #Hack

Love the convenience of Bluetooth? Be wary of Bluesnarfing!
This sneaky cyber attack can compromise your data when you least expect it. Learn how to protect your wireless connections and keep those hackers at bay - tinyurl.com/4nj6hpf4
#BluetoothSecurity
