#APT 32 #OceanLotus #Torii #APT #IoT
C&C:
top.haletteompson[.]com threatbook.io/domain/top.hal…
eu-draytek[.]com threatbook.io/domain/eu-dray…
#CyberAttack #Trojans #malware #threatintelligence #threatintelligence
![ThreatBook (@ThreatBookLabs) on Twitter photo 2022-12-07 07:46:31 #APT32 #OceanLotus #Torii #APT #IoT
C&C:
top.haletteompson[.]com threatbook.io/domain/top.hal…
eu-draytek[.]com threatbook.io/domain/eu-dray…
#CyberAttack #Trojans #malware #threatintelligence #threatintelligence #APT32 #OceanLotus #Torii #APT #IoT
C&C:
top.haletteompson[.]com threatbook.io/domain/top.hal…
eu-draytek[.]com threatbook.io/domain/eu-dray…
#CyberAttack #Trojans #malware #threatintelligence #threatintelligence](https://pbs.twimg.com/media/FjW_EHGUYAAuFO_.png)


APT Operation/Group Mid-2022 Summary Report
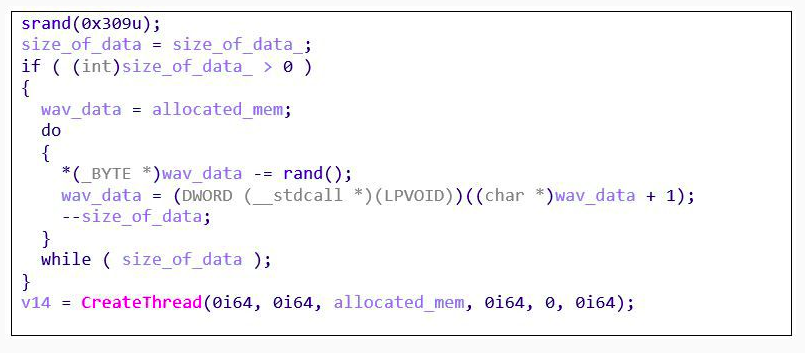
#Oceanlotus use tinyPortMapper forward traffic to Cobaltstrike sever , and New mips-architecture malware named 'Caja' discovered on controlled devices(IOT/Linux).
github.com/blackorbird/AP…

#OceanLotus botnet : Torii/Caja
eu-draytek[.]com
top[.]haletteompson[.]com
mp.weixin.qq.com/s/v2wiJe-YPG0n…
mp-weixin-qq-com.translate.goog/s/v2wiJe-YPG0n…
![blackorbird (@blackorbird) on Twitter photo 2022-11-02 07:45:01 #OceanLotus botnet : Torii/Caja
eu-draytek[.]com
top[.]haletteompson[.]com
mp.weixin.qq.com/s/v2wiJe-YPG0n…
mp-weixin-qq-com.translate.goog/s/v2wiJe-YPG0n… #OceanLotus botnet : Torii/Caja
eu-draytek[.]com
top[.]haletteompson[.]com
mp.weixin.qq.com/s/v2wiJe-YPG0n…
mp-weixin-qq-com.translate.goog/s/v2wiJe-YPG0n…](https://pbs.twimg.com/media/FgivIH4aUAEeUPw.png)

