Found a bug on GitHub Security
Bug: Privilege escalation
Tip: Check each API endpoint
#bugbounty #pentesting #bugbounty tip #cybersecurity #hackerone #ethicalhacking #reports #bounty #bugbounty tips

Google Dorking with ease.
Dorki.io - dorki.io
#bugbounty #ethicalhacking #recon #osint #hackforgood #infosec


Did you know you can hack computers using your phone?
Full video: youtu.be/LjB5XN4awgk
#zsecurity #hacking #ethicalhacking #cybersecurity #Learnhacking #Learncybersecurity #starthacking

Add '.ftpconfig' to the wordlist, and maybe you will get juicy data. Enjoy!
#bugbountytip s #bugbountytip #cybersecurity #ethicalhacking


Last month, I found myself switching between targets frequently, making it difficult to concentrate.
However, in the last week revisited one program, where I found some access control issue.
Need to choose some good program this month.
#bugbounty #ethicalhacking

We strive to dispel myths and provide aspiring ethical hackers with the knowledge, skills, and guidance they need to succeed. ✨💫
Enrollment Opens Soon at the Cykea Ethical Hacking Academy 🎉
#ethicalhacking #CyberSecurity #myth



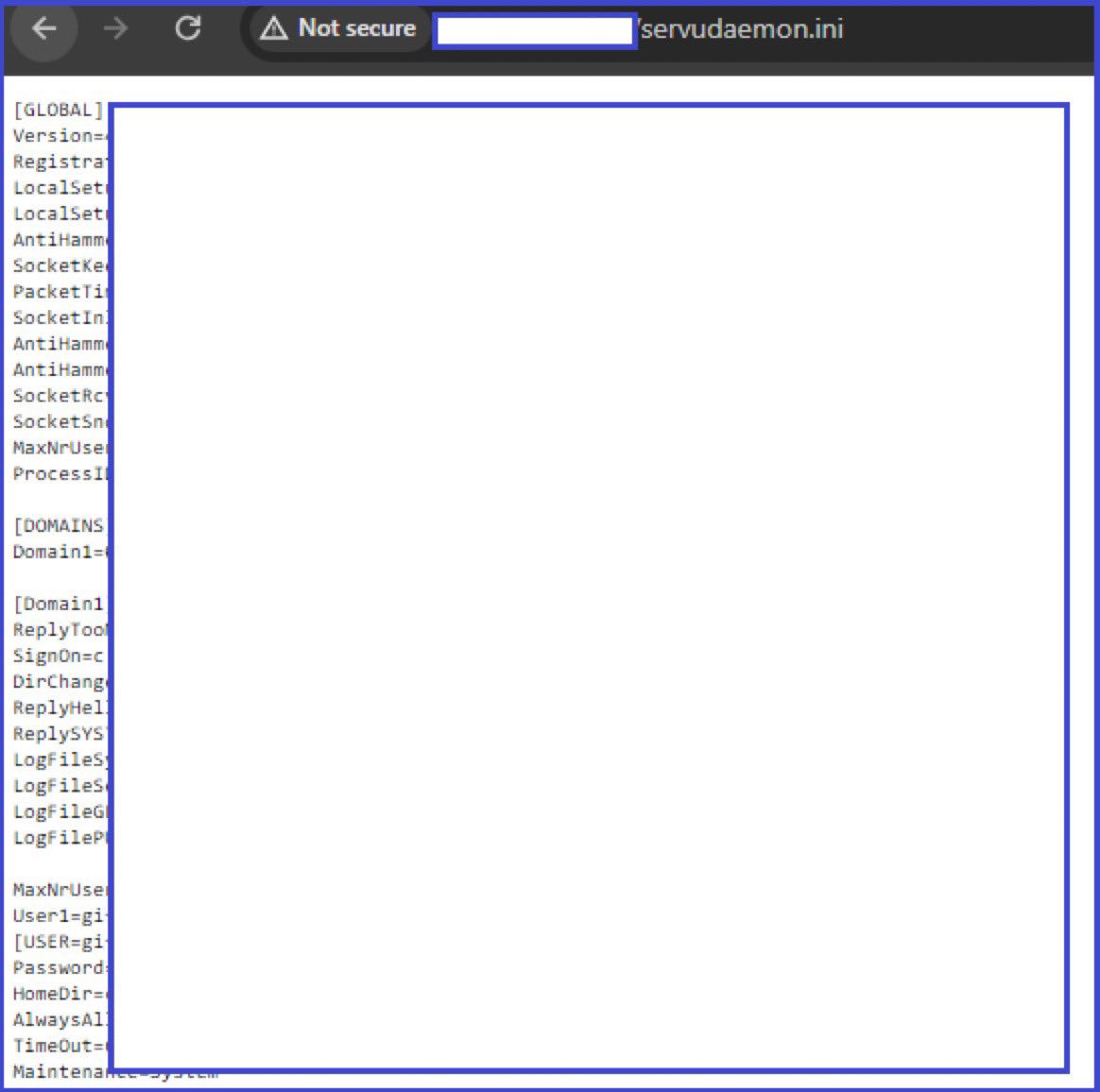
Add 'servudaemon.ini' to the wordlist, and maybe you will get juicy data. Enjoy! 😄
Created a nuclei template for it: github.com/NoRed0x/nored0… 🚀
credit: Karim Habeeb
#bugbountytips #cybersecurity #ethicalhacking 💻

