[Threatview.io] ⚡ Latest collection of #evilproxy domains on #virustotal as seen from our proactive hunter domain telemetry 👇
virustotal.com/gui/collection…
#Threatintel
#CTI
#Phishing
#DFIR
#cybersecurity

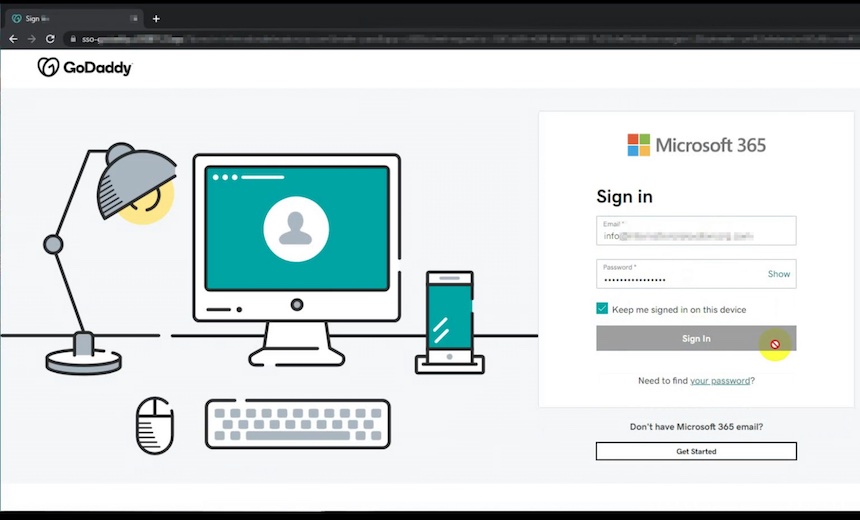
Microsoft 365 accounts of execs, managers hijacked through EvilProxy - helpnetsecurity.com/2023/08/10/evi… - Proofpoint Shachar Gritzman Tim Kromphardt Microsoft Microsoft365 #CyberSecurity #security #InfoSecurity #ITsecurity #CyberSecurity News #SecurityNews #Microsoft365 #phishing



Published: How ‘EvilProxy’ #phishing attack is targeting top-level executives? #cybersecurity #CyberAttack #hacking
buff.ly/3YBVdrq - Technicity Magazine
🟣Tyler Cohen Wood Fawad Khan Greg Valancius Sahba Ferdowsi DO (conciergedoc) Peter Tendekayi Chingonzo Enrico Molinari #CES2024 Avrohom Gottheil Kohei Kurihara - Privacy for all together 🌍 Shane Fogle drhiot




James @AnFam17 Gi7w0rm proxylife Igal Lytzki🇮🇱 So this looks like it might be some #EvilProxy stuff based on behavior. This IP has had so many DGA's stood up over the last few days. all but a few are 0/88 on VT. All samples are 'F12' resistant.
virustotal.com/gui/ip-address…

EvilProxy uses indeed.com open redirect for Microsoft 365 phishing - Bill Toulas
bleepingcomputer.com/news/security/…


EvilProxy phishing malware is once again on the rise⚠️👿
More security info: redfox.ntrigo.com
.
#cybersecurity #nodejs #opensource #Pune #jeru #indiedev #Mentalhealth #SocEnt #Trending #Android #gamedev #HR #Phishing #malware #infosec #Ransomware
siliconangle.com/2023/08/09/ris…

“EvilProxy” Phishing Tool Puts Microsoft Outlook Users at Risk: How to Protect Your Network.
Read more eitex.co.uk/microsoft-365/…
#cyberrisks #cyberprotection #cyberattack #cyberriskmanagement #cyberessentials #microsoft


Some badness to look for in the logs.
If you’ve had users going to rambollmx[.]com - especially since 22nd October - then they’ve probably given their credentials away.
You can check sign in logs for intrusion from 40[.]119[.]40[.]147
#EvilProxy

Detect #phishing by using Any.RUN! 👨💻
Our service detects various phishing-as-a-service platforms such as #storm1575 , #greatness , #evilproxy , and more.
These services are responsible for some of the highest volumes of phishing attacks, which are detected by our

EvilProxy phishing campaign targets 120,000 Microsoft 365 users - Bill Toulas
bleepingcomputer.com/news/security/…

Hundreds of executives are falling for Microsoft 365 phishing attacks, according to new research published by Proofpoint. Read in IT Business Canada about the hybrid campaign using #EvilProxy to target thousands of #Microsoft 365 user accounts. bit.ly/44vLdBs



Not sure what kind of pirate elixir that was, but hey, at least my friend Captain Patches is back! 😊🏴☠️
Thanks Trend Micro Check Point Research Cisco Talos Intelligence Group for the #Rhysida #ransomware research, Shachar Gritzman Tim Kromphardt Proofpoint for #EvilProxy research and Kav