If you are so unlucky to missed our talk at #SASatHome on #PhantomLance relations with #OceanLotus , check out our public report:
securelist.com/apt-phantomlan…
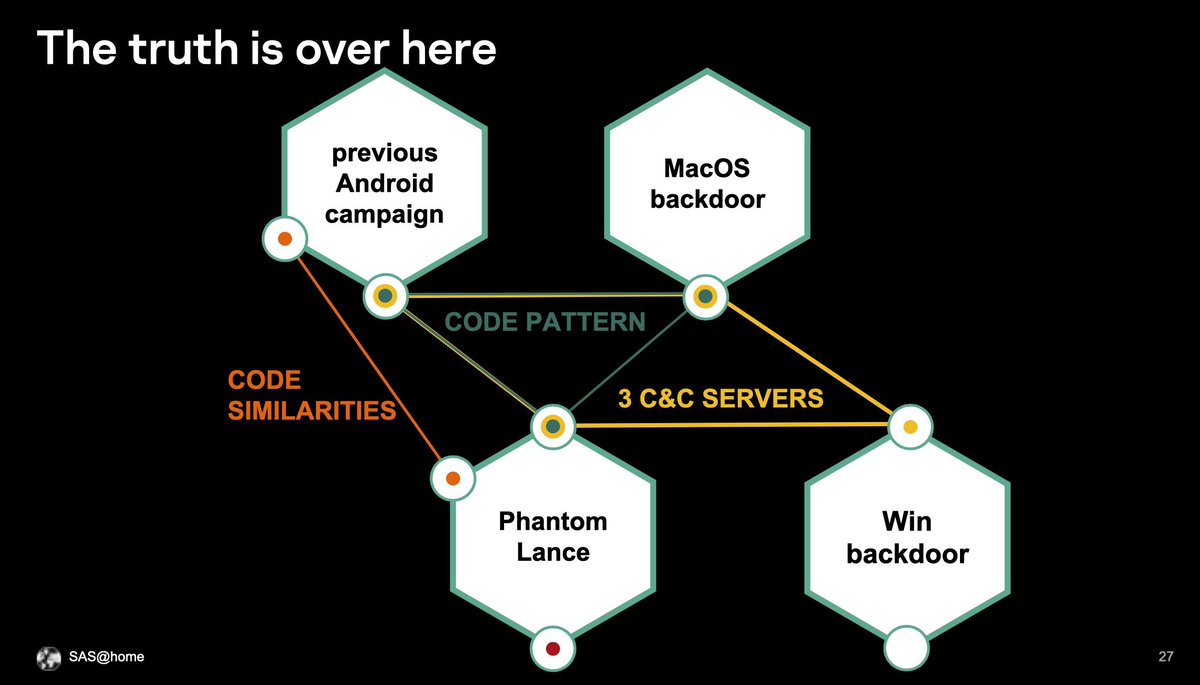


#APT #cybercrime #ThreatIntelligence #ThreatHunting #APT 32
I share some #Oceanlotus IOC.
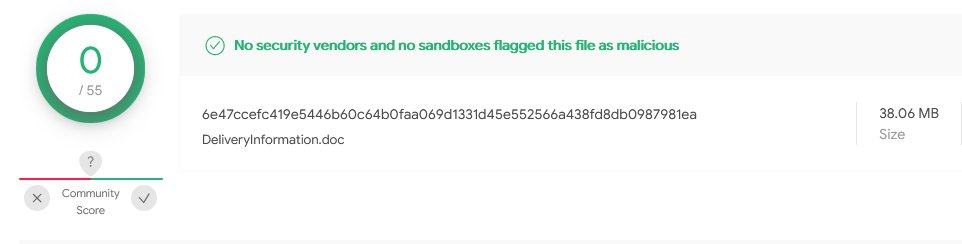
DeliveryInformation.doc, which has some zero detection tag.
Please enjoy it.
docs.google.com/spreadsheets/d…



New IOC of #OceanLotus #APT discovered by our analyst. Keep tracking^
198[.]244[.]207[.]133
Check it out: threatbook.io/ip/198.244.207…
#ThreatHunting #ThreatIntelligence #threats #infosec #cybersecurity #cybercrime #SOC #CTI
![ThreatBook (@ThreatBookLabs) on Twitter photo 2023-06-04 13:26:00 New IOC of #OceanLotus #APT discovered by our analyst. Keep tracking^
198[.]244[.]207[.]133
Check it out: threatbook.io/ip/198.244.207…
#ThreatHunting #ThreatIntelligence #threats #infosec #cybersecurity #cybercrime #SOC #CTI New IOC of #OceanLotus #APT discovered by our analyst. Keep tracking^
198[.]244[.]207[.]133
Check it out: threatbook.io/ip/198.244.207…
#ThreatHunting #ThreatIntelligence #threats #infosec #cybersecurity #cybercrime #SOC #CTI](https://pbs.twimg.com/media/Fxwv3EWaAAICEV2.jpg)