As i said every day new feature is being deployed stay with us in this journey of making your Google dorking life easier #bugbounty #ethicalhacking #infosec

Biqudratillahi, the O-range tech hub is going to be one of the most visited centers to learn #cybersecurity and #ethicalhacking in Nigeria.
والله متم نوره ،ولو كره........🏌️
Yunus Oyetunde (Coy Emerald) 🇳🇬🇺🇦

DotGit Firefox extension could get you some serious P1/P2 vulnerabilities. 😱🔥 It's a must-have in your hacker toolkit. Easy bug bounty money! 💰💻
credit: Otterly
#bugbounty #cybersecuritytips #ethicalhacking 😎


Want to be a part of the World's No.1 #thicalhacking certification? Get the #CEH certification and join the ranks of successful professionals who have received promotions.
Learn more at buff.ly/4bphUEn
#certifiedethicalhacker #ethicalhacking #eccouncil


Add 'master.passwd/master.passwd.txt' to the wordlist, and you might uncover some juicy data. Enjoy! 😄💻🔍
credit: Karim Habeeb
#bugbountytips #cybersecurity #ethicalhacking


Mastering DevOps Engineering: A Comprehensive Guide to DevOps Engineer Masters Program
senacourse.blogspot.com/2024/05/master…
#DevOps #aws #hacked #snapchatsupport #gmailsupport #googleaccount #GMAILDOWN #NFT s #NFT #Bullish #ethicalhacking #digitalsecurity #hackingtools #CybersecurityNews

AI is revolutionizing ethical hacking by automating tasks, analyzing data, and identifying vulnerabilities faster than ever! 🚀 It’s like having a digital mentor that guides you through the complex cybersecurity landscape. #EthicalHacking #AI #CyberSecurity


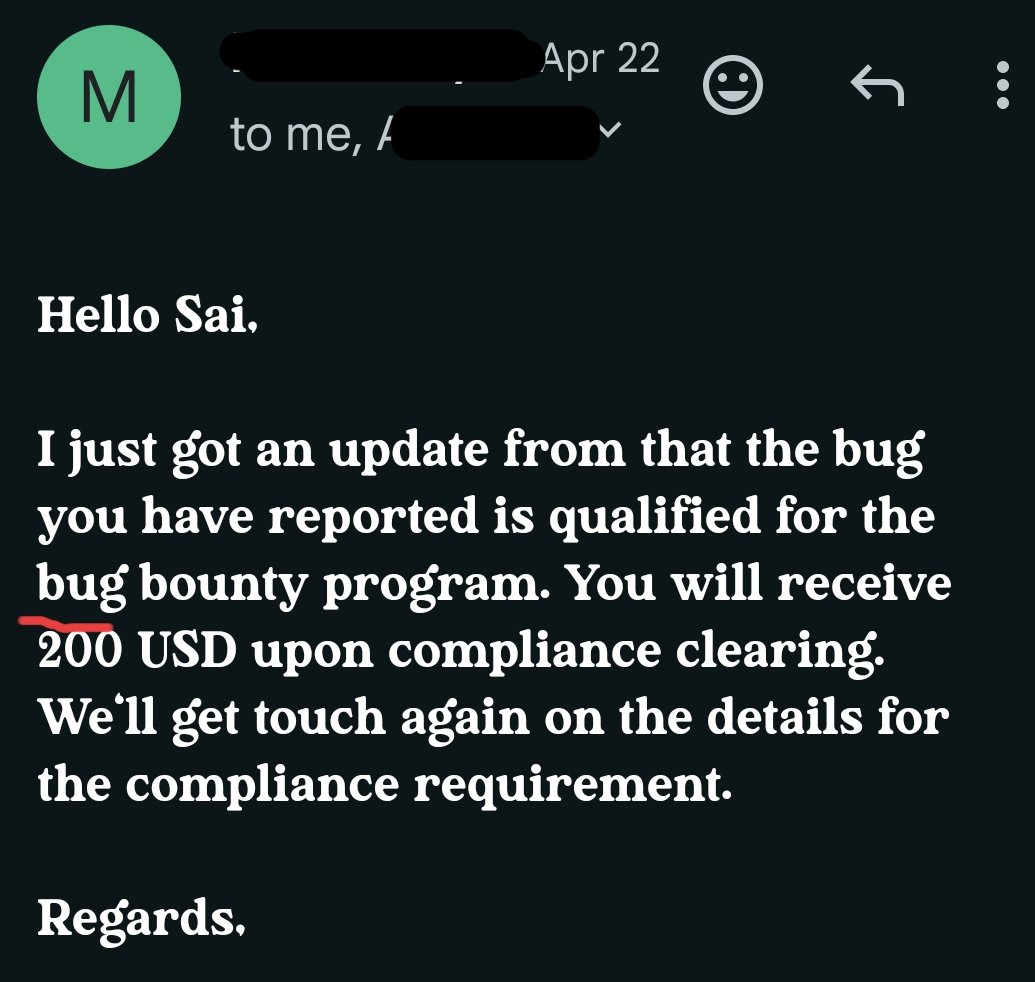
Jai shri Ram 🙏
got Bounty $$$
Thanks lord Krishna for this !
#BugBounty #SecurityVulnerabilities
#InfoSec #CyberSecurity #EthicalHacking #BugHunting #WhiteHat #server #unblock
#WebSecurity #HackerCommunity
#CyberAware

