Today I have a great IT Audit Checklist suggestion for Active Directory❗️🤓 Don't forget to add it to your bookmarks.🤞🏻🌸
PDF Link: media.licdn.com/dms/document/m…
#cybersecurity #infosec #activedirectory #windows #pentest #pentest er #audit #activedirectory security #checklist


Alexa, tell Sainz to sing 'Smooth Operator'😅
Got 6 of 8 flags on the CRTO exam, the last 2 flags I got 25mins too late for submission, I'm smooth like that💪🏾😅
Well detailed course and amazing stable exam lab by Zero-Point Security 👏🏾
Send redteam/pentest roles my way😊



Facing security concerns? Let us assist you!✅
Simply share your security issues with us, and we'll provide expert guidance.
Email us at [email protected] for immediate support.
Protect your business today!🏆
#vulncure #pentest #cybersecurity

Web Application Pentest Lab Setup
Web Application Pentest Lab Setup on AWS
hackingarticles.in/web-applicatio…
Web Application Lab Setup on Windows
hackingarticles.in/web-applicatio…
Web Application Pentest Lab setup Using Docker
hackingarticles.in/web-applicatio…
Configure Web Application Penetration Testing…




Sensitive information disclosure
Tools used: Dirsearch
Path: '/sftp-config.json'
#BugBounty #pentest #bugbountytips







El lado del mal - Un Programa de Formación para usar Inteligencia Artificial en Seguridad Ofensiva & Seguridad Defensiva elladodelmal.com/2024/04/un-pro… Universidad Deusto - Deustuko Unibertsitatea #GenAI #Ciberseguridad #MachineLearning #IA #Hacking #Pentest #RedTeam #pentesting


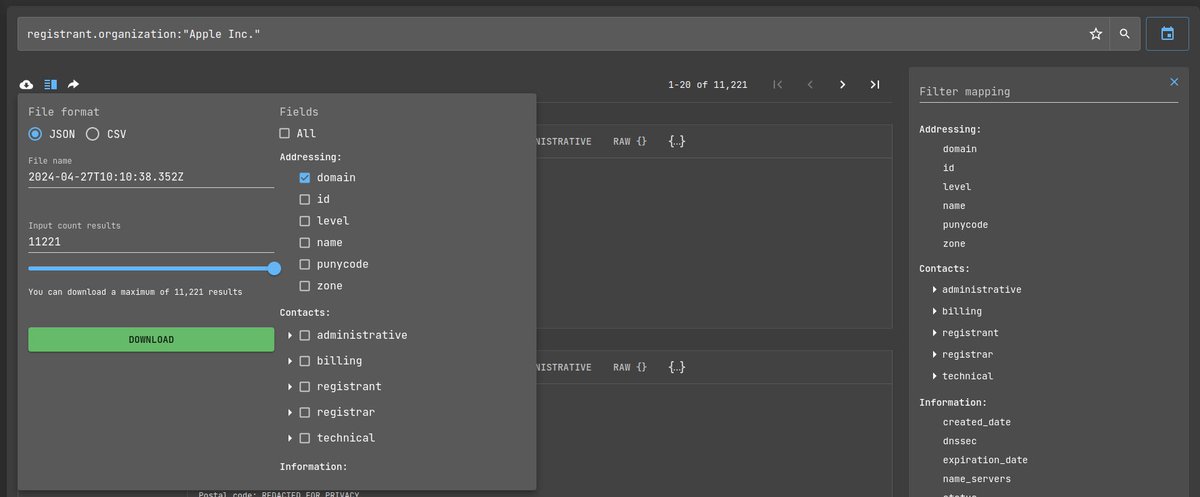
How to find all root domains during reconnaissance with Netlas.io:
registrant.organization:'Organization name'
👉 Read more about recon with Netlas: nt.ls/recon
#cybersecurity #bugbounty #pentest #tips