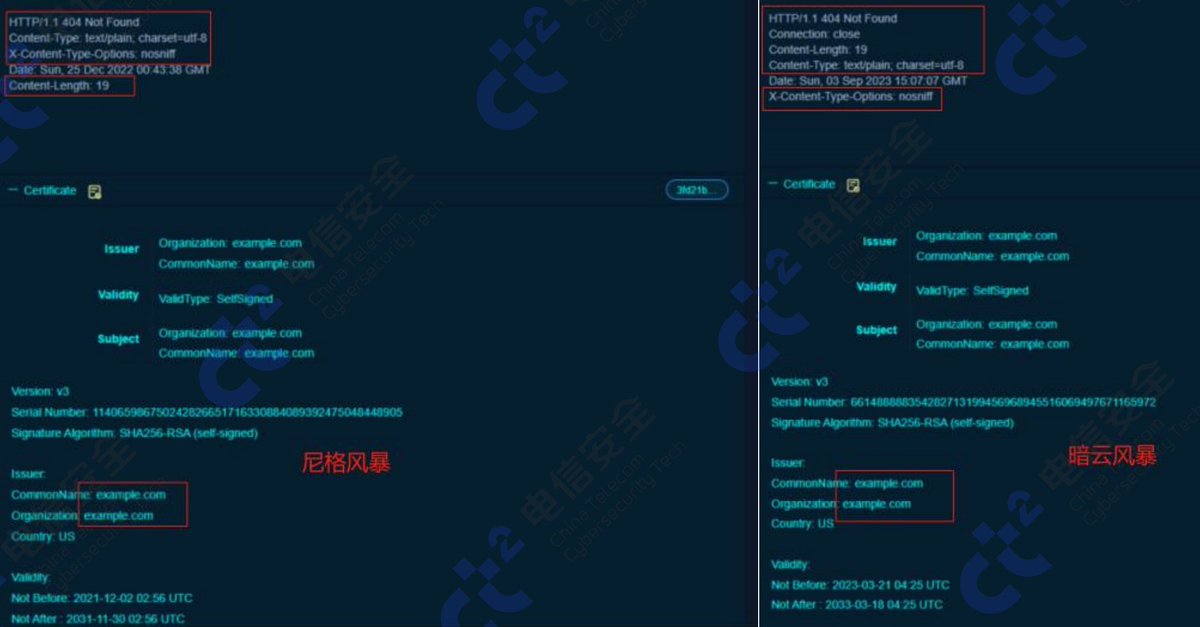
Extracting the #OceanLotus #APT32 VBA project from the Web Archive File using #CyberChef
Sample used: 3510590280406fa30eda94b3ae39058d
First we need to extract the ActiveMime (.mso) from the document. I've used Cerbero from Cerbero Labs and paste the Base64 string into CyberChef.


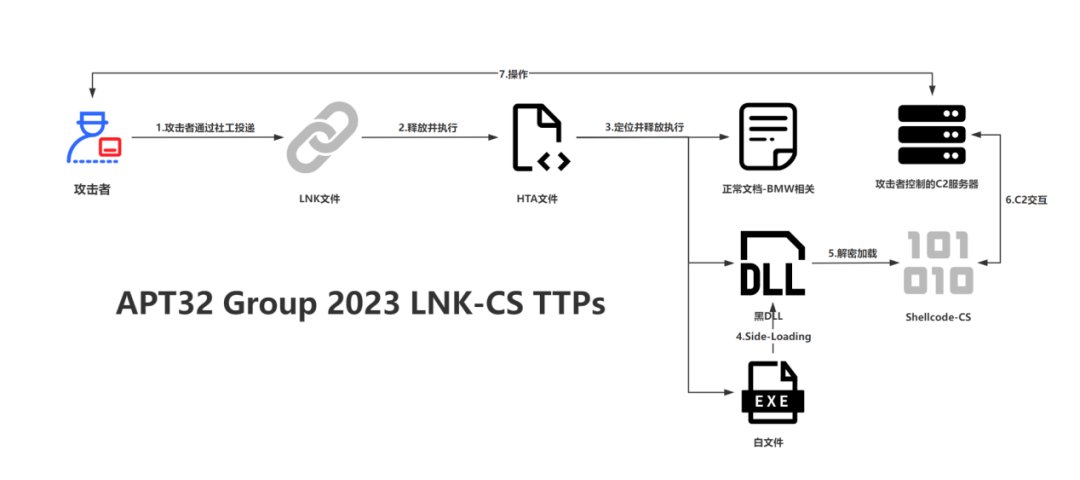
![Jazi (@h2jazi) on Twitter photo 2021-09-08 15:55:42 It looks like an old sample of #OceanLotus #APT has been submitted to VT today:
5b87ef34d174361f35b65c5ee684f1c3
2018年9月工作报告修改意见.doc
9b4c57e61f4df3b546aedf58b2f299cf
Log_Error.jpg
ristineho[.]com It looks like an old sample of #OceanLotus #APT has been submitted to VT today:
5b87ef34d174361f35b65c5ee684f1c3
2018年9月工作报告修改意见.doc
9b4c57e61f4df3b546aedf58b2f299cf
Log_Error.jpg
ristineho[.]com](https://pbs.twimg.com/media/E-xkGeEXMAETwMZ.jpg)