eJPT: Intermediate Level Ethical Hacking Certification
Watch full video at: youtu.be/pagn6Ppq3Ws
#Cybersec urity #Cybersec #InfoSec #PenetrationTesting #PenTesting #PenTester #Hacker #Hacking #EthicalHacker #EthicalHacking #eJPT

How to learn Cybersecurity | Ethical Hacking.
1. Learn the basics
2. Learn the 2nd basics
3. Learn tools used
4. Play around
5. Repeat Step 1 to 5.
#cybersecurity #ethicalhacker #ethicalhacking

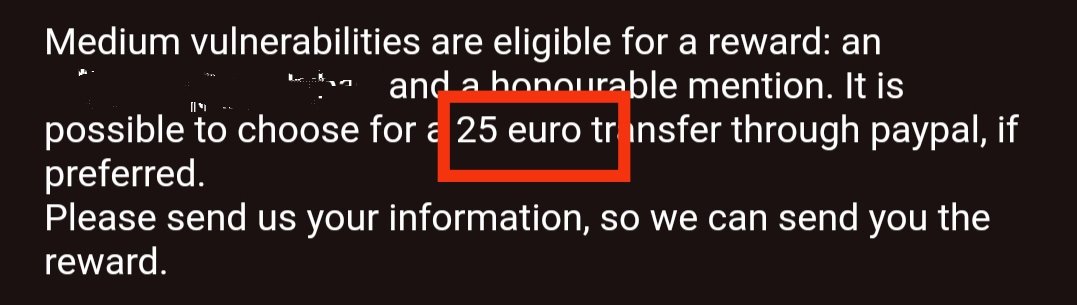
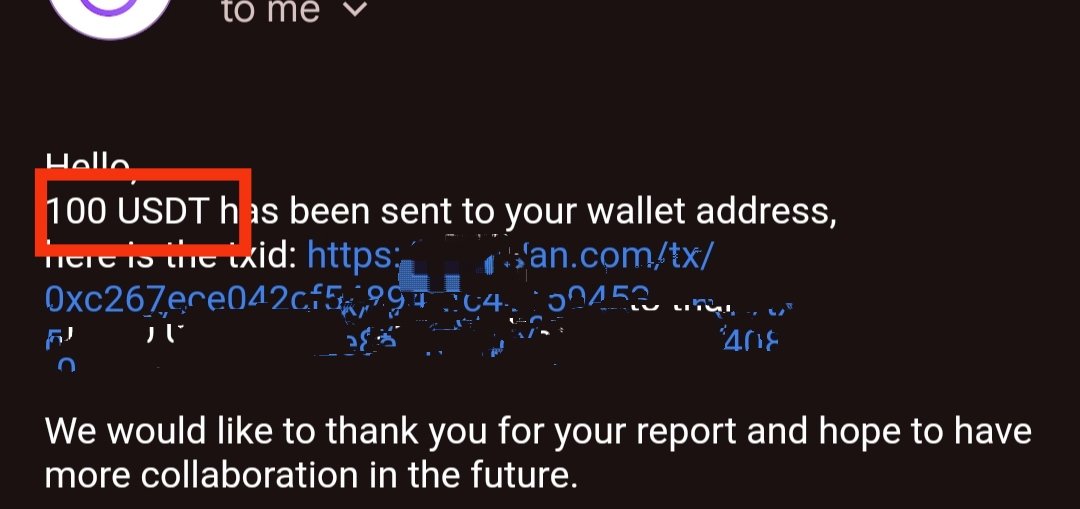
Jai shri Ram 🙏
got Bounty 75€
Thanks lord Krishna for this !
#BugBounty #SecurityVulnerabilities
#InfoSec #CyberSecurity #EthicalHacking
#BugHunting #WhiteHat #server #unblock #WebSecurity #HackerCommunity #CyberAware